Implementing Zero Trust in Cloud Environments
Understanding the Zero Trust Model
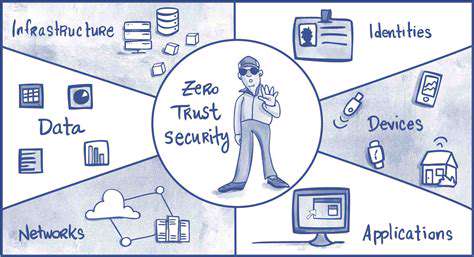
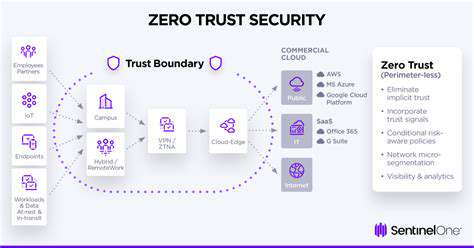
Zero Trust represents a security framework that operates on the assumption that no entity—whether user, device, or application—should be inherently trusted, even if it resides within a traditional network perimeter. This model demands constant validation and authorization for every access attempt, irrespective of origin or identity. It marks a radical departure from conventional security by shifting focus from network trust to universal verification. Deploying this framework in cloud settings necessitates a well-thought-out plan and a resilient security infrastructure.
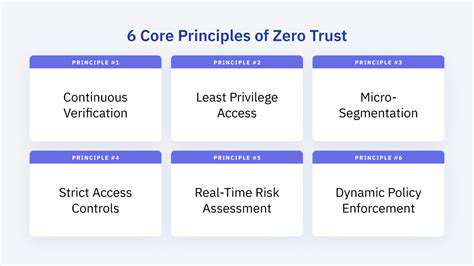
Central to this approach is the principle of least privilege. Every user, device, and application is restricted to the minimal access required, thereby reducing the potential fallout from a security breach. Such precise control is especially vital in cloud ecosystems, where resources are often dispersed and accessed from diverse locations.
Identifying and Verifying Identities
A cornerstone of Zero Trust in cloud environments lies in the precise identification and authentication of users and devices. This entails deploying multi-factor authentication (MFA) and stringent password protocols to ensure only legitimate entities gain entry. Innovative methods like biometric verification and contextual analysis can further bolster security measures.
Establishing a comprehensive identity and access management (IAM) system that seamlessly integrates with cloud services is critical. This system must dynamically oversee user roles, permissions, and access requests, adapting fluidly to evolving business requirements.
Micro-segmentation for Enhanced Security
Micro-segmentation stands as a pivotal strategy for applying Zero Trust principles in cloud environments. By dividing the cloud infrastructure into isolated segments, this technique confines the potential impact of a breach, hindering attackers from navigating the network freely and reaching sensitive data.
Creating these finely tuned security zones allows administrators to exert precise control over access to specific applications and resources. This method dovetails perfectly with the least privilege principle, ensuring only authorized entities interact with designated data and functionalities within the cloud.
Continuous Monitoring and Threat Detection
Adopting Zero Trust in cloud environments calls for an advanced monitoring and threat detection framework. This system must perpetually scrutinize user and device activities, flagging irregularities and suspicious patterns. Cutting-edge security information and event management (SIEM) tools are indispensable for real-time threat identification and response.
Data Loss Prevention (DLP) Measures
Data loss prevention (DLP) is a fundamental pillar of Zero Trust in cloud environments. Enforcing DLP protocols safeguards sensitive data, irrespective of its location or access method. This encompasses encrypting data both at rest and in transit, alongside stringent access controls to avert unauthorized exposure or alterations.
Enhancing Cloud Security Posture with Automation
Automation is instrumental in the effective deployment of Zero Trust in cloud environments. Automating security tasks—such as policy configuration, access control enforcement, and incident response—can markedly diminish human error and boost operational efficiency. This empowers security teams to concentrate on higher-level strategic initiatives.
Automation tools also facilitate ongoing evaluation of the cloud environment's security stance, proactively pinpointing and addressing vulnerabilities. This iterative enhancement cycle is essential for sustaining a robust Zero Trust security framework.
Regular Security Assessments and Audits
Conducting periodic security assessments and audits is vital for verifying the efficacy of Zero Trust implementation in cloud environments. These evaluations should scrutinize existing security controls, uncover vulnerabilities, and propose refinements. This practice ensures the security posture remains attuned to the ever-changing threat landscape.
Regular audits also aid in demonstrating compliance with industry regulations and standards, while establishing a baseline for future security improvements. This relentless pursuit of betterment is key to maintaining an agile and resilient security strategy.
Challenges and Considerations
Implementing Zero Trust in Existing Environments
Transitioning to a Zero Trust architecture within an established cloud infrastructure can pose formidable hurdles. Legacy systems and applications frequently lack the built-in security features requisite for a Zero Trust model. Upgrading these systems to align with Zero Trust tenets demands meticulous planning, potential redesign, and often substantial investment in new security solutions and staff training. This transition must be executed systematically, with each system evaluated individually to pinpoint vulnerabilities and determine the optimal approach for implementing granular access controls.
Granular Access Control and Micro-segmentation
At the heart of Zero Trust lies granular access control, which entails rigorously defining and restricting resource access based on strict necessity. Micro-segmentation is integral to this, involving the subdivision of the network into isolated segments to impede lateral threat movement. This necessitates meticulous network design and the deployment of tools capable of efficiently tracking and managing access permissions across these segments.
Balancing Security with User Experience
Zero Trust security measures can occasionally result in a less intuitive user experience. Users may face additional authentication steps or restrictions compared to traditional models. Striking a harmonious balance between robust security and seamless usability is paramount. This may involve simplifying authentication processes, offering clear user guidance, and proactively addressing any friction points.
Security Tool Integration and Management
Zero Trust often requires the integration of multiple security tools, including identity and access management (IAM) systems, network security appliances, and threat detection and response (EDR) solutions. Effective management and coordination of these tools are crucial for maintaining a comprehensive security posture. Ensuring interoperability among these tools is essential to prevent data silos and enable efficient information sharing across the security ecosystem.
Compliance and Auditing Considerations
Zero Trust implementations must be thoroughly documented and audited to comply with industry regulations and internal policies. This demands robust logging and reporting mechanisms to track user activities, access requests, and potential breaches. Clear audit trails are indispensable for demonstrating adherence to security standards and facilitating incident response. This aspect is critical for maintaining trust with regulatory bodies and partners.
Cost Implications and ROI
Deploying Zero Trust solutions can involve substantial initial costs, including new security tools, staff training, and potential infrastructure upgrades. A thorough cost-benefit analysis is essential to evaluate the return on investment (ROI) by weighing the risks mitigated, potential financial losses averted, and operational efficiencies gained. Such analysis is vital for justifying the investment in a Zero Trust architecture.
Maintaining a Dynamic Security Posture
Cloud environments are in a constant state of flux, with new applications, services, and users being added regularly. A Zero Trust approach must be flexible enough to adapt to these changes. This requires ongoing monitoring, analysis, and updates to security policies and configurations to maintain a dynamic security posture capable of addressing emerging threats and evolving business needs. Security teams must be prepared to refine their strategies as the cloud environment grows and transforms.