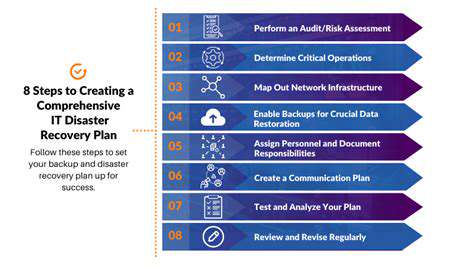
The future of cybersecurity lies in AI-powered predictive defense. By leveraging machine learning and artificial intelligence, organizations can develop systems that anticipate and mitigate threats before they occur. This proactive approach to security will require a shift in mindset from simply reacting to threats to actively preventing them. The ability to predict and prevent attacks will be crucial in a future where threats continue to evolve at an unprecedented pace. This approach involves a continuous learning process, adapting to new attack vectors and enhancing the accuracy of predictive models.
Selecting the appropriate flooring for your furry friend is crucial for their comfort, safety, and overall well-being. Different pets have different needs, and what works for one might not be suitable for another. Consider your pet's size, activity level, and potential for destructive chewing when making your decision. For example, a high-energy dog might need a durable, non-slip surface to prevent slips and falls, while a kitten might benefit from a soft, easily cleaned surface.
The Future of Cybersecurity Anomaly Detection with Machine Learning
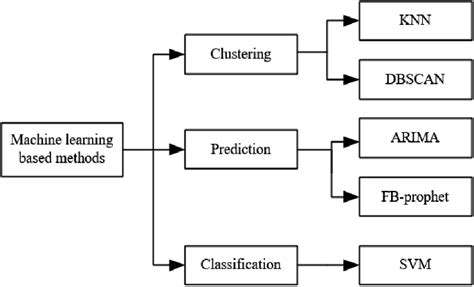
Machine Learning's Growing Role in Anomaly Detection
Machine learning (ML) is rapidly transforming the landscape of cybersecurity anomaly detection. Traditional methods often rely on predefined rules, making them vulnerable to evolving threats. ML algorithms, however, learn from vast datasets of normal and anomalous network activity, enabling them to identify subtle patterns and deviations that might be missed by static rule-based systems. This adaptive learning capability is crucial in combating the ever-increasing sophistication of cyberattacks.
Beyond Signature-Based Detection: Predictive Capabilities
While signature-based detection methods are valuable for known threats, they struggle with zero-day attacks and evolving malware. ML-powered anomaly detection systems go beyond simply identifying known patterns; they can predict potential threats by analyzing complex relationships within network traffic. This predictive capability allows security teams to proactively identify and respond to emerging threats before they cause significant damage.
Deep Learning for Enhanced Accuracy and Scalability
Deep learning, a subset of machine learning, offers even greater potential for accuracy and scalability in anomaly detection. Deep learning models, with their ability to extract intricate features from complex data, can identify more subtle and nuanced anomalies compared to simpler algorithms. This enhanced accuracy translates to fewer false positives, allowing security teams to focus on genuine threats without wasting resources on irrelevant alerts.
The Importance of Feature Engineering
The effectiveness of any ML-based anomaly detection system hinges on the quality and relevance of the data features used for training. Properly engineered features – representing key aspects of network activity, user behavior, and system logs – are critical for accurate model training. Carefully selecting and transforming these features can significantly improve the model's ability to distinguish between normal and malicious activities.
Handling Big Data Challenges
Modern cybersecurity environments generate massive volumes of data. ML algorithms need to be robust enough to process and analyze this big data effectively. Efficient data preprocessing techniques and distributed computing frameworks are essential to ensure that the models can handle the scale of data without sacrificing performance and accuracy. This is critical for maintaining the responsiveness and effectiveness of the system.
The Need for Continuous Learning and Adaptation
Cyber threats are constantly evolving, demanding that anomaly detection systems adapt and learn continuously. ML models require regular retraining using updated datasets to maintain their effectiveness against new attack vectors and tactics. This continuous learning and adaptation is essential for staying ahead of cybercriminals and ensuring ongoing protection against evolving threats. Regular updates and fine-tuning are key to staying ahead of the curve.
Ethical Considerations in ML-Based Security
While ML offers significant advantages in cybersecurity, ethical considerations are paramount. Bias in training data can lead to unfair or inaccurate detection of anomalies, potentially impacting specific user groups or organizations. Careful attention to data diversity, fairness, and transparency is essential to building responsible and equitable ML-based security systems. This crucial aspect of responsible AI implementation must be considered at every stage of development.