Identifying Potential Internal Threats
Internal supply chain vulnerabilities often originate from unintentional process gaps rather than malicious intent. A well-meaning manager overriding safety protocols to meet quotas can create more systemic risk than a disgruntled employee. The most effective controls address both human psychology and technical safeguards, recognizing that people will always find workarounds to cumbersome systems.
Access management requires nuanced approaches beyond simple permission levels. Context-aware systems that adjust privileges based on multiple factors (location, device, time) provide better security than static role-based controls. Regular access reviews should examine not just who has permissions but whether they still need them for current responsibilities.
Assessing External Threats
External risk assessment has evolved from checking supplier financials to analyzing their cybersecurity posture and climate change exposure. The most thorough evaluations now consider multi-tier supplier relationships - your second-tier chip manufacturer's water source matters as much as your primary vendor's delivery performance. Traditional risk matrices struggle to capture these complex interdependencies.
Forward-looking organizations supplement traditional assessments with predictive analytics. By combining supplier data with geopolitical indicators, weather patterns, and even social media sentiment, companies can identify brewing problems long before they appear on standard risk dashboards. This early warning capability separates reactive from proactive supply chains.
Analyzing Emerging Threats and Trends
The next wave of supply chain disruptions will likely come from unexpected intersections of technology and regulation. Consider how evolving data privacy laws might impact IoT device tracking across borders, or how carbon accounting requirements could reshape supplier selection criteria. Truly strategic risk management anticipates these convergences before they become crises.
Scenario planning exercises that bring together experts from diverse fields (technology, law, environmental science) yield the most robust preparedness. These sessions should deliberately challenge conventional wisdom - if everyone agrees a risk is improbable, that's precisely when complacency becomes dangerous.
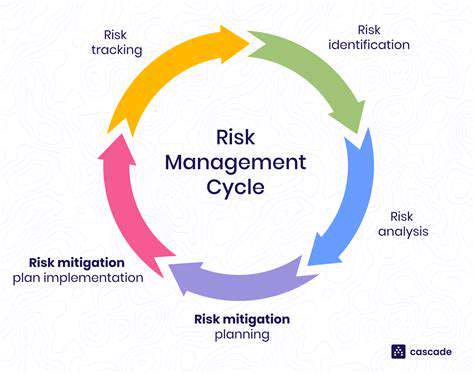
Implementing and Monitoring Risk Assessment Processes
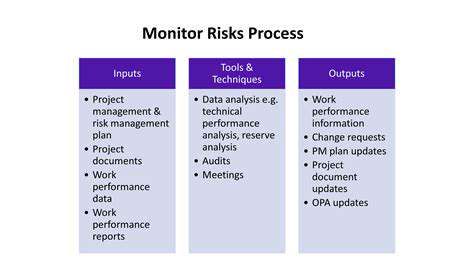
Understanding Risk Assessment
A modern risk assessment framework must balance quantitative data with qualitative insights. While metrics provide objective benchmarks, the most revealing information often comes from employee interviews and process observations. This blended approach captures both measurable risks and subtle cultural factors that data alone might miss.
The most effective assessments consider not just immediate impacts but second- and third-order effects. A transportation delay doesn't just affect inventory - it can trigger customer contract penalties, reputational damage, and employee overtime costs that compound the original disruption.
Defining Risk Tolerance
Risk appetite statements often fail when they're too generic. We accept moderate risk means nothing without context. Effective tolerance definitions specify acceptable thresholds for different risk categories - perhaps accepting higher financial volatility than quality variation. These differentiated guidelines make decision-making clearer when trade-offs are necessary.
The best tolerance frameworks include escalation protocols, specifying exactly when and how to elevate risk decisions. This prevents middle managers from gambling with unacceptable risks or executives from micromanaging trivial concerns.
Identifying Potential Risks
Traditional risk identification often focuses too narrowly on operational issues. Truly comprehensive exercises should also examine strategic risks like business model obsolescence and innovation risks like failing to adopt emerging technologies. The most forward-thinking companies even assess success risks - how rapid growth could strain quality controls or corporate culture.
Creative risk identification techniques like pre-mortems (imagining future failures to uncover current vulnerabilities) often reveal blind spots in conventional approaches. These exercises work best when they include voices from across the organizational hierarchy.
Analyzing Risk Likelihood and Impact
Probability assessments frequently suffer from recency bias - overestimating risks from recent events while discounting less memorable but equally dangerous scenarios. Sophisticated analyses use historical data to counterbalance these cognitive biases. Impact assessments similarly benefit from examining parallel cases in other industries facing comparable challenges.
The most valuable analyses distinguish between controllable and uncontrollable factors. This distinction guides where to invest mitigation efforts versus where to build resilience against inevitable shocks.
Developing Mitigation Strategies
Effective mitigation moves beyond generic reduce risk statements to specific action plans. For each major risk, there should be clear ownership, timelines, and success metrics. The best strategies combine preventive controls with detection mechanisms and response protocols - recognizing that some risks will materialize despite best efforts.
Innovative companies now design fail-safe rather than fail-secure systems - when controls break down, they fail in ways that minimize damage rather than creating new problems. This philosophy transforms risk management from obstacle to enabler.
Monitoring and Evaluating Risk Responses
Static risk registers quickly become outdated. Dynamic monitoring systems automatically update risk profiles based on changing internal and external conditions. These systems flag when previously minor risks cross established thresholds, preventing nasty surprises.
The most insightful evaluations compare predicted versus actual risk outcomes, continuously improving the organization's risk prediction capabilities. This feedback loop turns risk management into a learning system that gets smarter with each cycle.
Continuous Improvement and Adaptation: Staying Ahead of the Curve
Adapting to Evolving Market Demands
Market-responsive supply chains don't just react to changes - they anticipate them. The most advanced organizations employ sense-and-respond systems that detect demand shifts in real time through point-of-sale data, social media trends, and even weather forecasts. This predictive capability allows inventory adjustments before traditional indicators signal the need.
Flexibility must extend beyond operations to organizational structures. Teams structured around fixed product lines struggle when demand patterns shift. Agile organizations use cross-functional swarm teams that rapidly reconfigure based on evolving priorities.
Embracing Technological Advancements
Technology adoption decisions now carry significant risk implications. Implementing the wrong system can create more vulnerabilities than it solves. Wise organizations pilot new technologies in controlled environments while maintaining legacy capabilities during transition periods. This balanced approach captures innovation benefits without unacceptable disruption risks.
The most effective digital transformations focus first on data quality rather than flashy analytics. Clean, well-organized operational data enables all subsequent technology benefits while poor data undermines even the most sophisticated tools.
Building Robust Supplier Relationships
Traditional supplier management focused on cost negotiation. Modern approaches emphasize joint capability building. Leading companies invest in supplier development programs that strengthen the entire ecosystem's resilience. These partnerships pay dividends when crises hit, as collaboratively developed contingency plans execute more smoothly than imposed requirements.
The deepest supplier relationships include regular stress tests of mutual capabilities, identifying improvement opportunities before emergencies reveal weaknesses. These exercises build trust while hardening the supply chain against real disruptions.
Proactive Risk Management Strategies
Beyond preparing for known risks, resilient organizations practice black swan preparedness. These extreme-but-plausible scenarios reveal hidden vulnerabilities in conventional plans. The most valuable exercises simulate multiple simultaneous disruptions - how would a cyberattack during a natural disaster with key personnel unavailable play out?
Creative risk financing strategies also differentiate mature programs. Alternative approaches like parametric insurance (payouts triggered by objective metrics rather than loss assessments) can provide faster recovery from certain disruptions.
Implementing Continuous Monitoring and Evaluation
The most effective monitoring goes beyond tracking KPIs to analyzing their leading indicators. Rather than just measuring on-time deliveries, advanced systems monitor the precursors to delays - supplier production rates, transportation bottlenecks, quality rejection rates. This shift from lagging to leading indicators creates time to intervene before problems occur.
Evaluation processes should examine both successes and failures with equal rigor. Near-misses and avoided crises often contain the most valuable lessons for preventing future incidents. Creating a culture that celebrates identifying these learning opportunities is as important as the technical monitoring systems themselves.