Recognizing Potential Vulnerabilities
The initial phase in developing a resilient continuity plan involves thorough vulnerability identification, particularly concerning ransomware threats. This requires complete evaluation of organizational weaknesses, examining elements like obsolete systems, insecure credentials, insufficient security measures, and human error possibilities. Detailed examination of recent cyber extortion patterns and attack methods helps identify probable threats. This anticipatory method enables creation of specific countermeasures rather than reactive responses after incidents occur.
Beyond digital extortion, consider broader operational disruptions. Natural catastrophes, electrical failures, and supply chain breakdowns can all severely affect business functions. Comprehensive risk analysis should encompass all potential threats and their possible effects on critical operations.
Creating Restoration Protocols
Following threat identification, establishing detailed recovery procedures becomes critical. These should specify organizational responses to ransomware incidents or other major disruptions, detailing steps from initial detection through full operational restoration. This includes specific methods for isolating infected networks, halting malware spread, and retrieving data from backups. Comprehensive documentation ensures all personnel understand their crisis roles and responsibilities.
Recovery protocols must also address reinstatement of essential operations. This involves outlining steps for reactivating affected systems, restoring information, and resuming normal activities. Here, a well-structured backup and restoration strategy becomes paramount. Regular protocol testing verifies effectiveness and execution efficiency during actual incidents.
Designing Communication Strategies
Effective information dissemination proves crucial during ransomware incidents or operational crises. A clearly defined communication strategy ensures all stakeholders - employees, clients, and regulators - receive timely, accurate updates. This plan should specify communication channels, designated spokespeople, and information release schedules. Transparent, prompt communication maintains trust and reduces potential reputational harm.
The communication framework should accommodate various scenarios, such as notifying clients about service interruptions or updating stakeholders on recovery progress. A thorough communication approach benefits both internal operations and external relations, protecting brand integrity and demonstrating crisis management capabilities.
Executing and Maintaining the Strategy
An effective continuity plan requires ongoing refinement, testing, and updating. Regularly review and adjust the plan to address emerging threats and operational changes. Conduct periodic tests to verify procedure effectiveness and team preparedness, including simulated ransomware attacks to evaluate response capabilities and identify improvement areas. Employee training and active participation ensure successful implementation and maintenance.
Ensure plan accessibility to all relevant personnel with clear understanding of individual responsibilities. Updates based on exercise lessons or actual incidents maintain plan effectiveness and organizational readiness. This proactive approach enhances recovery capabilities and minimizes operational disruption impacts.
Implementing Data Protection and Restoration Methods
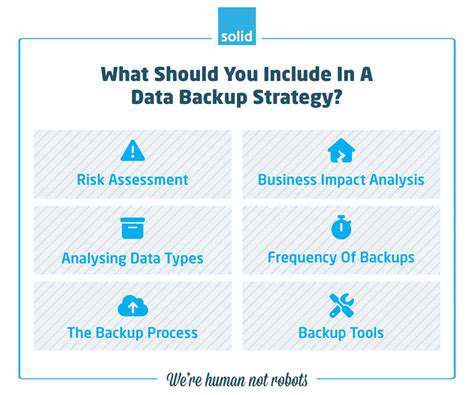
Preparing for Information Loss Prevention
The foundation of any effective data protection strategy begins with meticulous preparation. This process involves cataloging all critical information sources, understanding their usage patterns and organizational importance, and evaluating potential data loss risks. Comprehensive documentation of existing data structures proves essential for successful planning. Details should include storage locations, access permissions, and data classifications.
A well-designed emergency recovery blueprint should outline necessary steps to reinstate critical systems following failures. This document must account for various scenarios including equipment malfunctions, natural disasters, and malicious intrusions. Thorough preparation enables proactive risk mitigation and ensures efficient recovery processes. Regular testing identifies improvement areas and verifies plan effectiveness.
Selecting Appropriate Protection Solutions
Choosing suitable data protection methods is crucial for maintaining information integrity and availability. Available solutions range from basic file backups to sophisticated cloud-based systems, catering to diverse requirements and budgets. Consider data volume, storage needs, recovery time expectations, and financial constraints when evaluating options. Combining multiple solutions often provides comprehensive protection.
Selected solutions should integrate smoothly with existing infrastructure to minimize implementation disruptions. Seamless integration ensures compatibility with current workflows and reduces operational interference. Extensive testing in controlled environments before deployment verifies solution reliability and effectiveness, allowing for necessary adjustments.
Ensuring Effective Restoration Processes
Developing clear, detailed restoration procedures is fundamental to successful emergency recovery. These should specify response steps during recovery events, defining participant roles and responsibilities. Regular procedure testing maintains plan relevance and effectiveness while identifying potential gaps. Comprehensive documentation reduces confusion and ensures efficient crisis response.
Implement data verification processes post-recovery to validate information completeness and accuracy. Rigorous verification ensures restored data integrity, enabling swift operational resumption. This critical step guarantees restored information usability and functionality.
Emergency Recovery and Operational Restoration Processes
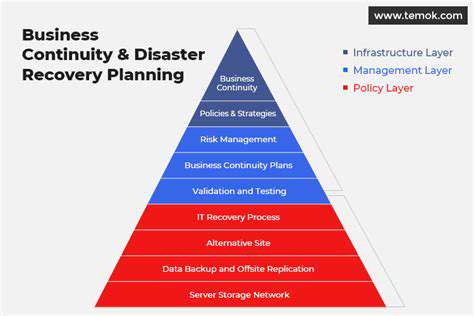
Emergency Recovery Planning: Essential Business Continuity Component
Effective emergency recovery planning is crucial for all organizations. Beyond data retrieval, it ensures complete operational restoration following disruptive events. A well-structured plan minimizes downtime, reduces financial impact, and protects corporate reputation. This proactive approach safeguards valuable assets including sensitive information and critical infrastructure.
Emergency recovery planning extends beyond simple backups. It involves risk identification, mitigation strategy development, and detailed operational restoration procedures. A comprehensive plan addresses multiple aspects from critical system identification to communication protocol establishment and recovery process testing.
Data Protection and Restoration Approaches
Robust data protection strategies form the foundation of emergency recovery. Regular offsite backups ensure information redundancy and reduce localized disaster risks. Appropriate technology selection and tested restoration processes enable swift operational recovery.
Regular backup system testing and validation ensures effectiveness. This includes verifying rapid, accurate data restoration capabilities. Thorough testing identifies weaknesses and allows necessary strategy adjustments.
Identifying Critical Operational Functions
Recognizing essential business operations is vital for emergency recovery planning. This involves evaluating core processes from order processing to client support. Understanding which functions are most critical helps prioritize recovery efforts.
Recognizing operational interdependencies is equally important. Disruptions in one area can create cascading effects throughout the organization. This understanding is key for developing comprehensive recovery strategies.
Establishing Communication Frameworks
Clear communication protocols during emergencies are essential. This includes identifying primary and secondary communication channels such as telephone systems, email, and messaging platforms. These protocols ensure stakeholder awareness and recovery coordination.
Effective communication reduces confusion and enables organized responses. Regular protocol testing ensures continued effectiveness across various emergency scenarios.
Developing Restoration Procedures
Detailed restoration procedures are vital for successful emergency recovery. These should outline steps for system and operational restoration from data recovery to facility reactivation. These procedures require clear documentation and easy accessibility for relevant personnel.
Plan Testing and Validation
Regular emergency plan testing and validation is crucial. This includes conducting simulated exercises to verify plan practicality. Thorough testing identifies weaknesses and ensures efficient recovery processes.
Recovery Time Targets and Data Loss Thresholds
Defining clear Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) helps prioritize resources and set achievable goals. RTO determines maximum acceptable system restoration time, while RPO defines maximum acceptable data loss. Well-defined objectives focus recovery efforts and measure plan success.