Leveraging Security Tools and Technologies
Identifying Potential Vulnerabilities
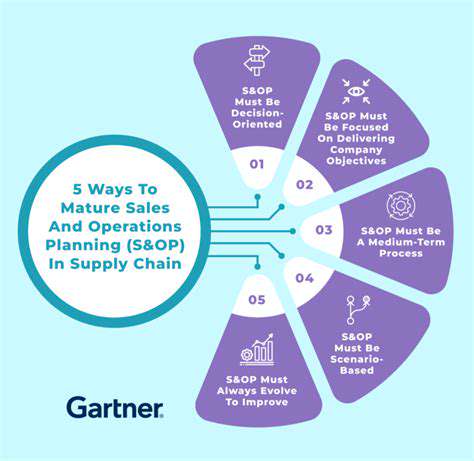
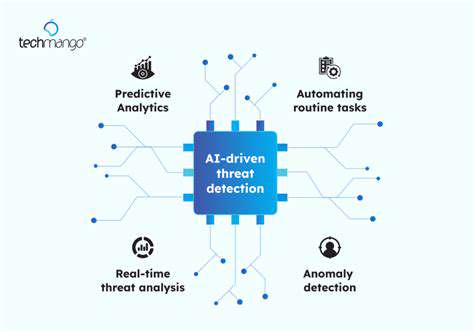
Securing the software supply chain demands vigilance at every stage - from development and testing to deployment. The most effective strategy involves hunting for weaknesses before they become threats. Teams must deploy a mix of automated scanners and human expertise to evaluate every component's security. This means examining not just the core code but also third-party libraries that could introduce hidden risks.
Advanced code analysis tools provide deeper inspection than basic scans, using static analysis to uncover logic flaws that might escape notice. Security professionals must understand how vulnerabilities manifest differently across programming languages. Regular penetration testing takes this further, simulating real attacks to expose weaknesses in both code and system architecture.
Implementing Robust Security Measures
Finding vulnerabilities is only half the battle - the real work begins with implementing solutions. Organizations need comprehensive security policies that cover every phase of development. These guidelines should dictate everything from which third-party components to use, to how teams write and test their code. Consistent enforcement of these standards separates effective security programs from mere checklists.
Developer education forms the foundation of secure software. Training should cover secure frameworks, proper data handling, and common coding pitfalls. But knowledge alone isn't enough - rigorous testing at multiple development stages validates whether security measures actually work. Penetration tests and security audits provide this critical verification.
The cybersecurity landscape never stands still, so neither can defense strategies. Regular updates for all tools and frameworks maintain protection against emerging threats. This requires an ongoing commitment to improvement as new vulnerabilities and attack methods surface.
Security succeeds through collaboration. Clear communication channels between developers, security teams, and vendors ensure quick identification and resolution of issues. When everyone shares responsibility for security, the entire development lifecycle becomes more resilient.

Continuous Monitoring and Improvement

Continuous Monitoring for Enhanced Performance
Performance improvement requires constant vigilance. By systematically tracking key metrics, organizations can spot trends, identify problems early, and optimize outcomes. This forward-looking approach prevents minor issues from becoming major disruptions while boosting overall efficiency.
Regular performance monitoring transforms guesswork into data-driven decisions. The insights gained allow for precise adjustments that maximize results while minimizing wasted effort.
Identifying Bottlenecks and Inefficiencies
Ongoing monitoring shines brightest when revealing workflow obstacles. Whether it's delayed tasks, underused resources, or needless complexity, tracking performance exposes these issues clearly. Addressing these choke points directly leads to smoother operations.
Solutions tailored to specific bottlenecks create more streamlined processes. This focused improvement reduces delays and enhances productivity throughout the organization.
Proactive Problem Resolution
Catching problems early defines successful monitoring programs. When metrics deviate from expectations, teams can intervene immediately - often before users notice any impact. This proactive stance keeps operations running smoothly.
Early detection dramatically reduces downtime and operational headaches. Maintaining performance levels requires this preventative approach rather than reactive firefighting.
Predictive Analytics for Future Optimization
Historical performance data becomes more valuable over time. Analyzing trends allows organizations to forecast needs and adjust strategies preemptively. This forward planning optimizes resource use and prepares for future challenges.
Adapting to Changing Market Demands
Business environments evolve constantly. Continuous monitoring of market trends and customer behavior helps organizations pivot effectively. Staying attuned to these shifts ensures continued relevance and competitiveness.
Improved Communication and Collaboration
Shared performance data creates common understanding across teams. Visualizations and reports align everyone on priorities and progress. This transparency fosters cooperative problem-solving and process optimization.
When all teams work from the same performance data, coordinated improvement becomes natural. The entire organization moves toward shared objectives more effectively.
Employee Engagement and Motivation
Visibility into individual and team performance can energize an organization. When employees see how their contributions matter, engagement naturally increases. Recognizing achievements reinforces positive behaviors and outcomes.
Performance transparency builds trust and motivation at all levels. This creates a virtuous cycle where engaged employees drive better results, which in turn boosts morale further.