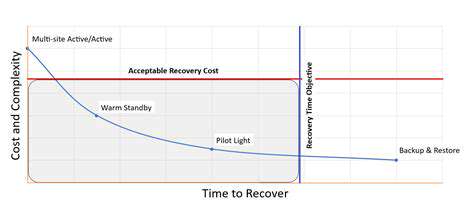
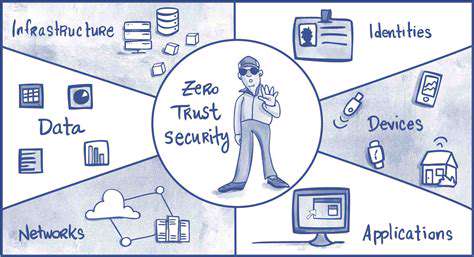
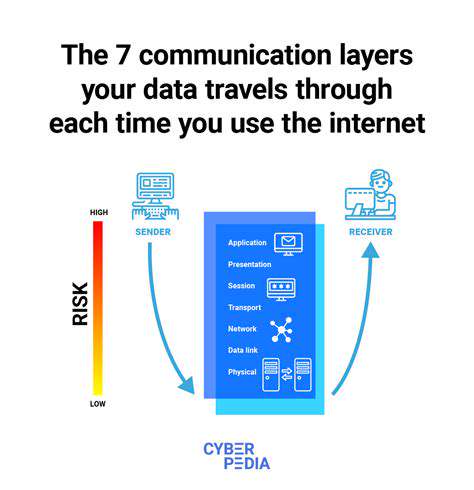
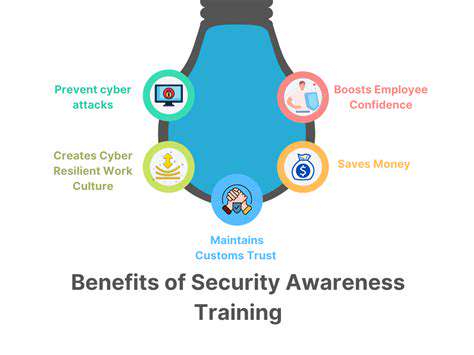
Introduction to AI in Vulnerability Management
Understanding the Role of AI in Vulnerability Management
Artificial intelligence (AI) is rapidly transforming various sectors, and vulnerability management is no exception. AI-powered tools and strategies offer a significant boost in identifying, analyzing, and mitigating vulnerabilities in systems and applications. This enhanced efficiency allows organizations to respond more swiftly to emerging threats, reducing the potential for costly security breaches and downtime.
AI's ability to process vast amounts of data, identify patterns, and learn from past incidents provides a crucial advantage over traditional methods. This analytical power enables AI to pinpoint vulnerabilities that might be missed by human analysts, leading to a more comprehensive and effective vulnerability management process.
Identifying Vulnerabilities with AI-Driven Analysis
AI algorithms excel at analyzing vast datasets of security logs, network traffic, and code repositories to identify potential vulnerabilities. This automated analysis process significantly speeds up the vulnerability discovery phase, allowing organizations to address threats more proactively. Sophisticated AI models can recognize subtle anomalies and patterns indicative of vulnerabilities, often before they are exploited by malicious actors.
Prioritizing Vulnerabilities for Effective Remediation
AI can significantly enhance vulnerability prioritization by considering factors such as exploitability, potential impact, and the criticality of affected systems. This prioritization ensures that resources are allocated effectively, focusing on the most critical vulnerabilities that pose the greatest risk. This targeted approach minimizes the risk of overlooking high-impact vulnerabilities while optimizing remediation efforts.
By assessing the likelihood of exploitation and the potential damage, AI-powered tools can help prioritize vulnerabilities, allowing security teams to focus on the most pressing issues first.
Automating Vulnerability Remediation Processes
AI can automate many aspects of the vulnerability remediation process, such as patching, configuration changes, and security updates. This automation significantly reduces the time and effort required for remediation, enabling organizations to respond to threats more rapidly. AI-driven automation streamlines the entire remediation pipeline, from identification to resolution, resulting in a more efficient and effective security posture.
Improving Security Incident Response with AI
AI-powered tools can play a critical role in security incident response by automating threat detection, analysis, and response. This automation allows organizations to react to incidents faster, minimizing the potential damage and fallout. AI's ability to learn from past incidents improves the accuracy and efficiency of future responses, creating a more resilient security posture.
By analyzing historical data and current events, AI-powered systems can identify emerging threats and provide recommendations for mitigation strategies, improving the effectiveness of incident response teams.
Predictive Modeling for Proactive Vulnerability Management
AI's predictive capabilities allow organizations to anticipate and proactively mitigate vulnerabilities before they are exploited. By analyzing trends, historical data, and emerging threats, AI can predict potential vulnerabilities and suggest preventive measures. This proactive approach allows for a more robust and preventative security posture, reducing the risk of future breaches.
Predictive modeling using AI empowers organizations to anticipate future threats, proactively implementing measures to prevent potential vulnerabilities before they materialize, thereby strengthening overall security posture.
The Future of AI in Vulnerability Management
The future of AI in vulnerability management is bright, with ongoing advancements promising even greater capabilities. As AI technology continues to evolve, we can expect more sophisticated and integrated solutions that seamlessly integrate into existing security infrastructures. The potential for AI to automate complex tasks, anticipate emerging threats, and personalize security measures will shape the future of cybersecurity.
Future advancements in AI will likely lead to more sophisticated predictive models, allowing organizations to anticipate and mitigate vulnerabilities with even greater precision and efficiency, creating a more dynamic and proactive security landscape.
Prioritizing Vulnerabilities Based on Risk
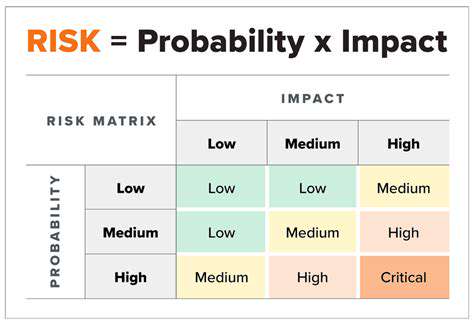
Prioritizing vulnerabilities in software development is crucial for maintaining system security and preventing potential breaches.
Effective vulnerability prioritization ensures that the most critical security flaws are addressed first, minimizing the risk of exploitation and maximizing the impact of security efforts. This proactive approach focuses on vulnerabilities that pose the greatest immediate threat to the system or data, allowing for a targeted and efficient allocation of resources to remediation efforts.
Understanding the Severity of Vulnerabilities
A comprehensive understanding of vulnerability severity is fundamental to effective prioritization. Factors such as the potential impact of exploitation, the likelihood of exploitation, and the exploitability of the vulnerability itself must be assessed. Quantitative metrics and qualitative assessments can be integrated to provide a holistic view of the risk posed by each vulnerability.
Identifying Critical Vulnerabilities
Identifying critical vulnerabilities necessitates a thorough analysis of the system's architecture, functionalities, and dependencies. This includes examining code, configurations, and third-party components to pinpoint potential weaknesses. A systematic approach, incorporating security testing methodologies like penetration testing, can significantly aid in the identification of critical vulnerabilities.
Exploitability and Impact Assessment
Evaluating the exploitability and impact of a vulnerability is paramount. The likelihood of an attacker successfully exploiting the vulnerability needs to be assessed. This involves considering factors like the complexity of the exploit, the availability of exploit code, and the potential for widespread impact. Understanding the potential impact, such as data breaches, service disruptions, or financial losses, is essential to prioritizing vulnerabilities effectively.
Implementing Prioritization Strategies
Implementing effective prioritization strategies involves various techniques. These include using risk matrices, scoring systems, and vulnerability databases. These tools help in assigning scores or ratings to vulnerabilities based on their severity level. Prioritizing by the potential impact of exploitation is often a key component of these strategies.
Prioritizing Vulnerabilities During Development
Integrating vulnerability prioritization into the software development lifecycle (SDLC) is highly recommended. This approach ensures that vulnerabilities are addressed early in the development process. This allows for a more efficient and cost-effective resolution of issues. Regular security assessments throughout the development lifecycle are key to proactively addressing potential threats.
Continuous Monitoring and Improvement
The process of vulnerability prioritization isn't static. Continuous monitoring and improvement are essential. As new threats emerge and systems evolve, the prioritization strategy needs to adapt. Security teams should regularly review and update their prioritization methodologies to reflect the changing threat landscape and the evolving system architecture. Regularly updating the vulnerability database is an essential part of this continuous improvement.