Modern households are witnessing a transformation in how security is implemented, with smart home systems leading the charge. These innovative solutions combine cutting-edge sensors, intelligent video monitoring, and adaptive algorithms to create a multi-layered defense mechanism. This represents a monumental leap from conventional alarm systems, granting residents unprecedented control over their safety. What sets these systems apart is their predictive capabilities—analyzing behavioral patterns to differentiate between normal activity and potential threats, often preventing incidents before they occur.
The true brilliance of these systems lies in their learning capacity. Through continuous data analysis, they refine their understanding of a home's unique rhythms, drastically reducing false alerts while maintaining vigilant protection. This intelligent adaptation provides users with a seamless interface that simplifies security management without compromising effectiveness.
Advanced Features and Technologies
Today's home protection goes far beyond simple sirens and motion detectors. State-of-the-art sensors now incorporate sophisticated discrimination algorithms that can tell the difference between a family pet and an intruder, or between wind-blown branches and forced entry attempts. High-definition surveillance systems offer crystal-clear remote viewing, putting property monitoring literally in the palm of homeowners' hands.
Innovations like smart locks revolutionize access control, enabling keyless entry through smartphone authorization while automatically securing premises when residents leave. When integrated with other home automation systems, these security features can trigger appropriate responses—like turning on lights during detected movement—creating a cohesive protective environment.
Remote Monitoring and Control
The ability to oversee and manage home security from any location has fundamentally changed residential protection. Modern applications transform smartphones into powerful monitoring stations, providing instant alerts and live feeds that keep homeowners connected to their property. This remote capability extends to creating customized security schedules that adapt to changing routines, offering protection that evolves with residents' lifestyles.
Integration with Other Smart Home Devices
The synergy between security systems and other smart home components creates a truly intelligent living space. When security sensors detect unusual activity, they can trigger coordinated responses across multiple systems. Imagine a scenario where detected smoke automatically unlocks doors for emergency access while simultaneously alerting authorities—this is the power of integrated smart home security.
Future Trends and Innovations
The horizon of home security technology continues to expand with remarkable innovations. Artificial intelligence is poised to make systems more intuitive, capable of learning family patterns and predicting potential threats with greater accuracy. The integration of biometric verification methods like facial recognition and fingerprint scanning will likely become standard, offering both enhanced security and streamlined access. These advancements promise to make future homes not just safer, but smarter about protection.
Vulnerabilities in Smart Home Security Systems

Smart Home Network Weaknesses
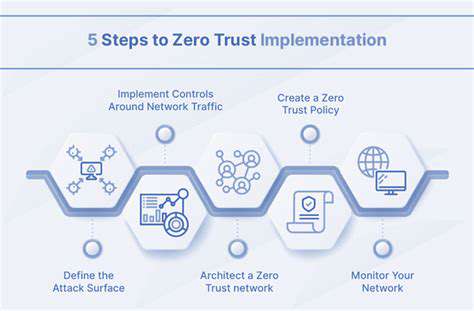
The interconnected nature of smart devices creates potential entry points for security breaches. When multiple devices share a network infrastructure, compromising one vulnerable point can expose the entire system. Common oversights like weak authentication credentials or neglected firmware updates dramatically increase exposure to cyber threats. This network vulnerability highlights the importance of implementing robust security protocols across all connected components.
Device-Specific Security Flaws
Many internet-connected home devices ship with inherent security shortcomings. These often result from rushed development cycles where security takes a backseat to functionality. Manufacturers frequently prioritize quick market entry over thorough security testing, leaving devices vulnerable to exploitation. The widespread use of generic default login credentials compounds this issue, as these are often easily discoverable through basic online searches.
The absence of multi-step verification in many devices represents another significant vulnerability. Implementing additional authentication layers would substantially strengthen overall security measures against unauthorized access attempts.
Data Privacy Concerns
Smart systems generate and process enormous amounts of sensitive information, from daily routines to personal identifiers. Without proper encryption and access controls, this data becomes vulnerable to interception or misuse during transmission and storage. Consumers often lack clear information about how their data is handled, underscoring the need for transparent data policies and user control options.
User Behavior and Security Practices
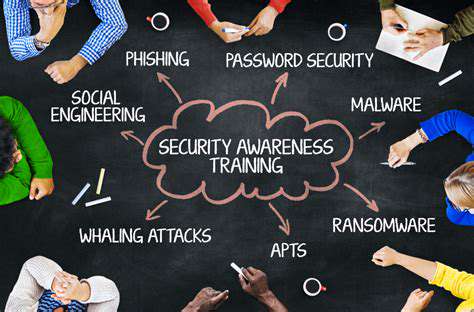
Even the most advanced systems depend on responsible user practices for optimal protection. Neglecting basic security hygiene—like regular password updates and software patches—can undermine even robust security architectures. Cultivating security awareness and promoting proactive maintenance habits among users is as crucial as technological safeguards in creating comprehensive protection.
Patient flow, in healthcare settings, describes how patients move through different care stages, starting from their first contact until discharge. This process involves multiple steps like appointment scheduling, paperwork completion, diagnostic tests, treatment administration, and final discharge. A well-managed patient flow system is fundamental for delivering high-quality care and ensuring patients leave satisfied. When patient flow improves, healthcare facilities operate more efficiently and effectively.
Beyond the Tech: Cultural and Legal Considerations
Privacy Concerns in Smart Home Surveillance
The convenience of always-on monitoring comes with significant privacy tradeoffs. Continuous recording within living spaces creates tension between security benefits and personal privacy rights. Establishing clear guidelines about data access, retention periods, and authorized usage is essential for balancing these competing priorities. As surveillance technologies become more sophisticated, questions emerge about their potential for misuse, whether through data breaches or unauthorized access by third parties.
Legal Ramifications of Home Surveillance
Legal frameworks governing residential surveillance vary considerably across regions. Some jurisdictions impose strict limitations on recording in private spaces, while others focus more on notification requirements. Understanding these legal nuances is critical to avoid unintentionally violating privacy laws or having recorded evidence deemed inadmissible. The legal status of recordings often depends on context—whether they capture private interiors or public areas, and whether audio recording is involved.
Ethical Considerations in Camera Deployment
Installing monitoring systems demands careful ethical reflection. Beyond legal compliance, homeowners should consider how surveillance might affect household dynamics and relationships. Open discussions about camera placement and usage policies can prevent misunderstandings and preserve trust among household members. The broader societal impact of normalized surveillance also warrants consideration, as it may subtly alter community interactions and expectations of privacy.
Cultural Sensitivity and Smart Home Security
Cultural perspectives on privacy and surveillance vary dramatically worldwide. Practices considered normal in some societies may be deeply offensive in others. When implementing security measures in multicultural contexts, it's crucial to research and respect local norms regarding personal space and observation. This cultural awareness helps prevent unintended offenses while maintaining effective security.
Data Security and Privacy in the Cloud
Cloud-based storage solutions for security footage introduce additional considerations. Evaluating a provider's encryption standards, data handling policies, and breach response protocols should be a priority when selecting surveillance systems. Consumers should understand where their data is stored, who might access it, and under what circumstances—especially when dealing with international service providers subject to different privacy regulations.
Maintenance and Responsibility in Camera Use
Owning surveillance systems carries ongoing responsibilities beyond initial installation. Regular system updates, periodic review of access permissions, and compliance with evolving privacy laws require sustained attention from homeowners. Proper maintenance not only ensures system effectiveness but also mitigates potential legal and ethical risks associated with surveillance technology.