Identifying Potential Insider Threats within Your Supply Chain
Understanding the Scope of Insider Threats
Spotting potential insider threats in your supply chain demands a deep dive into the diverse players involved and their vulnerabilities. This includes not just employees handling sensitive data but also contractors, vendors, and third-party providers. A key insight is that insider threats aren't always intentional—they can arise from carelessness, ignorance, or honest mistakes. Addressing these weaknesses proactively is non-negotiable for risk reduction.
Assessing the Risk Factors within Your Supply Chain
A meticulous evaluation of supply chain risks is indispensable. Analyze each stakeholder's access to critical information and assets, considering interaction frequency, data sensitivity, and breach consequences. Regular audits and risk assessments are vital to catch vulnerabilities early, covering both physical and digital access points.
Don't overlook cultural factors. A workplace that champions security and ethics drastically lowers insider threat risks compared to one with loose security norms.
Implementing Robust Security Measures
Deploying ironclad security protocols across your supply chain is essential. Mandate multi-factor authentication, conduct frequent security training, and establish clear data handling policies. Strict enforcement and regular updates of these protocols ensure everyone knows their duties and the fallout of non-compliance.
Establishing Clear Communication Channels
Transparent communication is the backbone of effective incident response. Set up straightforward reporting mechanisms for suspected threats and designate a response team. Encouraging open reporting—without fear of backlash—ensures swift action to limit damage.
Conducting Regular Security Audits and Training
Ongoing audits and training are the lifeblood of supply chain security. Audits should test existing measures and highlight gaps, while training should cover threat awareness, best practices, and ethical conduct. This proactive stance keeps risks top of mind and equips teams to handle them.
Enhancing Background Checks and Due Diligence
Rigorous vetting of employees and third parties is non-negotiable. Screen for past security issues or red flags, extending checks to contractors and vendors. Thorough due diligence slashes insider threat risks by ensuring only trustworthy parties access sensitive assets. This is a cornerstone of supply chain risk management.

Fostering a Culture of Security and Transparency

Building a Strong Foundation
A resilient security culture grows from clear communication, consistent training, and universal buy-in on security's importance. Defining unambiguous guidelines ensures everyone knows their role in safeguarding the organization.
Swift, open communication channels are critical for sharing updates and incidents. Role-specific training arms employees with threat-spotting skills.
Defining Roles and Responsibilities
Clarity is power. Documenting each person's security duties eliminates ambiguity and fosters accountability. Employees must grasp how their actions impact the organization's safety.
Promoting a Culture of Reporting
Security thrives when staff can report concerns freely. A blame-free environment and confidential reporting channels are game-changers. This teamwork approach nips threats in the bud.
Implementing Effective Training Programs
Dynamic training—think simulations and hands-on drills—keeps defenses sharp. Tailor content to roles for maximum relevance and retention.
Encouraging Proactive Security Measures
Great security cultures don't just react; they anticipate. Empower employees to flag risks early.
Utilizing Technology for Security
Layer defenses with tools like firewalls and multi-factor authentication. Regular updates ensure these shields stay robust.
Measuring and Evaluating Success
Track metrics like incident rates to gauge security health. Regular policy reviews keep defenses aligned with evolving threats.
Establishing Contingency Plans and Incident Response Protocols
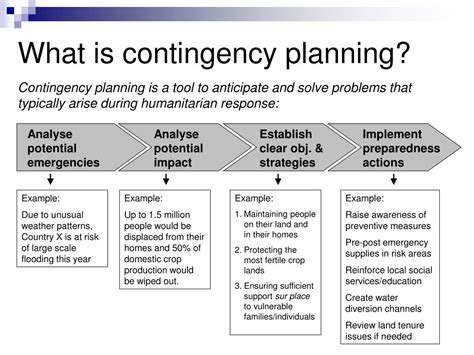
Developing Robust Contingency Plans
A bulletproof contingency plan is your playbook for chaos, detailing responses to supply chain snags, tech failures, or disasters. It's about foresight—spotting risks early and scripting recovery steps.
Identifying Potential Disruptions
Cast a wide net when hunting for risks, from internal hiccups like staff shortages to external shocks like economic crashes. Historical data and expert input reveal blind spots.
Defining Clear Response Procedures
Crises demand choreographed responses. Document who does what, with clear escalation paths. Keep this manual current and within easy reach.
Allocating Resources Effectively
Budget for the unexpected. Skimping on contingency funds or backup systems can cripple recovery efforts.
Testing and Evaluating the Plan
Stress-test plans through realistic drills. Debrief participants to fine-tune weaknesses before real disasters strike.
Maintaining and Updating the Plan
Treat your plan like software—patch it regularly. New threats and organizational changes demand constant revisions.