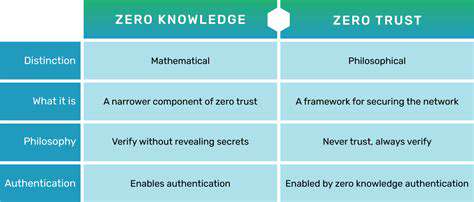
Optimizing Security Operations with Automation

Implementing Robust Access Controls
When it comes to safeguarding sensitive data, few measures are as fundamental as implementing robust access controls. Organizations must carefully map out user roles and permissions, creating a digital fortress where each individual only accesses what's absolutely necessary for their role. The principle of least privilege isn't just a recommendation—it's a security imperative that dramatically reduces potential attack surfaces.
What many security teams overlook is the dynamic nature of access requirements. Personnel changes, role adjustments, and project rotations all demand continuous access control reviews. A well-documented policy that's regularly updated and thoroughly communicated forms the backbone of effective access management. When everyone understands the why behind security protocols, compliance becomes significantly easier to maintain.
Employing Multi-Factor Authentication
In today's threat landscape, passwords alone are about as effective as a screen door on a submarine. Multi-factor authentication (MFA) introduces critical friction in the authentication process, requiring would-be attackers to overcome multiple verification hurdles that often include physical devices or biometric markers. The psychological impact on security posture is almost as valuable as the technical protection—users become more conscious of security when they regularly interact with multiple authentication factors.
The most security-conscious organizations extend MFA requirements beyond user accounts to all administrative interfaces and system access points. This creates a consistent security blanket across the entire digital infrastructure rather than leaving certain systems vulnerable as weak points in the security chain.
Regular Security Audits and Assessments
Security isn't a destination—it's an ongoing journey that requires constant vigilance. Routine audits serve as checkpoints in this journey, revealing vulnerabilities before attackers exploit them. These evaluations should examine both technical configurations and human processes, as security weaknesses often emerge at the intersection of technology and behavior.
What separates adequate security from exceptional protection is the willingness to simulate attacks through penetration testing. These controlled exercises uncover vulnerabilities that automated scans might miss, providing insights into how different attack vectors could chain together to compromise systems. The most valuable assessments don't just identify problems—they prioritize them based on real-world exploit potential.
Proactive Threat Intelligence
The cybersecurity landscape evolves at breakneck speed, with new threats emerging daily. Organizations that merely react to threats after they surface are playing a dangerous game of catch-up. Effective security operations require constant horizon-scanning for emerging attack methods and vulnerabilities.
Threat intelligence becomes truly valuable when it's contextualized for an organization's specific risk profile. The most sophisticated security teams don't just monitor threats—they analyze how those threats might uniquely impact their systems and develop targeted defenses accordingly. This predictive approach transforms security from a cost center into a strategic advantage.
Incident Response Planning
No security strategy is complete without acknowledging that breaches will occur. The difference between a minor incident and a catastrophic breach often comes down to response preparedness. A well-crafted incident response plan serves as both a playbook and a communication framework during high-stress security events.
The most effective plans go beyond documentation—they're regularly stress-tested through realistic simulations that reveal gaps in procedures or coordination. These exercises should challenge assumptions about detection capabilities, response times, and communication flows between technical teams, executives, and potentially affected stakeholders.
Employee Security Awareness Training
Technology can only go so far in protecting an organization—the human element remains both the greatest vulnerability and the most powerful defense. Effective security training moves beyond annual compliance checkboxes to create a culture of security mindfulness.
The most engaging programs use real-world examples and interactive scenarios to help employees recognize subtle social engineering tactics. When staff members understand how their daily actions contribute to organizational security, they transform from potential weak links into active participants in threat detection and prevention.
Security Information and Event Management (SIEM)
In complex IT environments, security signals often get lost in the noise. SIEM solutions act as sophisticated filters and correlators, turning fragmented log data into actionable security intelligence. The true power of these systems lies in their ability to identify patterns across disparate systems that might indicate coordinated attacks.
Advanced SIEM implementations leverage machine learning to establish behavioral baselines, making anomalous activity stand out more clearly. When properly configured and continuously tuned, these systems don't just alert to known threats—they help uncover novel attack patterns that haven't yet been documented in threat databases.