
Implementing Zero Trust Principles
Zero Trust security models operate on a simple yet revolutionary premise: trust must be earned continuously, never granted by default. Unlike traditional security approaches that assume safety within network boundaries, this methodology demands rigorous authentication for every access attempt, whether originating inside or outside the organizational perimeter.
Effective implementation requires robust identity verification systems coupled with dynamic access control frameworks that adapt to changing risk factors. These systems must evaluate multiple contextual factors - including user behavior, device health, and request timing - to make intelligent access decisions. By maintaining this constant vigilance, organizations can dramatically shrink their vulnerable attack surfaces while neutralizing threats from credential theft or insider risks.
Key Components of a Zero Trust Architecture
Building a resilient Zero Trust infrastructure involves deploying several critical security layers. Multi-factor authentication (MFA) stands as the first line of defense, requiring users to present multiple evidence types - something they know (password), something they have (security token), and something they are (biometric) - before gaining entry. This layered verification makes unauthorized access exponentially more difficult, even when attackers obtain valid credentials.
Network microsegmentation creates security compartments that contain potential breaches. This architectural approach transforms networks into collections of isolated security zones, ensuring that a compromise in one area cannot spread laterally to other systems. Each segment operates with customized security policies tailored to its specific risk profile and sensitivity level.
Strategic network segmentation further enhances protection by establishing clear security boundaries between different data classifications and business functions. This structured approach enables precise control over information flows while simplifying compliance with regulatory requirements.
Data Security and Policy Enforcement
Zero Trust demands comprehensive data protection strategies that extend beyond perimeter defenses. Advanced data loss prevention (DLP) systems must identify, classify, and protect sensitive information wherever it resides or moves. Consistent policy enforcement across all access points forms the backbone of effective data security, ensuring uniform protection regardless of where or how data is accessed.
Security policies under Zero Trust must evolve continuously to address emerging threats and business changes. Regular policy reviews and updates maintain alignment with the shifting risk landscape while supporting organizational agility. This dynamic policy management approach represents a fundamental shift from static, compliance-focused security models.
Comprehensive monitoring systems provide the visibility needed to detect and respond to security incidents promptly. These solutions should correlate events across all security layers, using behavioral analytics to identify anomalies that might indicate compromise. The resulting security intelligence enables organizations to transition from reactive defense to proactive threat anticipation.
The true power of Zero Trust emerges from its continuous verification cycle and adaptive response capabilities. This paradigm represents a fundamental shift from passive perimeter defense to active, intelligence-driven security operations.
Zero Knowledge Proofs: Guaranteeing Authenticity Without Revealing Secrets

Zero-Knowledge Proof Fundamentals
Zero-knowledge proofs (ZKPs) represent a cryptographic breakthrough enabling truth verification without information disclosure. This elegant solution allows one party to confirm another's knowledge of secret information while learning nothing about the secret itself. The mathematical elegance of ZKPs lies in their ability to prove possession without revealing contents, making them invaluable for privacy-preserving verification scenarios.
Consider proving you know a complex mathematical solution without showing your work. ZKPs make this possible through clever cryptographic constructions that verify correctness while maintaining complete secrecy about the underlying method or data.
Proving Knowledge, Not Revealing Secrets
The unique value proposition of ZKPs centers on their ability to establish truth without transferring knowledge. Verifiers gain absolute certainty about a statement's validity while remaining completely ignorant of the statement's content. This property makes ZKPs particularly valuable in high-stakes environments where information disclosure could create unacceptable risks.
This verification paradigm enables new forms of secure interaction where privacy and security coexist without compromise, opening doors to previously impossible security architectures.
Applications in Blockchain Technology
Blockchain implementations increasingly leverage ZKPs to resolve the inherent tension between transparency and privacy. These cryptographic tools enable network participants to validate transaction correctness without exposing sensitive details to public scrutiny.
This application demonstrates ZKPs' dual benefit - maintaining blockchain's trustless verification principle while adding essential privacy protections absent in early implementations.
Improving Transaction Privacy
ZKPs revolutionize financial privacy in distributed ledgers by enabling selective disclosure. Transaction validity becomes provable without exposing amounts, participants, or business logic, addressing one of blockchain technology's most significant adoption barriers. This capability proves particularly valuable for enterprise applications requiring confidentiality alongside distributed verification.
Traditional transparent blockchains create privacy challenges by design. ZKP-enhanced chains maintain all verification benefits while adding essential confidentiality features needed for commercial adoption.
Enhancing Scalability
ZKPs contribute significantly to blockchain scalability through data compression. By replacing bulky transaction data with compact proofs, ZKPs reduce network bandwidth requirements and storage burdens. This efficiency gain enables higher transaction throughput without compromising security or decentralization principles.
The resulting performance improvements make blockchain solutions more practical for high-volume applications while maintaining their core security guarantees.
Security and Trust Considerations
While ZKPs offer remarkable capabilities, their security depends entirely on proper implementation. Flawed cryptographic constructions or implementation errors can create false confidence with potentially catastrophic consequences.
Rigorous third-party audits and extensive testing must validate any ZKP system before production deployment. Only through meticulous verification can organizations ensure their ZKP implementations deliver the promised security benefits without introducing unexpected vulnerabilities.
Future Directions and Challenges
ZKP research continues advancing on multiple fronts, with particular focus on reducing computational overhead and expanding applicability. Current efforts aim to make these proofs practical for resource-constrained environments while maintaining their strong security guarantees.
The field must balance theoretical elegance with real-world performance, ensuring ZKP solutions remain both cryptographically sound and practically deployable across diverse use cases.
The Synergy of Zero Trust and Zero Knowledge
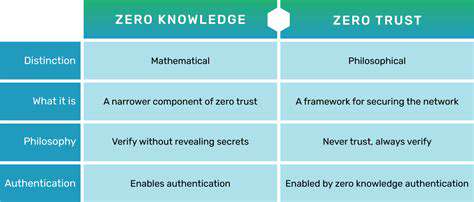
Zero Trust Architecture: A Foundation for Enhanced Security
The Zero Trust model revolutionizes security by eliminating implicit trust assumptions. This architecture treats every access attempt as potentially hostile, requiring continuous validation regardless of origin or previous authentication. By abandoning the outdated trust but verify approach, organizations gain fine-grained control over resource access while dramatically reducing attack surfaces.
Central to this model are dynamic access policies that evaluate multiple risk factors in real-time. These policies must balance security requirements with operational needs, ensuring protection without creating unnecessary friction for legitimate users.
Zero Compromise Security Posture
The combination of Zero Trust principles with uncompromising security standards creates a formidable defense posture. This approach assumes breach inevitability while designing systems to contain and neutralize threats automatically. Each security layer operates independently yet cooperatively, ensuring that no single failure can compromise the entire environment.
This defense-in-depth strategy proves particularly effective against modern threats that exploit trust relationships and security blind spots in traditional architectures.
Enhanced Visibility and Control
Zero Trust implementations generate unprecedented security visibility by instrumenting all access attempts and system interactions. The resulting data streams enable security teams to detect anomalies faster and respond more precisely than traditional monitoring approaches.
This comprehensive observability transforms security operations from reactive troubleshooting to proactive threat hunting, fundamentally changing how organizations defend their digital assets.
Data Protection and Compliance
Zero Trust architectures naturally support compliance objectives by enforcing least-privilege access to sensitive information. Granular access controls ensure data remains protected regardless of user location or device type, simplifying compliance with evolving privacy regulations. This approach particularly benefits organizations operating across multiple jurisdictions with conflicting regulatory requirements.
Improved Operational Efficiency
Contrary to initial assumptions, Zero Trust architectures often improve operational efficiency by replacing complex perimeter defenses with streamlined, policy-driven access controls. This modernization reduces security complexity while improving both protection and user experience, particularly for distributed workforces accessing resources from varied locations and devices.
The resulting architecture proves more adaptable to changing business needs while maintaining strong security assurances.
Beyond Authentication: Zero Knowledge in Data Integrity
Beyond Basic Verification: Zero-Knowledge Proofs for Data Integrity
Zero-knowledge proofs extend far beyond authentication, offering revolutionary approaches to data integrity verification. These cryptographic techniques enable systems to confirm information accuracy without examining the information itself - a capability particularly valuable in zero-trust environments where verification must occur without information disclosure.
Consider document validation scenarios where authenticity matters more than content. ZKPs enable rigorous verification while maintaining complete confidentiality, using mathematical relationships rather than content inspection to establish trust.
Enhancing Data Security with Non-Interactive Proofs
Non-interactive ZKP variants offer particular value for modern distributed systems. These efficient proofs enable verification without multiple communication rounds, making them ideal for high-volume applications like financial settlements or IoT device authentication.
This efficiency unlocks new possibilities for secure, privacy-preserving systems that must scale to handle millions of daily verifications without performance degradation.
Zero-Knowledge and the Prevention of Data Tampering
ZKPs provide powerful tools for detecting unauthorized data modifications. By creating cryptographic fingerprints tied to original content, these proofs enable tamper detection without exposing sensitive information. This capability proves invaluable for audit trails, evidentiary records, and any scenario where data provenance matters.
Financial systems particularly benefit from this application, as ZKPs can verify transaction integrity while maintaining strict confidentiality around amounts and participants.
Zero-Knowledge and Data Privacy
The privacy-preserving nature of ZKPs makes them ideal for compliance-sensitive environments. These techniques enable organizations to demonstrate regulatory compliance without exposing protected data to auditors or third parties. This breakthrough addresses one of the most challenging aspects of modern privacy regulations - proving compliance without creating new privacy risks.
Scalability and Practical Application
As ZKP technology matures, real-world applications continue expanding. Current implementations demonstrate the feasibility of applying these techniques to supply chain verification, identity management, and even voting systems. Each successful deployment provides valuable lessons for overcoming the performance challenges inherent in advanced cryptography.
The intersection of ZKPs with distributed ledger technology creates particularly promising opportunities. This combination enables trustworthy data sharing across organizational boundaries while maintaining strict confidentiality controls - a capability that could transform how enterprises collaborate securely.











