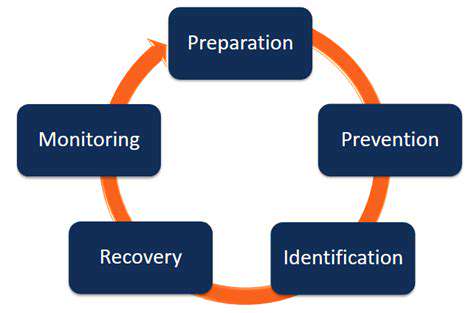
Understanding Backup and Recovery
A well-structured backup and recovery plan is indispensable for businesses and individuals who prioritize data security. Losing critical information can wreak havoc, damaging operations, credibility, and financial health. A solid strategy guarantees that essential data remains recoverable during emergencies—be it system crashes, cyberattacks, or natural calamities. Maintaining consistent backups and secure storage protocols minimizes risks and ensures operational resilience.
It's vital to grasp the distinctions between full, incremental, and differential backups. Each method offers unique advantages and drawbacks in terms of storage efficiency and restoration speed. Selecting the optimal backup approach depends on your data volume and specific requirements, ensuring minimal disruption during recovery. Equally important is deciding where to store backups—locally, remotely, or in the cloud—to safeguard against physical threats.
Implementing a Backup Strategy
Developing a backup strategy goes beyond mere data duplication. A thorough plan must incorporate routine tests and validations to confirm backup functionality. Verifying backup integrity ensures files remain uncorrupted and ready for restoration. Proactive testing helps uncover flaws in the process, allowing timely corrections before emergencies arise.
Beyond technical measures, effective backup planning demands clear protocols and communication. A written recovery blueprint outlining disaster response steps is non-negotiable. This document should specify roles, timelines, and required resources. Educating employees on their responsibilities during recovery significantly enhances the likelihood of successful data retrieval.
Choosing the Right Backup Solution
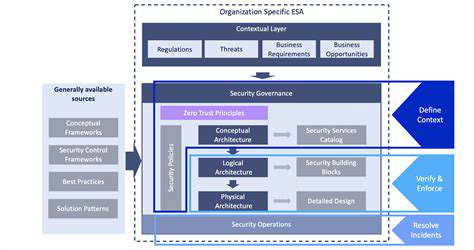
Selecting an appropriate backup system requires evaluating data volume, budget constraints, and security needs. Cloud-based options provide flexibility and scalability, while local solutions offer quicker restoration. Comparing various software and hardware alternatives helps identify the optimal match for your infrastructure. Key considerations include encryption standards, disaster recovery features, and compatibility with existing systems.
Security must remain paramount when selecting backup technologies. Verify that chosen methods implement robust encryption for data in transit and at rest. An effective backup solution must defend against diverse threats, including ransomware and malware intrusions. Regular security audits ensure continued protection against evolving cyber risks. Understanding available recovery options is equally crucial for making informed decisions.

Testing and Refining Your Plan: A Living Document
Understanding the Dynamic Nature of Threats
Ransomware defense strategies cannot remain static—they must evolve with the shifting cybersecurity landscape. Contemporary ransomware employs increasingly complex methods, exploiting vulnerabilities once considered secure. Recognizing this fluid threat environment is fundamental for developing effective countermeasures. Regular plan revisions maintain proactive defenses against novel attack vectors.
Staying informed about emerging ransomware trends, attack methods, and security updates is critical. Organizations that neglect to update their strategies risk exposure to devastating breaches and operational paralysis.
Regularly Evaluating Your Vulnerabilities
Continual vulnerability assessment forms the backbone of ransomware preparedness. This involves systematically identifying weaknesses in networks, systems, and security policies that attackers might exploit. Conduct these evaluations quarterly at minimum, ensuring defenses match current threat levels across all infrastructure components.
Comprehensive assessments should examine network perimeters, endpoints, applications, and storage systems. Analyze security procedures, staff training effectiveness, and incident response protocols. Prioritize remediation efforts based on assessment findings to maximize protection.
Testing Your Incident Response Plan
Untested incident response plans offer false security. Regular ransomware simulations prove essential for verifying team preparedness. These drills should replicate realistic scenarios involving system disruptions, data compromises, and financial impacts. Such exercises reveal procedural gaps while improving response coordination.
Practical testing not only validates procedures but also builds team confidence during actual crises. Familiarity with response protocols enables quicker decisions and more organized reactions when real threats emerge.
Implementing and Monitoring Security Controls
Robust security measures constitute the foundation of ransomware defense. Install advanced firewalls, intrusion prevention systems, and endpoint protection solutions. Equally important is comprehensive security training for all personnel. Educated employees who can spot and report suspicious activity create a critical human firewall against threats. Security implementation demands ongoing attention and adaptation rather than one-time deployment.
Frequently audit security controls to maintain effectiveness. Monitor system logs and alerts for anomalies that might indicate compromise attempts. This continuous surveillance enables preemptive action against potential breaches.
Continuous Improvement and Adaptation
Effective ransomware preparedness requires perpetual evolution. Treat your defense plan as a dynamic document that incorporates new threat intelligence, simulation insights, and real incident lessons. This iterative approach ensures continued relevance against advancing ransomware tactics.
Solicit input from security teams and stakeholders to identify enhancement opportunities. Collaborative refinement produces more resilient, comprehensive protection strategies tailored to organizational needs.