The Evolving Threat Landscape in Retail
The Rise of Advanced Persistent Threats (APTs)
Modern cybersecurity faces a growing challenge from Advanced Persistent Threats (APTs), which represent one of the most sophisticated dangers in digital security. These well-organized attacks, often backed by nation-states or highly skilled criminal networks, specialize in maintaining long-term access to compromised systems. APTs follow a meticulous process involving reconnaissance, system infiltration, and data extraction over extended periods. Their effectiveness stems from combining social engineering tactics with advanced malware techniques and previously unknown system vulnerabilities. Security teams must thoroughly understand these attack methods to create appropriate defense mechanisms.
As APT methodologies continue evolving, businesses must adopt dynamic security strategies. This involves regularly updating defensive measures, incorporating comprehensive threat intelligence systems, and deploying state-of-the-art protective technologies. The cybersecurity field must prioritize continuous education and flexibility to counter these increasingly complex threats effectively.
The Growing Importance of Cloud Security
Cloud computing's widespread adoption has fundamentally changed security requirements. Protecting cloud-based infrastructure demands specialized approaches for securing virtual environments, containerized applications, and distributed data storage. Security incidents in cloud platforms can lead to substantial financial penalties and lasting damage to organizational reputation.
Addressing cloud vulnerabilities requires a comprehensive security framework. Businesses need to establish enhanced access management protocols, implement strong encryption standards, and deploy monitoring systems specifically designed for cloud architectures. Successful cloud protection strategies must acknowledge the platform's unique characteristics and implement appropriate safeguards.
The Impact of Ransomware Attacks
Ransomware continues to pose significant risks across all sectors. These attacks typically encrypt essential data and demand payment for restoration. The operational and financial consequences of successful ransomware attacks can cripple organizations for extended periods. Recovery efforts often involve costly data recovery processes, system repairs, and potential legal complications.
With ransomware tools becoming more accessible through RaaS platforms, preventative measures have never been more critical. Organizations should prioritize comprehensive endpoint protection, maintain reliable backup systems, and educate staff on phishing recognition. Preventative security measures including vulnerability assessment and threat monitoring play vital roles in reducing ransomware risks.
The Expanding Role of IoT Devices
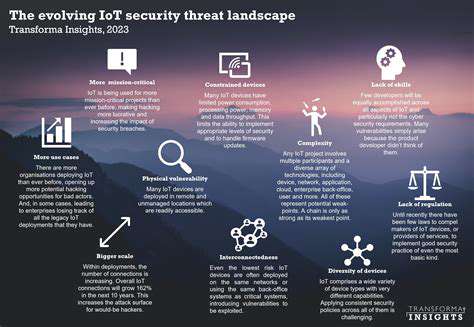
The rapid growth of Internet-connected devices has introduced numerous security challenges. Many IoT products lack adequate security features, creating potential entry points for network breaches. The interconnected nature of smart devices establishes complex vulnerability chains that attackers can exploit to access sensitive systems.
Effective IoT security requires comprehensive protection strategies. Organizations must implement device authentication systems, data encryption protocols, and regular firmware updates. Maintaining consistent security standards across all connected devices is essential for reducing breach risks.
The Need for Enhanced Threat Intelligence
Contemporary security operations increasingly rely on advanced threat intelligence capabilities. Understanding attacker methodologies through detailed analysis allows organizations to anticipate and prevent potential breaches before they occur.
Developing effective threat intelligence involves synthesizing information from multiple sources including OSINT, SIEM platforms, and external threat data streams. Analyzing these information sources helps identify emerging threat patterns, enabling organizations to develop precise defensive measures against sophisticated attacks.
Proactive Inventory Protection Strategies
Understanding the Importance of Proactive Protection
Effective inventory protection requires anticipating potential risks rather than simply responding to incidents. This forward-looking approach is essential for maintaining profitability and operational continuity in retail environments. By identifying potential vulnerabilities early, businesses can implement preventative measures that safeguard assets and minimize losses. Comprehensive protection strategies must consider the entire supply chain and factors that could compromise inventory security.
Implementing Robust Security Systems
Advanced security infrastructure forms the foundation of effective inventory protection. Beyond visible deterrents like surveillance equipment, comprehensive systems should include access control technologies and inventory tracking software. Security configurations must account for each location's specific requirements, considering product types, facility layout, and surrounding environment.
Regular security system evaluations and upgrades are essential to maintain effectiveness. As criminal techniques evolve and technology advances, security measures must adapt accordingly to provide optimal protection.
Optimizing Warehouse and Retail Space Layout
Strategic facility design significantly influences inventory security. Well-planned layouts with properly positioned security checkpoints, storage areas, and access routes can deter theft while improving staff visibility. Proper lighting and clear pathways not only enhance safety but also make unauthorized activities more noticeable.
Employing Effective Inventory Management Techniques
Precise inventory tracking systems are fundamental to proactive protection. Real-time stock monitoring, detailed transaction records, and regular inventory audits help quickly identify discrepancies. This data also reveals patterns that indicate potential vulnerabilities, allowing businesses to strengthen security in critical areas.
Employee Training and Awareness Programs
Staff education plays a crucial role in inventory protection. Comprehensive training programs should emphasize threat recognition, proper reporting procedures, and the importance of security protocols. Establishing a culture of accountability among employees creates an additional layer of protection and helps prevent security incidents before they occur.
Safeguarding Customer Data in the Digital Age

Protecting Sensitive Information
Data protection has become critical in modern business operations, requiring multi-layered security approaches. Organizations must clearly understand what data they collect and process, then implement appropriate safeguards against unauthorized access or modification. Strong encryption for stored and transmitted data ensures information remains protected even if intercepted. Regular security evaluations help identify and address potential weaknesses proactively.
Implementing Secure Data Storage
Choosing appropriate data storage solutions requires careful consideration of security requirements. Cloud platforms with advanced security features offer robust protection when properly configured. This includes implementing strict access controls, physical security measures for data centers, and comprehensive backup systems. Regular data backups stored in multiple locations minimize potential data loss risks.
Developing Comprehensive Security Policies
Clear security policies establish essential guidelines for data handling and system usage. These documents should outline incident response procedures and employee responsibilities regarding data protection. Regular policy reviews ensure security measures remain effective against evolving threats.
Employee Training and Awareness
Staff education is fundamental to maintaining data security. Employees should understand protection principles, company policies, and how to recognize potential security threats. Ongoing training programs keep security knowledge current and reinforce best practices.
Utilizing Multi-Factor Authentication
Implementing MFA significantly enhances account security. Requiring multiple verification methods makes unauthorized access considerably more difficult. This additional security layer protects sensitive customer information from compromise.
Monitoring and Incident Response
Continuous system monitoring helps detect potential security incidents early. Advanced SIEM solutions can identify suspicious activity patterns, enabling proactive threat response. Well-defined incident response plans ensure organizations can effectively manage security breaches when they occur.
Staying Updated on Security Best Practices
The security field constantly evolves, requiring organizations to stay informed about new threats and protection methods. Regularly reviewing security tools, participating in training, and engaging with the security community helps maintain effective data protection.
Implementing Integrated Security Systems
Implementing Robust Access Control
Effective security systems begin with comprehensive access management. Modern solutions extend beyond traditional locks to include keycard systems, biometric verification, and advanced recognition technologies. These measures provide granular control over facility access points, preventing unauthorized entry to sensitive areas. Digital access controls for internal systems through strong authentication methods protect critical business data and transactions.
Utilizing Advanced Surveillance Technologies
Contemporary surveillance systems combine high-definition cameras with intelligent software for comprehensive monitoring. Integrated video management platforms enable real-time observation and historical review. Adding analytics capabilities allows for automatic detection of suspicious activities, enabling faster response to potential security incidents.
Protecting Inventory and Assets
Complete security strategies must include inventory protection measures. This involves secure storage solutions, anti-theft technologies for merchandise, and regular inventory verification processes. These practices help maintain accurate records while preventing loss.
Enhancing Employee Training and Awareness
Security system effectiveness depends on knowledgeable staff. Training programs should cover security procedures, threat recognition, and proper incident response. Creating a security-conscious culture makes employees active participants in protection efforts.
Integrating Security Systems with Existing Infrastructure
New security implementations should complement current operations. Careful planning ensures compatibility with existing systems while minimizing disruptions. Thorough testing and documentation during implementation helps maintain long-term system effectiveness.