Fundamentals of Profitable Business Models
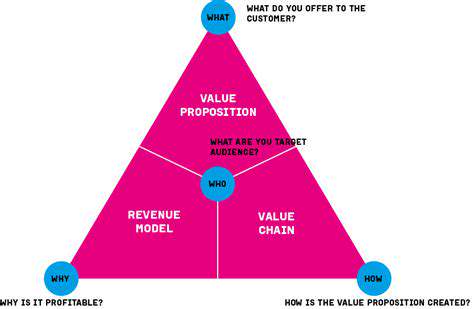
Successful enterprises share common foundations: clear market understanding, compelling value propositions, and sustainable revenue generation. These elements create the framework for enduring commercial success and competitive differentiation. Businesses that master these fundamentals demonstrate remarkable resilience in fluctuating markets.
True business success stems from solving genuine customer problems. Organizations that deeply understand their customers' challenges can develop solutions that command premium pricing and loyalty. This customer-first mentality separates market leaders from competitors.
Identifying Your Ideal Customer
Effective market targeting requires detailed audience analysis including demographics, behavioral patterns, and purchasing motivations. Precise segmentation enables efficient resource allocation and targeted messaging that resonates with specific customer groups.
Continuous competitive intelligence is equally vital. Businesses that systematically monitor industry shifts and competitor moves can anticipate changes rather than react to them. This proactive stance is particularly valuable in fast-moving sectors.
Developing a Powerful Value Proposition
A strong value proposition clearly communicates why customers should choose your offering over alternatives. It must articulate specific benefits that address customer pain points better than competing solutions. This core messaging forms the foundation of all effective marketing communications.
Differentiation can take many forms - superior quality, unique features, or exceptional service. The most successful businesses create value propositions that immediately capture attention and demonstrate clear advantages.
Creating Sustainable Revenue Streams
Long-term business viability requires diversified income sources. Innovative companies explore multiple monetization strategies including subscriptions, licensing, and value-added services to create financial stability regardless of market conditions.
Marketing for Maximum Impact
Modern marketing requires integrated campaigns across multiple channels tailored to audience preferences. The most effective strategies combine digital and traditional approaches to create cohesive customer experiences.
Customer relationships now extend far beyond the initial sale. Exceptional post-purchase engagement transforms one-time buyers into brand advocates who drive organic growth.
Adapting to Market Evolution
Business agility has become a critical success factor in today's volatile markets. Organizations must develop processes for continuously scanning the environment and rapidly adapting to changes. This dynamic capability separates thriving businesses from those struggling to survive.
Regular business model evaluation ensures continuous improvement. The most successful companies institutionalize processes for testing assumptions and refining operations to maintain competitive advantage.
The Role of Cryptocurrency in Facilitating Payments
Cryptocurrency's Potential for Speed and Efficiency
Digital currencies introduce transformative possibilities for payment systems through decentralized networks and rapid transaction processing. These characteristics enable near-instantaneous global transfers that traditional banking cannot match. The transparent nature of blockchain ledgers, while complex, offers fraud prevention advantages absent in conventional systems.
Breaking Down Geographic Barriers
Cryptocurrencies eliminate many constraints inherent in international banking. Without currency exchange complications or cross-border regulatory hurdles, crypto payments flow seamlessly between countries. This capability is particularly valuable for global enterprises and remote workers receiving international payments.
Cost Advantages of Crypto Transactions
When compared to traditional wire transfers and international payments, cryptocurrencies typically offer significantly lower fees. These savings accumulate rapidly for businesses processing high volumes of transactions, making crypto an attractive option for cost-conscious organizations.
Challenges: Price Swings and Security Concerns
The cryptocurrency market's notorious volatility introduces substantial risk for payment systems. Value fluctuations between transaction initiation and completion can create unexpected financial impacts. Additionally, while blockchain technology itself is secure, cryptocurrency exchanges and wallets remain prime targets for sophisticated cybercriminals.
Regulatory Landscape Evolution
The lack of consistent global cryptocurrency regulation creates uncertainty for businesses. Differing national approaches to crypto oversight complicate compliance for multinational operations. Until clearer international standards emerge, regulatory risk will continue to hinder mainstream adoption.
Crypto's Dual Role in Ransomware Payments
The same features that make cryptocurrency ideal for legitimate global commerce - pseudonymity and decentralization - also make it perfect for illicit ransom payments. This paradox presents law enforcement with unique challenges while highlighting the need for balanced solutions that preserve crypto's benefits while reducing criminal misuse.