Introduction to AI-Driven Security Automation
Defining AI-Driven Security Automation
AI-driven security automation leverages artificial intelligence (AI) technologies to automate various security tasks, significantly enhancing the efficiency and effectiveness of security operations. This involves using machine learning algorithms to identify patterns, anomalies, and threats in real-time, enabling proactive responses and reducing the time and resources required for manual security processes. AI-powered systems can analyze vast amounts of security data, identify potential breaches, and automatically initiate security responses, ultimately fortifying the overall security posture of an organization.
The core principle lies in automating repetitive, rule-based security tasks, freeing up human security analysts to focus on more complex and strategic issues. This automation is crucial in today's complex threat landscape, where organizations are constantly bombarded with increasing volumes of security data and sophisticated attacks.
Key Benefits of AI in Security Automation
Implementing AI-driven security automation offers a multitude of benefits, including substantial time savings and cost reductions. By automating routine tasks, organizations can allocate resources more strategically, focusing on critical incident response and threat analysis. This automation also leads to improved accuracy and efficiency in identifying and responding to threats. AI systems can process data at a scale and speed that far surpasses human capabilities, leading to faster incident detection and resolution.
Furthermore, AI-driven security automation enhances the overall security posture by identifying subtle anomalies and patterns that might be missed by traditional security systems. This proactive approach allows organizations to anticipate and mitigate potential threats before they can cause significant damage or disruption.
Types of AI Technologies Used in Security Automation
A variety of AI technologies are employed in security automation, including machine learning (ML) algorithms, deep learning (DL) models, and natural language processing (NLP). ML algorithms are trained on large datasets of security events to identify patterns and anomalies, allowing systems to learn and improve over time. Deep learning models, often used for image and video analysis in security, can identify complex patterns and relationships in data that might be missed by simpler algorithms. Natural language processing (NLP) plays a crucial role in analyzing security logs and reports, extracting valuable insights, and enabling automated threat detection and response.
Implementation Considerations for AI-Driven Security Automation
Implementing AI-driven security automation requires careful consideration of various factors, including data quality and security, infrastructure requirements, and integration with existing security systems. High-quality, reliable data is essential to train effective AI models. Ensuring data security and privacy is paramount to avoid potential breaches and comply with regulatory requirements. Proper infrastructure is needed to support the processing power and storage capacity required by AI systems.
Integrating AI solutions seamlessly with existing security systems is also critical. Careful planning and testing are necessary to ensure smooth operation and avoid disruptions to existing security workflows. Furthermore, organizations must consider the need for ongoing maintenance, retraining, and updates to ensure that AI systems remain effective and aligned with evolving threat landscapes.
Challenges and Future Trends in AI Security Automation
While AI-driven security automation offers significant advantages, there are challenges that need addressing. One major challenge is the potential for bias in AI models, which can lead to inaccurate or discriminatory outcomes. Ensuring fairness and accountability in AI systems is crucial to maintain trust and avoid unintended consequences. Another challenge lies in the need for skilled personnel to manage and maintain these sophisticated systems, requiring investment in training and upskilling initiatives.
Looking ahead, the future of AI security automation promises even greater advancements. Expect to see increased integration with cloud-based security platforms, the development of more sophisticated AI models capable of handling increasingly complex threats, and the emergence of new AI-driven security tools that address emerging threats, like quantum computing, and the metaverse. This evolution will continue to enhance the effectiveness and efficiency of security operations.
Optimizing Security Operations and Reducing Manual Tasks

Improving Incident Response
A robust incident response plan is crucial for minimizing the impact of security breaches. Proactive measures, such as regular vulnerability assessments and penetration testing, are essential for identifying weaknesses before malicious actors exploit them. This proactive approach allows organizations to patch vulnerabilities and strengthen their defenses, significantly reducing the risk of successful attacks. Developing and regularly testing incident response procedures empowers teams to effectively contain and resolve incidents, minimizing downtime and data loss.
Incident response plans should be tailored to specific organizational needs and regularly updated to reflect evolving threats and technologies. Clear communication protocols are vital during an incident, ensuring that all relevant personnel are informed and appropriately engaged in the response. Effective communication can prevent confusion and ensure a coordinated approach to mitigating the damage and restoring normal operations as quickly as possible.
Enhancing Security Awareness Training
Investing in comprehensive security awareness training programs is critical for empowering employees to become the first line of defense against cyber threats. These programs should cover various aspects of cybersecurity, including phishing awareness, safe password practices, and recognizing suspicious emails or websites. By equipping employees with the knowledge and skills to identify and report potential threats, organizations can significantly reduce the likelihood of successful attacks.
Security awareness training should be ongoing and tailored to the specific roles and responsibilities of employees. This ensures that employees are consistently updated on the latest threats and best practices. Regularly updating training materials and incorporating real-world examples can make learning more engaging and effective, leading to improved overall security posture.
Implementing Advanced Security Technologies
Leveraging advanced security technologies can significantly bolster your organization's defenses against sophisticated cyber threats. Implementing intrusion detection and prevention systems (IDS/IPS) can help proactively identify and block malicious traffic. This proactive approach can prevent attacks from reaching sensitive systems and data.
Utilizing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to gain unauthorized access. The implementation of robust endpoint security solutions, such as antivirus and antimalware software, can also protect individual devices from various threats. This layered approach to security is crucial for defending against today's complex and evolving threat landscape.
Strengthening Network Security
A strong network security infrastructure is the bedrock of any robust cybersecurity strategy. Implementing robust firewalls and network segmentation strategies can limit the scope of potential damage if a breach occurs. These measures help contain the spread of malicious activity within the network.
Regularly reviewing and updating security policies and procedures for network access and usage is essential. This ensures that only authorized personnel have access to sensitive data and resources. Implementing strong access controls and regular security audits of network configurations are crucial for maintaining a secure network environment.
Enhancing Security Visibility and Analysis

Improving Threat Detection
Implementing robust security measures is crucial for safeguarding sensitive data and systems from malicious actors. A critical component of this process is enhancing security visibility, which allows organizations to gain a comprehensive understanding of their security posture. This improved visibility enables proactive identification of potential threats before they can cause significant damage. By meticulously monitoring network traffic and system logs, security teams can pinpoint suspicious activities and respond effectively. This proactive approach ultimately strengthens the overall security architecture.
Advanced threat detection methods, such as machine learning algorithms and behavioral analytics, can significantly improve the accuracy and efficiency of threat identification. These tools can analyze vast amounts of data to identify patterns and anomalies that might indicate malicious activity. This ability to identify threats in real-time significantly reduces the time needed to respond to security incidents, minimizing potential damage.
Strengthening Security Controls
Implementing and maintaining robust security controls is paramount to protect against evolving cyber threats. These controls encompass a wide range of measures, including firewalls, intrusion detection systems, and access controls. Effective security controls act as the first line of defense against unauthorized access and malicious activities. Regularly reviewing and updating these controls is essential to ensure that they remain aligned with current threats and vulnerabilities.
Furthermore, security awareness training for employees is a vital component of a comprehensive security strategy. Educating employees about phishing scams, social engineering tactics, and other common cyber threats can significantly reduce the risk of successful attacks. Empowering employees with the knowledge and skills to identify and report suspicious activities strengthens the overall security posture of the organization.
Enhancing Incident Response Capabilities
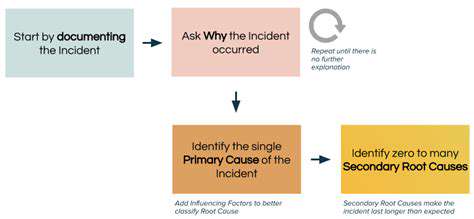
Developing and regularly testing incident response plans is critical for mitigating the impact of security breaches. A well-defined plan outlines the procedures to follow in case of a security incident, including steps for containment, eradication, recovery, and post-incident analysis. This proactive approach allows organizations to respond effectively and efficiently to security incidents, minimizing the potential disruption and damage caused. Having a clear and well-practiced incident response plan is crucial to maintaining business continuity and minimizing the financial and reputational consequences of security breaches.
A robust incident response process also includes the critical step of conducting post-incident analysis to identify the root cause of the incident. This analysis helps organizations learn from their mistakes and implement preventative measures to avoid similar incidents in the future. Thorough analysis and lessons learned from previous breaches are invaluable in strengthening security controls and enhancing overall security posture.