The Psychology and Economics of Ransom Payment Decisions
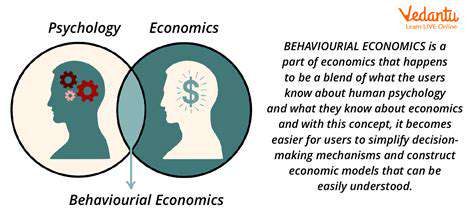
The Role of Cognitive Biases
When examining ransomware payment choices, it's crucial to recognize how cognitive biases shape decision-making. These mental shortcuts, while normally helpful, can distort judgment during high-pressure ransomware incidents. Take confirmation bias - victims often fixate on information supporting payment while ignoring counterarguments, creating dangerous tunnel vision. This psychological trap can lead to reckless financial decisions with lasting consequences.
The availability heuristic also plays a significant role, as people judge likelihoods based on memorable examples. If recent news highlights successful data recovery after payment, victims may overestimate this outcome's probability. This skewed perception frequently results in unnecessary payouts that further fund criminal enterprises.
The Behavioral Economics of Risk Assessment
Behavioral economics reveals fascinating patterns in how ransomware victims evaluate risk. Loss aversion - where potential losses feel more painful than equivalent gains - often pushes organizations toward payment. The immediate fear of data loss frequently outweighs rational calculations about the long-term implications of funding cybercrime.
Social Dynamics in Crisis Response
Group dynamics significantly influence ransomware responses. When multiple stakeholders are involved, the desire for consensus can override individual doubts, leading to hasty payment decisions. Executives often feel pressure to follow industry peers' examples, even when evidence suggests alternative approaches might be better.
Emotional Factors in Digital Extortion
The psychological toll of ransomware attacks cannot be overstated. The stress of operational disruption combined with anxiety about data loss frequently triggers fight-or-flight responses that impair clear thinking. Organizations that implement emotional regulation techniques beforehand tend to navigate these crises more effectively.
Presentation Effects on Decision-Making
How attackers frame their demands significantly impacts victim responses. Demands presented as data recovery fees rather than ransoms see higher compliance rates. Similarly, initial ransom figures serve as powerful anchors - even when negotiable, they establish psychological reference points. These subtle manipulations often lead to payment amounts that exceed what rational analysis would justify.
The Role of Cryptocurrency in Facilitating Ransom Payments

Decentralization's Dual Nature
Cryptocurrency networks operate without central oversight, creating both advantages and challenges. While this structure prevents single-point failures, it also enables pseudonymous transactions ideal for illicit activities. The very features that promote financial freedom also create perfect conditions for ransomware ecosystems to flourish.
Market Volatility Considerations
The fluctuating value of cryptocurrencies adds another layer of complexity to ransom payments. Victims must consider not just the demanded amount, but potential value changes during the payment process. This financial uncertainty forces organizations to make time-sensitive decisions with incomplete information.
Security Paradoxes
While blockchain technology offers robust transaction security, the surrounding infrastructure remains vulnerable. From wallet hacks to exchange breaches, the cryptocurrency ecosystem presents numerous attack vectors that both criminals and victims must navigate. These security challenges complicate an already stressful payment process.
Banking System Disruption
Cryptocurrencies have forced traditional financial institutions to confront new realities. Some banks now offer cryptocurrency services, while others actively block suspicious transactions. This evolving landscape creates both obstacles and opportunities for organizations facing ransom demands.
Regulatory Challenges
The lack of consistent global cryptocurrency regulations produces legal gray areas. Some jurisdictions prohibit ransom payments entirely, while others have no clear policies. This regulatory patchwork leaves organizations uncertain about compliance risks when considering payments.
Technological Evolution
As blockchain technology advances, new features like smart contracts and privacy coins emerge. These developments continuously reshape the ransomware landscape, creating an arms race between attackers and defenders. Organizations must stay informed about these changes to develop effective response strategies.
Environmental Considerations
The energy-intensive nature of some cryptocurrency networks raises ethical questions. Ransom payments indirectly contribute to this environmental impact, adding another dimension to the already complex decision-making process. Some organizations now factor this into their response calculations.