Establishing Realistic RTO and RPO Values
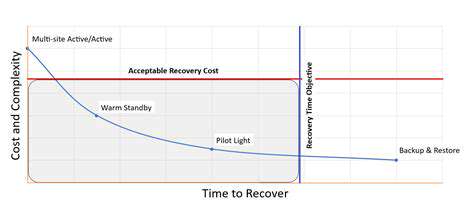
Understanding RTO and RPO
In the realm of disaster recovery, RTO (Recovery Time Objective) stands as a critical benchmark. It represents the maximum duration an organization can tolerate for restoring essential operations following a disruption. This metric directly correlates with financial and operational resilience, making its accurate definition paramount for business continuity. Without proper RTO determination, companies risk prolonged downtime with cascading consequences.
Equally vital is RPO (Recovery Point Objective), which quantifies the acceptable threshold of data loss post-disaster. Unlike RTO's focus on time, RPO addresses data integrity, establishing how much information a business can afford to lose without catastrophic impact. These dual metrics form the foundation of any robust disaster recovery framework.
Defining Realistic RTO Goals
Crafting achievable RTO targets demands a meticulous examination of business operations. Leaders must map critical workflows, identify single points of failure, and understand interdependencies across departments. The healthcare sector, for instance, might prioritize faster RTOs for patient management systems compared to administrative functions.
Financial implications should drive RTO decisions as much as technical considerations. A retail operation during peak season would require significantly tighter RTOs than during off-peak periods. This dynamic approach ensures resources aren't wasted on unnecessarily aggressive targets while protecting revenue streams.
Determining Acceptable RPO Levels
Data valuation forms the cornerstone of RPO determination. Organizations must classify data by criticality - transactional records often demand near-zero RPOs, while archived materials might tolerate longer intervals. The cost of data recreation frequently exceeds the investment in robust backup solutions, making this analysis financially prudent.
Regulatory landscapes dramatically influence RPO thresholds. Financial institutions governed by SEC regulations implement stricter RPOs than manufacturing firms. Compliance requirements often establish non-negotiable baselines that must be incorporated into recovery strategies.
Considering Business Impact Analysis
A comprehensive Business Impact Analysis (BIA) transforms recovery planning from guesswork to science. This process quantifies potential losses across operational, financial, and reputational dimensions. Effective BIAs employ scenario testing to evaluate how different disruption durations and data loss scenarios would affect organizational viability.
Implementing Backup and Recovery Strategies
Modern backup solutions have evolved beyond simple data copying. Today's systems incorporate incremental backups, geo-redundant storage, and automated verification processes. The emergence of immutable backups has revolutionized RPO achievement, providing cryptographic protection against ransomware and malicious deletions.
Hybrid cloud architectures now enable cost-effective RTO optimization, allowing critical systems to failover to cloud environments while maintaining on-premises control over sensitive data. This balanced approach satisfies both performance requirements and security concerns.
Testing and Validation of Plans
Tabletop exercises have proven invaluable for stress-testing recovery plans without disrupting production. These simulations reveal hidden dependencies and process gaps that documentation might overlook. Surprise disaster drills conducted during off-hours provide the most authentic assessment of team readiness and system resilience.
Monitoring and Continuous Improvement
Advanced monitoring tools now offer real-time RTO/RPO compliance tracking, alerting teams the moment backup windows are missed or recovery tests fall behind schedule. Machine learning algorithms can predict potential compliance breaches before they occur, enabling proactive adjustments to recovery strategies.
The integration of disaster recovery metrics into overall business performance dashboards ensures executive visibility and maintains organizational focus on resilience. This alignment between technical recovery capabilities and business objectives creates a culture of continuous preparedness.











