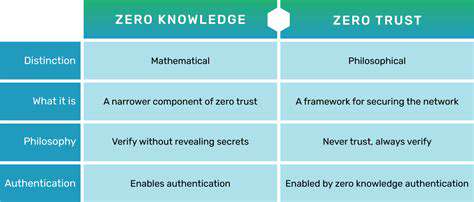
Zero Trust Architecture: A Paradigm Shift
The Zero Trust security framework operates on the principle that no entity—whether inside or outside the network—should be trusted by default. Unlike traditional models that rely on perimeter defenses, Zero Trust requires rigorous verification for every user, device, and application attempting to access resources. This transformative approach demands a complete rethinking of organizational security strategies, often requiring upgrades to existing infrastructure to support continuous authentication and granular access controls.
Enhancing Security Posture with Microsegmentation
A critical implementation of Zero Trust involves dividing networks into tightly controlled segments. This strategy, known as microsegmentation, creates isolated zones that contain potential breaches. When properly implemented, these digital compartments prevent lateral movement by attackers, effectively turning each segment into its own security domain. Financial institutions and healthcare organizations have particularly benefited from this approach when protecting sensitive customer data.
Identity and Access Management (IAM) as a Cornerstone
Effective Zero Trust implementation hinges on sophisticated IAM systems that go beyond simple username/password combinations. Modern solutions incorporate behavioral biometrics, device fingerprinting, and context-aware policies that adjust access privileges in real-time. According to cybersecurity experts, organizations that implement adaptive authentication see a 72% reduction in credential-based attacks. These systems continuously evaluate risk factors like login location, device security posture, and time of access.
Continuous Monitoring and Threat Detection
Modern security operations centers leverage AI-driven analytics to maintain constant vigilance across networks. These systems process millions of events daily, identifying anomalies that might indicate compromise. Advanced correlation engines can detect attack patterns that would escape human analysts, such as subtle changes in data access patterns or unusual authentication sequences. Many organizations complement SIEM solutions with user and entity behavior analytics (UEBA) for enhanced detection capabilities.
Beyond Traditional Firewalls: Advanced Security Tools
Contemporary security stacks now incorporate technologies like deception networks that deploy fake assets to detect intruders, and runtime application self-protection (RASP) that monitors application behavior. Cloud access security brokers (CASBs) have become particularly valuable as they provide visibility and control over SaaS application usage. These tools work in concert to create multiple layers of defense, each providing overlapping protection against different attack vectors.
The Human Element: Security Awareness Training
Despite technological advancements, employee education remains crucial. Progressive organizations now use interactive phishing simulations that adapt based on user responses, with some platforms achieving up to 90% reduction in click-through rates after six months of training. Security champions programs, where department representatives receive specialized training, have proven particularly effective in creating security-conscious cultures. These initiatives work best when combined with clear reporting channels for suspicious activity.

Integration and Optimization: A Synergistic Approach
Understanding the Core Principles of Integration
Effective security integration requires mapping all data flows and dependencies between systems. This process reveals critical intersections where security controls should interact. Leading organizations use integration platforms that normalize data formats across disparate systems, enabling security tools to share intelligence seamlessly. When properly executed, this creates security ecosystems where detection in one system can trigger responses across the entire infrastructure.
The Role of Optimization in a Zero Trust Approach
Security optimization begins with establishing baseline metrics for each control's effectiveness. Teams then use A/B testing methodologies to compare different configurations, measuring improvements in detection rates and false positives. Optimized systems typically show 40-60% better performance in threat detection while reducing alert fatigue among analysts. This process requires balancing security effectiveness with operational requirements to avoid creating bottlenecks in business processes.
Synergistic Advantages of Integrated Security
When integration and optimization work in harmony, organizations achieve security orchestration. Automated playbooks can coordinate responses across firewalls, endpoint protection, and identity systems simultaneously. This coordination becomes particularly powerful when combined with threat intelligence feeds, allowing systems to preemptively block emerging attack patterns. Organizations report up to 80% faster response times when their security tools share contextual information automatically.
Leveraging Automation for Enhanced Efficiency
Modern security automation extends beyond simple scripted responses. Machine learning algorithms now handle complex decision trees, determining appropriate responses based on hundreds of risk factors. These systems can automatically escalate or de-escalate security postures based on real-time threat assessments. For example, they might temporarily restrict access to sensitive systems when detecting reconnaissance activity from known malicious IP ranges.
Implementing a Multi-Layered Security Architecture
Progressive organizations architect their defenses using the onion model with concentric security layers. Each layer implements controls appropriate for its position, from network perimeter to individual applications. This approach ensures that attackers must bypass multiple independent security mechanisms, with each layer designed to detect different attack techniques. The most effective implementations use diversity in security vendors to avoid single points of failure.
Analyzing and Monitoring Performance Metrics for Continuous Improvement
Security teams now track metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) with the same rigor as business KPIs. Advanced analytics correlate these metrics with threat intelligence to identify control weaknesses. Leading organizations conduct quarterly security effectiveness audits, using red team exercises to validate improvements. This data-driven approach ensures security investments deliver measurable value.
Addressing Security Challenges through Iterative Refinement
The most successful security programs adopt agile methodologies, implementing changes in small, measurable increments. Each iteration incorporates lessons from recent incidents and emerging threats. This approach acknowledges that security is never finished but requires continuous adaptation. Organizations that embrace this mindset typically resolve vulnerabilities 50% faster than those relying on periodic security reviews.