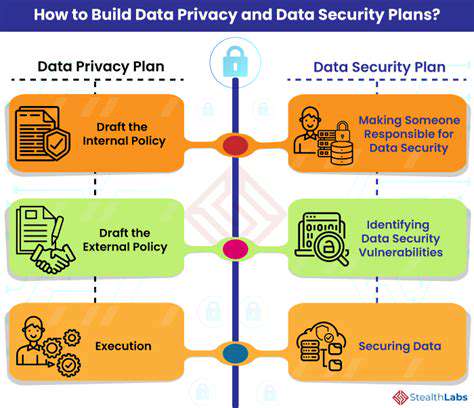
Creating Realistic Digital Representations
Developing convincing digital facsimiles requires meticulous attention to detail and comprehensive environmental analysis. Security architects must study network architectures, application behaviors, and data flows with precision to craft indistinguishable replicas. The authenticity of these decoys directly correlates with their effectiveness—imperfections or inconsistencies may alert sophisticated attackers to the ruse. Through careful emulation of production environments, including the recreation of typical system vulnerabilities, these digital facades become powerful tools for threat detection and analysis.
Leveraging AI for Enhanced Detection
Modern security systems incorporate advanced machine learning capabilities to analyze interactions with decoy assets. These intelligent systems excel at detecting subtle behavioral anomalies that might escape traditional monitoring solutions. By processing vast amounts of interaction data, AI algorithms can establish baseline patterns and flag deviations with remarkable accuracy. This technological synergy between deception techniques and artificial intelligence creates a dynamic defense mechanism that evolves alongside emerging threats.
Detecting Anomalies and Unusual Activity
Deception technologies shine brightest in their ability to surface suspicious behavior that would otherwise blend into normal network activity. The artificial environment created by mimic assets provides a controlled space where every interaction can be treated as potentially malicious. Security teams benefit from clear signals amidst the noise of everyday operations, as any engagement with decoy systems immediately raises red flags. This approach dramatically reduces false positives while ensuring genuine threats receive immediate attention.
Improving Security Posture and Incident Response
The insights gained from observing attacker behavior within controlled decoy environments directly enhance organizational security strategies. Security teams can study adversary techniques in real-time, refining their response protocols based on actual threat actor behavior. This hands-on intelligence allows for the development of precisely targeted defensive measures rather than relying on generic security templates. The resulting security framework becomes both more effective and efficient, capable of anticipating and neutralizing threats before they impact genuine assets.
Gathering Valuable Data about Attacker TTPs
Deception technologies create unprecedented opportunities for collecting detailed information about attacker methodologies. Every interaction with mimic systems contributes to a growing knowledge base of tactical approaches, preferred exploitation techniques, and post-compromise behaviors. This intelligence proves invaluable for developing predictive security models that can anticipate future attack vectors based on observed patterns. Security teams transition from reactive postures to proactive stances, staying ahead of emerging threats through comprehensive behavioral analysis.
Integration with Existing Security Infrastructure
Successful implementation of deception technologies requires thoughtful incorporation into the broader security ecosystem. Decoy systems must seamlessly interact with SIEM platforms, threat intelligence feeds, and incident response workflows to maximize their effectiveness. This integration ensures that alerts from mimic environments trigger appropriate investigative and containment procedures. When properly synchronized with other security components, deception technologies amplify the capabilities of the entire defense infrastructure, creating a security multiplier effect.
Education systems are evolving to accommodate the fact that no two students learn identically. Customized learning trajectories acknowledge individual academic strengths, challenges, preferred methods of learning, and personal objectives. This paradigm shift rejects standardized approaches, instead cultivating a more stimulating and productive educational journey. The focus lies in modifying instructional content to align with each learner's distinct requirements, thereby optimizing their academic growth.
Enhancing Security Operations and Reducing Costs

Improving Incident Response
A robust incident response plan forms the backbone of effective cybersecurity operations. Preventative measures like systematic vulnerability scanning and controlled penetration testing allow organizations to identify and remediate weaknesses before exploitation occurs. Establishing clear response protocols—including communication chains and escalation pathways—empowers security teams to act decisively during critical events. This operational preparedness minimizes business disruption while maximizing containment effectiveness.
Successful incident management depends on rapid threat identification and isolation, preventing minor incidents from escalating into full-scale breaches. Layered detection systems incorporating network monitoring, behavioral analytics, and real-time alerting create multiple opportunities to intercept malicious activity. The speed and accuracy of response actions often determine the ultimate impact of security events on organizational operations.
Strengthening Access Controls
Modern access management strategies extend far beyond basic password requirements. Implementing context-aware authentication systems that evaluate multiple risk factors significantly improves protection for sensitive resources. These adaptive controls consider device health, location patterns, and behavioral biometrics to make real-time access decisions, creating dynamic barriers against credential-based attacks.
Implementing Security Awareness Training
Human factors remain among the most challenging security vulnerabilities to address. Effective training programs move beyond annual compliance checkboxes to create continuous learning experiences. Role-specific scenarios and regular simulation exercises help employees develop practical security instincts that translate to real-world situations. This investment in human firewalls complements technical controls and creates organizational resilience.
Security culture develops through consistent reinforcement and practical application. Interactive training modules that evolve with the threat landscape ensure employees maintain awareness of current attack methodologies. Gamification elements and positive reinforcement mechanisms can significantly improve engagement and knowledge retention.
Enhancing Data Loss Prevention (DLP)
Contemporary data protection strategies employ intelligent classification systems to automatically identify and protect sensitive information. These solutions combine content analysis with contextual understanding to make nuanced decisions about data handling. Advanced DLP implementations can detect potential policy violations in real-time, enabling security teams to intervene before sensitive data leaves organizational control.
Enhancing Network Security
Modern network defense architectures incorporate zero-trust principles that verify every connection attempt regardless of origin. Micro-segmentation strategies create granular security zones that limit lateral movement during potential breaches. Continuous traffic analysis and anomaly detection provide visibility into network activities, while encrypted communications ensure data confidentiality in transit.
Next-generation firewalls equipped with deep packet inspection and application-aware filtering offer enhanced protection against sophisticated network-based attacks. Regular architecture reviews and penetration testing validate security configurations and identify potential weaknesses before they can be exploited.
Improving Security Monitoring and Logging
Advanced security operations centers leverage machine learning to process vast volumes of security telemetry. These intelligent systems identify meaningful patterns amidst the noise, allowing analysts to focus on genuine threats. Unified logging architectures ensure comprehensive visibility across all IT environments, from on-premises systems to cloud workloads.
Behavioral analytics platforms establish baseline activity patterns for users and systems, enabling detection of subtle deviations that may indicate compromise. Integrating threat intelligence feeds with monitoring systems creates context-aware detection capabilities that recognize known attack patterns and emerging threats. This combination of broad visibility and intelligent analysis significantly reduces detection times for security incidents.
Developing a Security Culture
Organizational security maturity grows when protection becomes a shared responsibility across all departments. Leadership commitment to security priorities sets the tone for enterprise-wide engagement. Practical security champions programs empower employees at all levels to contribute to protection efforts while serving as local resources for security questions.
Establishing clear reporting channels for security concerns encourages proactive identification of potential issues. Recognition programs that reward secure behaviors reinforce positive security practices. This cultural transformation creates an environment where security considerations become integrated into daily operations rather than viewed as external constraints.