Zero Trust: Defining the Paradigm Shift
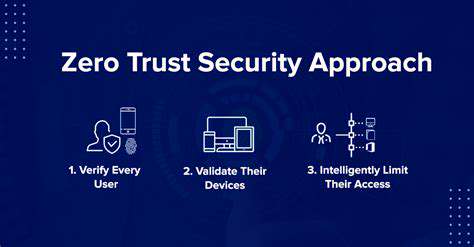
The Zero Trust model represents cybersecurity's most significant evolution since firewalls. Its core principle - never trust, always verify - applies equally to CEOs logging in from headquarters and contractors accessing systems remotely. This approach proves particularly effective against lateral movement, containing breaches to small network segments even when credentials are compromised.
Implementing Zero Trust: Beyond the Basics
Successful deployment requires mapping every data flow in an organization. A pharmaceutical company might discover its research data traverses sixteen unintended pathways. The implementation process often reveals surprising shadow IT systems that require integration or decommissioning.
Access Control and Authentication: The Cornerstones of Zero Trust
Modern MFA solutions now incorporate behavioral biometrics, analyzing typing patterns and mouse movements. Some financial institutions have reduced account takeovers by 92% using these continuous authentication methods alongside traditional credentials.
Micro-segmentation: Isolating the Attack Surface
A hospital demonstrated micro-segmentation's value by containing a ransomware attack to non-clinical systems, allowing uninterrupted emergency room operations. Their network design treated each MRI machine as its own secure zone with individual access policies.
Continuous Monitoring and Threat Detection: Proactive Security
Next-gen SIEM systems now correlate data from physical access logs, badge swipes, and even building management systems. One energy provider detected an intruder by spotting anomalous HVAC usage in a restricted server room during off-hours.
Data Loss Prevention (DLP): Protecting Sensitive Information
Advanced DLP now uses natural language processing to identify sensitive content regardless of format. A defense contractor's system recently blocked an attempt to exfiltrate classified data hidden in cat meme metadata.
The Human Element: Education and Awareness
Behavioral psychology techniques have transformed security training. Instead of boring lectures, companies use capture the flag exercises where employees compete to spot phishing attempts in simulated environments. One manufacturer saw a 75% reduction in successful phishing after implementing this approach.
Implementing Zero Trust in Critical Infrastructure: Key Considerations

Implementing Zero Trust in Critical Infrastructure: A Multi-Layered Approach
Securing critical systems requires balancing security with operational continuity. A regional power grid operator maintains separate authentication tiers - engineers can bypass some MFA steps during emergencies while logging every action for post-event auditing.
Establishing Strong Access Controls
One airport's access system combines facial recognition with RFID-enabled uniforms, ensuring only authorized personnel can enter sensitive areas like fuel depots. Their system automatically revokes access when uniforms are reported lost or stolen.
Continuous Monitoring and Threat Detection
Advanced anomaly detection now monitors industrial control systems for subtle timing variations that might indicate tampering. A water utility detected compromised valves by analyzing millisecond deviations in normal operation cycles.
Automated Response Mechanisms
When a gas pipeline's sensors detected suspicious pressure changes, automated systems isolated the segment within 47 milliseconds while alerting engineers. This rapid response prevented what could have been an environmental disaster.
Segmentation and Isolation of Networks
A smart city project implemented seven-layered segmentation for its traffic management systems. Even if attackers compromise traffic lights, they can't access emergency vehicle routing systems or surveillance networks.
Regular Vulnerability Assessments and Patching
One nuclear facility runs continuous vulnerability scans during planned outages, patching systems in a carefully orchestrated sequence that maintains safety redundancies throughout the process.
Employee Training and Awareness Programs
A maritime port's security team uses augmented reality to train crane operators on recognizing cyber-physical threats. The system projects virtual attack scenarios onto real equipment, creating muscle memory for emergency responses.