Inventory Management Best Practices
Maintaining an accurate inventory is the lifeblood of successful business operations, whether for multinational corporations or small local shops. When companies implement streamlined inventory tracking methods, they gain the ability to monitor product movement in real-time, anticipate market fluctuations, and prevent both shortages and wasteful surpluses. Strategic grouping of inventory items creates a framework that enhances supply chain fluidity while boosting productivity across all operational levels. Mastering these inventory techniques often translates directly to reduced expenses and improved profit margins.
Adopting comprehensive inventory protocols represents a critical investment in long-term financial health. The ideal system captures detailed information about each product throughout its entire lifecycle - from initial procurement to final sale or retirement. Maintaining precise documentation enables more accurate demand forecasting and smarter procurement strategies.
Categorization Strategies for Products
Developing an effective product classification system demands careful consideration of multiple factors. Businesses might organize items by physical characteristics, market segments, or operational roles within their product ecosystem. A logical classification structure provides clarity about inventory composition and enables focused evaluation of specific merchandise categories. This granular visibility supports more accurate predictions and optimal resource distribution.
Classification approaches vary significantly across industries. While clothing retailers might sort products by seasonal collections, industrial manufacturers may categorize components by production phases. The key lies in designing a system that aligns perfectly with your company's operational requirements and business objectives.
Importance of Accurate Inventory Data
Precise inventory records form the bedrock of intelligent business decisions. These records empower organizations to maintain optimal stock quantities, predict upcoming demand fluctuations, and refine their ordering processes. This accuracy proves particularly valuable for preventing shortages that could result in missed sales opportunities and dissatisfied clients. Reliable data facilitates superior demand prediction and strategic purchasing choices, leading to substantial cost reductions.
Consistent verification and updating of inventory information remains an ongoing necessity. While this may require specialized staff or technological solutions, the investment yields significant returns. With meticulous record-keeping, businesses can guarantee product availability when needed, ensuring uninterrupted operations and meeting customer expectations consistently.
Analyzing Products for Optimal Stock Levels
Thorough examination of product categories is indispensable for determining ideal inventory quantities. This evaluation should incorporate historical performance metrics, cyclical demand patterns, and market projections. By understanding these variables, companies can make informed predictions about future requirements while avoiding the pitfalls of excessive or inadequate stock levels. This forward-thinking methodology reduces warehousing expenses and mitigates financial risks tied to surplus inventory.
Studying sales trends and consumption patterns allows businesses to calibrate their inventory precisely for maximum financial performance. While this analysis may require dedicated analytical tools, the operational efficiencies and profit potential justify the investment. Periodic reassessment of inventory metrics, particularly for core product lines, remains crucial for refining stock management practices and enhancing financial returns.
Robust Data Backup and Recovery Procedures: Building an Escape Route
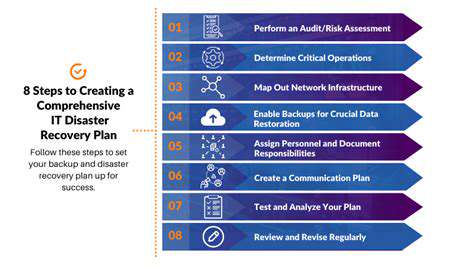
Robust Data Backup Strategies
Establishing comprehensive data preservation measures represents a critical priority for organizations seeking to protect their vital information from numerous potential threats, including human error and catastrophic system breakdowns. A meticulously crafted backup protocol guarantees operational resilience and significantly reduces recovery time following disruptive incidents. This entails scheduled duplication of essential data, secure storage in geographically diverse locations, and implementation of thorough contingency plans.
Selecting the optimal backup methodology requires careful consideration. Options range from complete system copies to selective incremental updates, each offering distinct benefits and limitations. The decision should reflect both the nature of your data assets and your organization's risk management philosophy. Determining appropriate backup frequency should account for data criticality and the company's tolerance for potential information loss.
Effective Data Recovery Procedures
A well-structured data restoration process serves as the backbone of any reliable backup system. This involves creating detailed protocols for data retrieval following loss events. Documented recovery guidelines should specify exact restoration sequences, ensuring rapid and effective data rehabilitation. Clearly defined processes and validated recovery methods minimize operational downtime and maintain business continuity during critical situations.
Regular testing of recovery capabilities remains essential for verifying system reliability. Periodic validation of backup integrity and restoration procedures confirms data recoverability and identifies potential weaknesses. These proactive measures allow organizations to refine their disaster response strategies before facing actual emergencies.
Security Considerations for Data Backups
Information protection represents a fundamental aspect of backup system design. Safeguarding backup repositories against unauthorized intrusion while maintaining data privacy and accuracy is paramount for ensuring business stability. Implementing stringent protective measures - including advanced encryption, strict access limitations, and routine security evaluations - forms the foundation of backup security. These precautions prevent data breaches while preserving information authenticity.
Physical storage security demands equal attention. Backup archives should reside in protected facilities, preferably at separate geographical locations, to guard against environmental hazards or criminal activity. Continuous refinement of security standards remains vital for sustaining robust data protection measures. Additional safeguards like multi-factor authentication further strengthen backup system defenses.