Identifying the Key Challenges
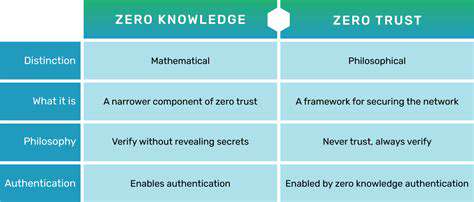
Defining Zero Trust
Zero Trust flips traditional security on its head by treating every access request as a potential threat until proven otherwise. Gone are the days of assuming safety behind a corporate firewall. Every user, device, and connection must earn trust continuously through rigorous verification. This paradigm shift creates both opportunities and obstacles for organizations transitioning from legacy systems.
Establishing Trust Boundaries
Drawing the digital equivalent of a medieval castle's walls presents unique challenges in today's fluid work environments. Security teams must map out an ever-changing landscape of access points while balancing productivity needs. The real art lies in creating dynamic boundaries that adapt to new SaaS applications, BYOD policies, and remote work arrangements without compromising security. Regular audits become essential as cloud infrastructure evolves.
Implementing Strong Authentication and Authorization
The password's days as sole gatekeeper are numbered. Modern authentication requires multiple proof points - something you know, something you have, and something you are. Biometric verification and hardware security keys are becoming standard requirements rather than premium options. Authorization systems now demand context-aware decisions, evaluating factors like location, device health, and time of access alongside traditional role-based permissions.
As authentication methods multiply, user experience can't become collateral damage. IT departments walk a tightrope between ironclad security and employee frustration thresholds. The most successful implementations employ adaptive authentication that increases requirements based on perceived risk while minimizing hurdles for routine access.
Managing the Complexity of Data and Policies
Zero Trust generates a firehose of security telemetry that can overwhelm traditional monitoring tools. Security operations centers now require AI-assisted analytics to separate genuine threats from false alarms in mountains of log data. Policy management has evolved into a specialized discipline requiring dedicated staff and purpose-built software platforms. Version control for security rules becomes as critical as it is for application code.
Compliance adds another layer of complexity, with regulations often lagging behind technical realities. Organizations must interpret broad mandates like GDPR through a Zero Trust lens while maintaining audit trails that satisfy multiple regulatory frameworks simultaneously.
Overcoming Resistance to Change
Human nature favors convenience over security, making cultural transformation the steepest hurdle. Security teams encounter pushback from executives worried about productivity and employees annoyed by additional login steps. Successful adoption requires framing Zero Trust as an enabler rather than an obstacle - the digital equivalent of seatbelts rather than handcuffs. Phased rollouts with clear communication help smooth the transition.
The financial case presents another barrier, particularly for resource-constrained organizations. While upfront costs appear daunting, the potential savings from avoided breaches often justify the investment. Creative financing options like security-as-a-service models are making Zero Trust attainable for smaller enterprises.
Bridging the Skills Gap
Bridging the Gap in Essential Skills
The modern workplace resembles a high-stakes obstacle course where technical skills alone won't guarantee success. Employers increasingly value problem-solving agility - the ability to navigate unfamiliar challenges as they emerge. This skills mismatch leaves many qualified candidates on the sidelines while critical positions go unfilled. Targeted skills mapping can reveal where educational programs need realignment with industry needs.
Upskilling and Reskilling Initiatives
Continuous learning has shifted from career enhancement to career survival. Forward-thinking companies now treat training budgets as strategic investments rather than optional benefits. Micro-credentials and digital badges are creating flexible pathways for professionals to validate new competencies without traditional degrees. Partnerships between employers and training providers yield curriculum that's relevant from day one.
Curriculum Development and Alignment
Academic institutions face pressure to produce workplace-ready graduates despite rapidly changing requirements. Some pioneering schools have adopted agile curriculum development cycles that can incorporate new technologies within a semester. Capstone projects co-designed with industry partners give students hands-on experience with real business challenges while providing companies with fresh perspectives.
Promoting Lifelong Learning
The half-life of technical skills continues to shrink, making continuous upskilling mandatory. Innovative organizations are embedding learning opportunities into daily workflows through microlearning platforms and knowledge-sharing communities. Peer-to-peer mentoring programs leverage institutional knowledge while fostering collaborative cultures. Gamification techniques turn skill development into engaging challenges rather than obligatory training.
Addressing the Digital Divide
Technology access disparities create uneven playing fields in the digital economy. Rural communities and underserved urban populations often lack both infrastructure and digital literacy. Public-private partnerships are demonstrating success through initiatives like subsidized broadband and community technology centers. Mobile-first training approaches reach populations where traditional computer access remains limited.
Collaboration and Partnerships
No single entity can solve the skills gap alone. Regional workforce development consortia bring together employers, educators, and government agencies to align efforts. Sector-specific skills alliances create pipelines for high-demand fields while sharing the costs of training development. Apprenticeship programs combine classroom learning with paid work experience, benefiting both employers and career seekers.

Maintaining Continuous Monitoring and Adaptation
Defining Continuous Monitoring
Modern security monitoring resembles a 24/7 digital immune system rather than periodic checkups. Behavior analytics establish normal patterns for every user and device, enabling the detection of subtle anomalies that might indicate compromise. The most effective systems correlate data across multiple layers - network traffic, application usage, and endpoint behavior - to identify sophisticated attack patterns.
Adapting Security Policies in Real-Time
Static security rules can't keep pace with dynamic threats. Next-generation systems now incorporate feedback loops that automatically adjust controls based on observed activity. Machine learning models can detect emerging attack patterns and implement temporary countermeasures before human analysts identify the threat. This adaptive approach proves particularly valuable against zero-day vulnerabilities.
Implementing Automated Response Mechanisms
Response automation transforms security from reactive to proactive. When suspicious activity crosses defined thresholds, systems can automatically isolate affected devices, revoke credentials, or block malicious IPs. Playbooks ensure consistent response to common threats while preserving human oversight for complex incidents. The key lies in balancing automation speed with appropriate human review mechanisms.
Addressing the Challenges of Data Volume
Security teams increasingly turn to data lake architectures to manage monitoring data at scale. Advanced analytics extract meaningful signals from the noise through techniques like user behavior analytics and entity relationship mapping. Cloud-based solutions offer elastic scalability for organizations that experience seasonal spikes in monitoring data. Data retention policies must balance forensic needs with privacy regulations.
Maintaining Scalability and Performance
Distributed monitoring architectures prevent bottlenecks in large-scale deployments. Edge processing reduces central analysis loads by performing initial filtering at data collection points. Agent-based and agentless monitoring approaches each offer advantages depending on specific use cases and infrastructure types. Performance optimization requires continuous tuning as environments evolve.
User Training and Awareness Programs
Security awareness has moved beyond annual compliance videos. Leading organizations implement continuous engagement programs using simulated phishing, interactive training modules, and recognition for security-conscious behavior. Department-specific training addresses unique risk profiles - HR teams learn different security practices than development teams. Metrics track behavioral changes rather than just completion rates.