The Evolving Threat Landscape and the Need for Zero Trust
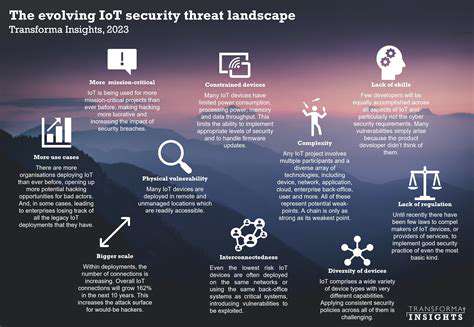
Understanding the Shifting Nature of Cyber Threats
The digital landscape is constantly evolving, and with it, the nature of cyber threats. Gone are the days of simple virus attacks; today's threats are far more sophisticated and targeted. Cybercriminals are increasingly employing advanced techniques, leveraging vulnerabilities in software and exploiting human weaknesses to gain unauthorized access to sensitive data. Understanding these evolving tactics is crucial for organizations to develop effective security strategies.
This evolution necessitates a proactive approach to cybersecurity. Organizations must move beyond reactive measures and embrace a culture of continuous learning and adaptation. Staying informed about emerging threats and proactively patching vulnerabilities are key to mitigating risks effectively.
The Rise of Targeted Attacks and Sophisticated Malware
The threat landscape is increasingly dominated by targeted attacks rather than broad-based campaigns. Cybercriminals are focusing on specific individuals or organizations, meticulously researching their systems and vulnerabilities to tailor attacks accordingly. This precision approach significantly increases the potential for success and the damage inflicted.
Sophisticated malware, often disguised as legitimate software or documents, is another significant concern. These advanced threats can bypass traditional security measures and remain undetected for extended periods, allowing attackers to exfiltrate sensitive data or disrupt critical operations. The ability to recognize and respond to these complex threats is a critical skill for modern cybersecurity professionals.
The Growing Importance of Data Protection and Privacy
Data breaches are a significant concern in today's interconnected world. The increasing reliance on digital systems and the vast amounts of data collected and processed daily create attractive targets for cybercriminals. Protecting this sensitive information and ensuring compliance with privacy regulations is paramount for organizations and individuals alike.
Data breaches can result in significant financial losses, reputational damage, and legal repercussions. A robust data protection strategy, encompassing strong encryption, access controls, and regular security audits, is essential for mitigating these risks and safeguarding sensitive data. Furthermore, organizations must prioritize educating their employees about data security best practices to prevent accidental data breaches.
The Human Element in Cybersecurity
Despite technological advancements, the human element remains a critical vulnerability in cybersecurity. Social engineering tactics, which exploit human psychology to trick individuals into revealing confidential information or performing actions that compromise security, are increasingly prevalent. Phishing emails, fraudulent websites, and malicious links are common examples of social engineering attacks.
Employee training and awareness programs are essential for mitigating the risks associated with human error and social engineering. Empowering employees with the knowledge and skills to recognize and report suspicious activities is crucial to preventing successful attacks. Regularly updated training and simulations can significantly improve the effectiveness of these programs.
Implementing Zero Trust in a Cloud-Native World

Understanding the Core Principles of Zero Trust
Zero Trust security is a crucial paradigm shift in modern cybersecurity, moving away from the traditional perimeter-based approach. Instead of assuming trust based on location, Zero Trust assumes no implicit trust for any user, device, or application, regardless of their location within or outside the network. This fundamental shift requires a comprehensive security posture that verifies every user and device access request before granting access to resources.
Implementing Zero Trust necessitates a shift in mindset, demanding a deep understanding of the organization's security needs and risk tolerance. This requires a detailed inventory of all systems and resources, along with a well-defined policy that dictates access control based on the principle of least privilege.
Establishing a Zero Trust Network Architecture
A robust Zero Trust network architecture involves several key components. These include a robust identity and access management (IAM) system, which authenticates and authorizes users and devices based on their attributes and permissions. A critical component is a microsegmentation strategy that isolates network segments to limit the impact of a breach.
Micro-segmentation, a key part of this architecture, divides the network into smaller, isolated segments. This approach restricts the propagation of threats if one segment is compromised.
Implementing Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a cornerstone of any Zero Trust implementation. It adds an extra layer of security beyond simple usernames and passwords, requiring users to provide multiple forms of verification, such as security tokens, biometric data, or one-time passwords. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
Leveraging Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems play a vital role in monitoring and analyzing security events in real-time. By collecting and correlating logs from various systems and applications, SIEMs can detect anomalies and potential threats, enabling proactive responses before they escalate into major incidents. They are essential for identifying and responding to security breaches quickly and efficiently.
Enforcing Least Privilege Access
The principle of least privilege is foundational to Zero Trust. This principle requires granting users only the minimum access rights necessary to perform their job functions. This significantly reduces the potential damage from a compromised account, as attackers will have limited access to sensitive data and resources.
Restricting access to sensitive data and critical systems based on the need-to-know principle is paramount to protecting your organization from unauthorized access. Implementing role-based access control (RBAC) is an effective way to achieve this.
Monitoring and Continuous Improvement
Zero Trust is not a one-time implementation; it's an ongoing process of monitoring, evaluating, and adapting to evolving threats. Regular security assessments and penetration testing are essential to identify vulnerabilities and weaknesses in the Zero Trust architecture. These assessments will help you stay ahead of potential threats and proactively address any gaps in security.
Continuous monitoring and improvement are crucial for maintaining the efficacy of a Zero Trust implementation. Regular updates to security policies and procedures, as well as incorporating new technologies, are essential to adapt to evolving threats and ensure the ongoing effectiveness of the security posture.






