
Implementing a Holistic Security Strategy
Understanding the Interconnected Nature of IoT Devices
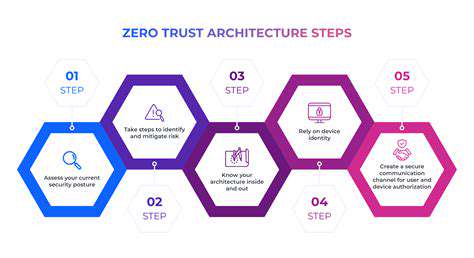
In the realm of critical infrastructure, the proliferation of interconnected Internet of Things (IoT) devices presents a complex security landscape. These devices, ranging from sensors monitoring water levels to controllers managing power grids, are often deployed without adequate security considerations. Understanding the intricate relationships between these devices and the broader infrastructure is paramount. A lack of visibility into these connections can create significant vulnerabilities, allowing malicious actors to exploit weaknesses in one device and potentially cascade the attack across the entire system.
Recognizing the interconnected nature of IoT devices is the first step towards developing a holistic security strategy. This includes mapping the communication pathways, identifying potential single points of failure, and proactively assessing the risk profile of each device based on its criticality to the overall infrastructure.
Prioritizing Device Security from the Ground Up
Implementing robust security measures right from the design phase of IoT devices is crucial. This means incorporating strong authentication mechanisms, encryption protocols, and regular security audits into the development process. By integrating security at the foundational level, organizations can significantly reduce the risk of vulnerabilities being exploited later on.
Furthermore, manufacturers must prioritize the lifecycle security of these devices. This includes providing clear and comprehensive documentation on security features, outlining patch management procedures, and establishing secure update channels. Devices with a long lifespan require particularly careful consideration, as they may be exposed to evolving security threats over time.
Establishing Robust Network Security Protocols
A comprehensive security strategy must encompass the network infrastructure supporting the IoT devices. This includes implementing firewalls, intrusion detection systems, and network segmentation to isolate critical systems and limit the impact of potential breaches. Regular network security audits are essential to identify vulnerabilities and ensure that security measures remain effective against evolving threats.
Utilizing encryption protocols across the network is critical. Protecting data in transit and at rest is essential to maintaining confidentiality, integrity, and availability. Implementing strong access controls and restricting unauthorized access to sensitive data are equally important components of a secure network architecture.
Developing Comprehensive Incident Response Plans
A holistic security strategy must include a well-defined incident response plan. This plan should outline procedures for detecting, containing, and recovering from security incidents. Regularly testing and updating the incident response plan ensures that the organization is prepared to handle any potential threat effectively.
Having dedicated personnel trained in incident response is crucial. These individuals should be equipped with the knowledge and tools to quickly identify and mitigate security breaches, minimizing downtime and damage to critical infrastructure. The plan should also involve external stakeholders, such as law enforcement and cybersecurity experts, to ensure a coordinated response.
Implementing Continuous Monitoring and Vulnerability Management
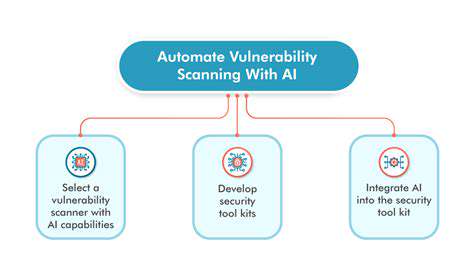
Maintaining a robust security posture requires continuous monitoring of IoT devices and the network infrastructure. Implementing security information and event management (SIEM) tools, and regularly scanning for vulnerabilities are essential components of this process. This continuous monitoring ensures that the organization remains proactive in identifying and addressing potential threats before they can cause significant harm.
Proactive vulnerability management is critical. Regularly updating device firmware, software, and security configurations will significantly reduce the attack surface. This includes implementing automated patching procedures and leveraging vulnerability management tools to identify and address weaknesses in a timely manner.
Employee Training and Awareness Programs
Human error is a significant factor in many security breaches. Implementing comprehensive employee training and awareness programs is therefore essential. These programs should educate employees on the importance of cybersecurity practices, such as strong password management, recognizing phishing attempts, and reporting suspicious activities. Regular training sessions reinforce security awareness and help build a security-conscious culture within the organization.
Empowering employees to report potential security threats is also vital. Creating a safe environment where employees feel comfortable reporting suspicious activities without fear of retribution is crucial. This encourages a proactive approach to security and fosters a collaborative environment in identifying and mitigating threats.
The Role of International Collaboration and Standards
International Collaboration for IoT Security Standards
International collaboration is crucial for establishing and maintaining robust IoT security standards. Different countries and regions often have varying levels of technological development, regulatory frameworks, and security priorities. A unified approach, fostered through international organizations and agreements, is essential to ensure a consistent level of security across diverse systems and applications. This collaboration is vital to prevent the development of fragmented and potentially vulnerable solutions.
Harmonized standards facilitate interoperability and reduce the risk of security breaches. Sharing best practices, threat intelligence, and vulnerability information among nations is critical for proactive security measures. This collective knowledge base strengthens the overall security posture of the global IoT ecosystem.
Establishing Global Security Frameworks
The development of comprehensive security frameworks, internationally recognized and adopted, is paramount. These frameworks must cover the entire lifecycle of IoT devices, from design and development to deployment and maintenance. They should incorporate guidelines for secure coding practices, vulnerability management, and incident response.
Standardization of Communication Protocols
Standardizing communication protocols is another key aspect of international collaboration. A lack of consistency in these protocols can create significant security vulnerabilities. International standards bodies can play a crucial role in developing and promoting secure communication protocols, ensuring that devices from different manufacturers can communicate securely without compromising the overall system.
This standardization will make it easier to identify and address vulnerabilities in communication protocols, leading to a more resilient and secure IoT ecosystem.
Addressing Data Privacy and Security
International collaboration is essential to harmonize data privacy and security regulations across borders. Different countries have different laws and regulations regarding data protection. A globally accepted framework for data handling in IoT systems, supported by international agreements, is needed to prevent data breaches and ensure compliance.
This framework should ensure the protection of sensitive data collected and transmitted by IoT devices and address the specific challenges posed by the interconnected nature of these devices.
Promoting Secure Development Practices
Promoting secure development practices throughout the entire IoT development lifecycle is a critical aspect of international collaboration. This involves establishing and sharing best practices for secure coding, risk assessment, and vulnerability testing. International collaboration can provide a platform to exchange knowledge and expertise, leading to a more secure and trustworthy IoT ecosystem.
Sharing Threat Intelligence and Vulnerability Information
Effective international collaboration demands the sharing of threat intelligence and vulnerability information. This collective effort will allow organizations to proactively address emerging threats and vulnerabilities. Establishing a global network for sharing such information is crucial to effectively combat sophisticated attacks and ensure the safety of IoT infrastructure.
Rapid dissemination of information about identified vulnerabilities is a key factor in mitigating their impact on critical infrastructure. This is a crucial element of global collaboration.
Enforcing Security Regulations and Standards
International collaboration is essential to enforce security regulations and standards. This includes establishing mechanisms for monitoring compliance, sanctioning non-compliance, and providing support for countries that are lagging behind in implementing these standards. Clear guidelines and penalties for non-compliance are necessary to encourage adoption and ensure the safety of the global IoT ecosystem.
International collaboration will provide a platform for countries to exchange best practices for enforcing regulations and standards, fostering a culture of security within the IoT industry.