The Role of Cybersecurity Professionals in Healthcare
As medical cyberthreats grow more sophisticated, healthcare institutions must recruit specialized security talent. These experts don't just install firewalls - they architect entire security ecosystems, train medical staff on emerging threats, and develop protocols that anticipate tomorrow's attack vectors. In modern healthcare, cybersecurity specialists are as vital as surgeons in protecting patient wellbeing.
Their expertise spans risk assessment, emergency response planning, and continuous system monitoring. Perhaps most importantly, they serve as translators between technical security requirements and practical healthcare delivery - ensuring protection measures never interfere with life-saving care.
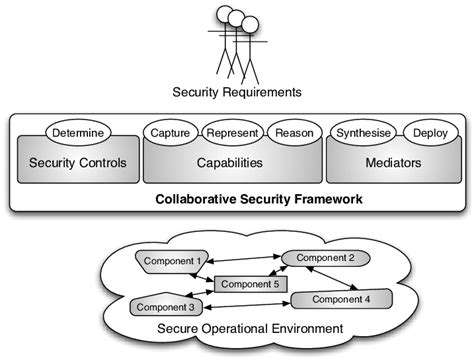
Addressing the Security Challenges through Collaborative Efforts
Tackling medical IoT security requires unprecedented cooperation across industries. Device manufacturers, healthcare providers, policymakers, and security experts must break down silos to share threat intelligence and best practices. The old model of isolated security efforts simply can't keep pace with today's interconnected threats.
This collaboration must produce standardized security frameworks, shared monitoring systems, and coordinated response protocols. Only through such unified efforts can the healthcare industry stay ahead of cybercriminals while maintaining the life-saving potential of connected medical technology.
Mitigating the Risks Through Robust Security Measures
Implementing Multi-Factor Authentication
Multi-factor authentication (MFA) has evolved from optional extra to absolute necessity in medical device security. Modern implementations combine biometric verification with hardware tokens and one-time passwords, creating multiple defense layers against credential theft. In healthcare environments, MFA doesn't just protect data - it safeguards lives.
The most effective systems dynamically adjust authentication requirements based on risk levels, applying stricter verification for sensitive functions while maintaining usability for routine operations. This balanced approach ensures security without compromising emergency access when seconds count.
Data Encryption and Secure Transmission Protocols
State-of-the-art encryption like AES-256 has become the minimum standard for protecting medical data in transit and at rest. However, true security extends beyond algorithms to encompass entire transmission ecosystems. Quantum-resistant cryptography now supplements traditional methods, preparing healthcare systems for future threats.
Regular Software Updates and Patch Management
The most sophisticated security measures crumble without timely updates. Automated patch management systems have become critical infrastructure, silently deploying updates during low-usage periods while maintaining continuous device functionality. In healthcare IT, an outdated system isn't just inefficient - it's potentially lethal.
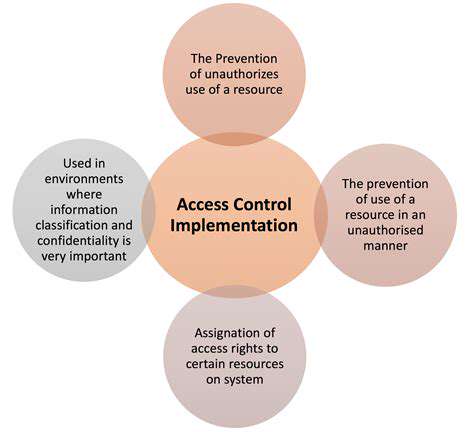
Secure Device Configuration and Access Control
Zero-trust architecture has revolutionized medical device security, treating every access attempt as potentially hostile until verified. Role-based access controls now incorporate contextual factors like location and time of day, while just-in-time privileges grant temporary access for specific procedures.
Regular Security Audits and Penetration Testing
Modern security assessments employ ethical hackers who think like criminals to expose vulnerabilities. These red team exercises now incorporate AI-driven attack simulations that continuously probe defenses, identifying weaknesses before real attackers can exploit them.
Incident Response Planning and Training
Contemporary response plans integrate real-time threat intelligence feeds with automated containment protocols. Staff training has evolved beyond annual seminars to include immersive simulations that test responses to increasingly sophisticated attack scenarios. In healthcare cybersecurity, preparation isn't a one-time event but an ongoing cycle of improvement.