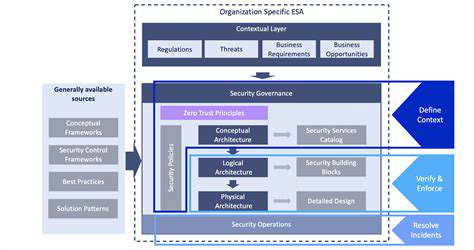
The Rise of Sophisticated Cyberattacks
The modern threat landscape is characterized by an alarming escalation in the sophistication and frequency of cyberattacks. These attacks are no longer simple phishing scams; instead, they utilize advanced techniques like spear-phishing, exploiting vulnerabilities in software, and employing elaborate social engineering tactics to gain unauthorized access to sensitive data. Understanding these sophisticated methods is crucial for organizations to effectively mitigate risks. Cybercriminals are constantly adapting their strategies, making it imperative for organizations to remain vigilant and proactively defend against emerging threats.
The increasing complexity of cyberattacks demands a proactive and multi-layered security approach. This necessitates a robust security infrastructure, rigorous security awareness training for employees, and the implementation of advanced threat detection and response mechanisms. Failure to adapt to these evolving threats can have devastating consequences for individuals and organizations alike.
The Growing Importance of Data Protection
In today's interconnected world, data is a valuable asset, and its protection is paramount. The increasing reliance on digital platforms and cloud services has amplified the risk of data breaches, making organizations more vulnerable to cyberattacks. Protecting sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction is a critical component of a robust security strategy.
Data breaches can have significant financial and reputational consequences for organizations, leading to hefty fines, loss of customer trust, and disruption of business operations. Implementing robust data protection measures is not just a best practice, it's a necessity for organizations operating in today's digital landscape.
The Impact of Remote Work on Security
The shift to remote work models has presented new and significant security challenges. With employees working from various locations and using diverse devices, the attack surface for cybercriminals has expanded considerably. Securing remote access points, protecting sensitive data transmitted over less secure networks, and enforcing strong authentication protocols are crucial in this new environment.
Ensuring secure remote access and maintaining robust data protection is essential to prevent data breaches and maintain business continuity in the face of cyberattacks. Organizations need to adapt their security measures to accommodate the increased risks associated with remote work and provide employees with the necessary tools and training to stay secure.
The Role of Artificial Intelligence in Threat Detection
Artificial intelligence (AI) is rapidly transforming the cybersecurity landscape. AI-powered tools can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, enabling proactive threat detection and response. These tools can automate tasks, identify suspicious behavior in real-time, and enhance the overall efficiency of security operations. AI is becoming an indispensable tool in the fight against escalating cyber threats.
The Need for Enhanced Security Awareness Training
Robust security awareness training programs are essential for all employees to mitigate the risks associated with social engineering attacks. Employees are often the weakest link in an organization's security posture, and attackers frequently exploit this weakness through phishing emails, malicious websites, and other social engineering tactics. Regular training programs that focus on identifying and avoiding these threats can significantly improve the overall security posture of an organization.
Equipping employees with the knowledge and skills to recognize and report suspicious activity is crucial. It is vital to foster a culture of security awareness, empowering employees to become active participants in defending against cyber threats.
Financial Implications: Beyond the Ransom Payment
Financial Losses Beyond the Ransom
Beyond the immediate cost of the ransom payment, organizations face a cascade of Financial repercussions. These include the expenses associated with forensic investigations to determine the extent of the breach, data recovery efforts, and the potential for regulatory fines or lawsuits. The loss of productivity due to system downtime, disruption of business operations, and the need for employee training to prevent future attacks all contribute to significant financial strain. The damage often extends beyond the immediate incident, affecting future revenue projections and potentially impacting the organization's reputation and market standing.
The long-term financial implications of a ransomware attack can be devastating, stretching well beyond the initial ransom demand. Consider the costs of implementing enhanced security measures to prevent future attacks, the expense of hiring cybersecurity specialists to bolster defenses, and the potential for reputational damage that could lead to lost contracts and diminished customer confidence.
Operational Disruption and Recovery Costs
Ransomware attacks typically result in significant operational disruption. Systems are often rendered unusable, halting production, delaying deliveries, and impacting customer service. The time required to restore systems and data can be extensive, requiring significant resources and impacting the organization's ability to function normally. This period of downtime can also lead to lost revenue and decreased efficiency, pushing the organization into a cycle of recovery and rebuilding.
The recovery process itself is costly. Data restoration, system rebuilding, and the implementation of new security protocols all require financial investment. The need to replace lost data, train employees on new security protocols, and potentially rebuild critical infrastructure adds to the overall financial burden of the attack.
Damage to Reputation and Customer Trust
A ransomware attack can severely damage an organization's reputation and erode customer trust. The breach often results in negative publicity, impacting the organization's brand image and potentially leading to customer churn. The fear of future attacks and the perception of vulnerability can create a lasting negative impression, making it difficult for the organization to regain the trust of its customers and stakeholders. Public disclosure of the attack, depending on its severity and nature, can have a profound and negative impact on the company's image and public perception.
Legal and Regulatory Penalties
Organizations targeted by ransomware attacks can face significant legal and regulatory penalties. Depending on the industry and the nature of the data breach, regulatory bodies may impose substantial fines. Furthermore, victims may face lawsuits from affected customers or partners, seeking compensation for damages incurred. Navigating the legal landscape after a ransomware attack requires expert legal counsel to mitigate potential liabilities and ensure compliance with relevant regulations.
Indirect Financial Impacts and Lost Opportunities
The financial implications of a ransomware attack extend beyond the direct costs. The disruption caused by the attack can lead to lost business opportunities, decreased market share, and difficulty attracting and retaining talent. The loss of confidence in the organization's security practices can deter potential investors and partners, impacting future growth prospects. These indirect financial impacts can be just as detrimental as the direct costs, highlighting the far-reaching consequences of a ransomware incident.
The Role of Cybercrime in Global Instability
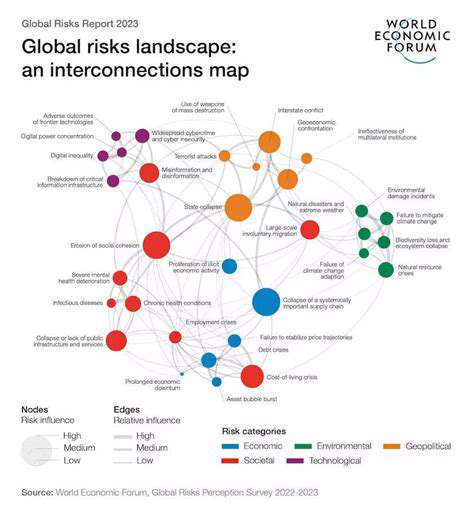
Cybercrime's Impact on Global Infrastructure
Cybercrime is no longer a niche issue confined to individual users; it poses a significant threat to global infrastructure, impacting critical systems and services that underpin modern life. The disruption caused by sophisticated cyberattacks can cripple essential services like power grids, transportation networks, and financial institutions, leading to widespread economic and social instability. This global interconnectedness makes infrastructure more vulnerable to coordinated attacks, as a breach in one part can quickly cascade to others.
The consequences of these attacks extend far beyond immediate disruption. Long-term damage to trust in systems and institutions can have lasting ramifications, requiring substantial investments in security measures and potentially altering the very fabric of how we interact with technology.
The Economic Toll of Cybercrime
The financial consequences of cybercrime are substantial and far-reaching, affecting individuals, businesses, and governments alike. Cyberattacks can result in significant financial losses, including direct costs for damage recovery, reputational damage, and loss of productivity. Furthermore, the cost of implementing security measures to prevent future attacks adds another layer to the financial burden.
The damage isn't limited to the direct costs. Stolen intellectual property, compromised sensitive data, and fraudulent activities can cause long-term financial harm to organizations, impacting their competitiveness and market share. Indirect costs, such as legal fees and regulatory penalties, often further amplify the economic impact.
The Social and Political Ramifications
Beyond the economic sphere, cybercrime has profound social and political implications. The theft and misuse of personal data can erode trust in online platforms and services, leading to increased anxieties about privacy and security. This can negatively impact social cohesion and political stability, as individuals become more wary of digital interactions and institutions. The anonymity afforded by the internet can also be exploited to spread misinformation and propaganda, exacerbating social divisions and influencing political outcomes.
The potential for manipulation and exploitation through cyber means raises serious questions about the future of democratic processes and the role of technology in society. Robust security measures and ethical guidelines are crucial to mitigate these risks and ensure that the digital realm contributes positively to a more just and equitable world.
The Need for International Cooperation
Addressing the global challenge of cybercrime requires a concerted effort from international organizations, governments, and private sector entities. Effective cooperation is essential to share information, coordinate responses to attacks, and develop harmonized standards for cybersecurity. This includes sharing threat intelligence, developing best practices for security protocols, and fostering collaboration in law enforcement to prosecute cybercriminals.
International cooperation is essential to address the complexities of cybercrime, which often transcends national borders. Building trust and promoting shared responsibility are critical for developing effective strategies that prevent future attacks and hold perpetrators accountable.
The Need for a Collaborative Response: International Cooperation and Prevention

Collaborative Responses in Modern Work Environments
In today's rapidly evolving business landscape, the ability to foster effective collaboration is paramount. Teams that can readily share ideas, insights, and feedback are far more likely to achieve ambitious goals and overcome complex challenges. This collaborative approach transcends individual expertise, leveraging the collective intelligence of the group to produce innovative solutions and drive organizational success. Collaboration is not just a desirable trait; it's a fundamental requirement for success in modern work environments.
A collaborative response fosters a culture of trust and openness. When individuals feel comfortable sharing their perspectives, even differing viewpoints, the potential for creative problem-solving explodes. This environment allows for a more comprehensive understanding of the issues at hand, leading to well-rounded and well-considered decisions. The key benefit lies in the diversity of thought that collaborative responses encourage.
Strategies for Enhancing Collaborative Responses
Implementing effective strategies for fostering collaborative responses is crucial. One key strategy involves establishing clear communication channels and protocols. This includes defining roles, responsibilities, and expectations for each team member, ensuring everyone understands their contribution to the overall goal. Regular meetings, both formal and informal, are essential for maintaining open dialogue and encouraging ongoing feedback. Furthermore, utilizing collaborative tools and platforms can streamline communication and project management, making it easier for team members to stay connected and informed.
Another crucial element is fostering a supportive and inclusive work environment. This necessitates encouraging active listening, valuing different perspectives, and providing constructive feedback mechanisms. Creating a psychologically safe space where everyone feels comfortable expressing their ideas, even if they are unconventional, is critical for generating truly innovative and effective responses. This environment must prioritize mutual respect and understanding to encourage the free exchange of ideas.
The Impact of Collaborative Responses on Organizational Performance
Collaborative responses have a significant impact on overall organizational performance. By promoting a culture of shared responsibility and collective problem-solving, organizations can achieve greater efficiency and productivity. Teams that work collaboratively are better equipped to handle unexpected challenges and adapt to evolving market conditions. This adaptability is essential for long-term success in a dynamic and unpredictable business environment.
Furthermore, collaborative responses contribute to increased employee engagement and satisfaction. When employees feel valued and heard, their motivation and commitment to the organization increase. This, in turn, leads to greater innovation, creativity, and ultimately, improved profitability. A strong sense of belonging and shared purpose fostered through collaborative responses ultimately benefits both the individual and the organization.