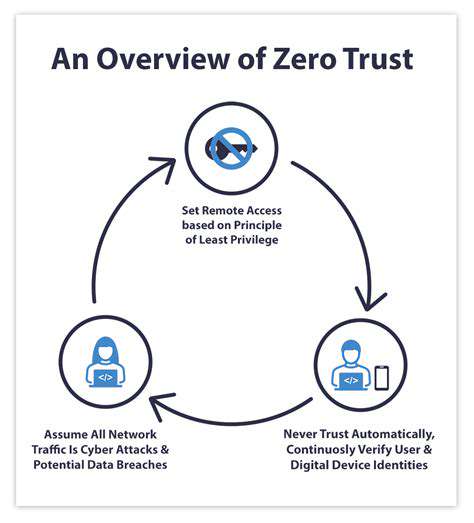
The Evolving Landscape of Technology and Cyber Threats
AI and Machine Learning's Growing Influence

Across industries worldwide, Artificial Intelligence and Machine Learning technologies are transforming traditional business operations and problem-solving approaches. What was once considered science fiction has become our everyday reality, with AI applications now touching every aspect of modern commerce from customer interactions to production line optimization. These systems excel at processing enormous datasets to uncover insights that would elude even the most skilled human analysts.
Organizations are witnessing substantial gains in operational efficiency as a result. By automating routine processes, intelligent systems enable human teams to concentrate on higher-value strategic work. This redistribution of labor leads to more effective resource utilization and measurable productivity improvements.
The explosion of digital data acts as a primary catalyst for this transformation. Modern enterprises collect unprecedented amounts of information - from consumer behavior metrics to real-time equipment diagnostics. While this data presents tremendous analytical potential, its true value remains locked without proper interpretation. AI and ML technologies provide the key to unlocking these insights at scale.
Practical applications demonstrate remarkable versatility. Whether enhancing online shopping recommendations or predicting factory maintenance needs, the possibilities continue to expand. Innovative companies constantly discover fresh applications that elevate customer satisfaction while streamlining internal operations. This cycle of discovery drives rapid technological progress across all sectors.
Concerns about workforce displacement deserve thoughtful consideration. However, predictions of widespread job losses often overlook emerging opportunities. While automation may change certain roles, it simultaneously creates demand for new positions focused on AI system management and optimization. These roles require specialized knowledge that blends technical expertise with domain-specific understanding.
Continuous learning initiatives become essential in this environment. Workers must cultivate complementary skills to collaborate effectively with intelligent systems and maximize their potential benefits.
Ethical implications represent perhaps the most critical consideration. As these technologies grow more sophisticated, we must proactively address potential algorithmic biases and ensure responsible implementation. Transparency and accountability form the foundation for building public trust in these powerful tools. The ethical dimensions of AI development demand sustained attention, preventive safeguards, and inclusive discussions to guarantee these innovations serve society's best interests.
Comprehensive regulatory frameworks provide necessary guidance. Thoughtful policy measures help mitigate potential harms while promoting beneficial applications across all industries.
The Expanding Ransomware-as-a-Service Ecosystem

Understanding Ransomware-as-a-Service
Ransomware-as-a-Service has emerged as a pervasive danger affecting organizations regardless of size or industry. This criminal business model provides ransomware platforms to less technically skilled operators through affiliate programs. Participants can launch sophisticated attacks without developing the underlying technology, focusing instead on target selection and ransom collection. This accessibility has caused an exponential increase in ransomware incidents.
The financial incentives prove compelling for RaaS providers, who typically receive percentage-based commissions from successful attacks. Comprehensive support services for affiliates, including operational guidance and technical assistance, further increase attack effectiveness. This collaborative criminal enterprise has significantly raised both the frequency and impact of ransomware campaigns.
Operational Mechanics Behind RaaS
The RaaS framework operates through a service-oriented structure, with core malware components delivered as turnkey solutions. Affiliates handle target identification, attack execution, and payment collection while leveraging the provider's technical infrastructure. This division of labor enables rapid adaptation to defensive measures and varying target environments.
Modern RaaS platforms often include sophisticated toolkits featuring reconnaissance utilities, attack vectors, and even negotiation support services. These comprehensive offerings dramatically lower the technical barriers for cybercriminals, resulting in attacks against previously unaffected sectors.
Consequences of RaaS Proliferation
The ramifications for victim organizations extend far beyond immediate financial demands. Direct costs from ransom payments represent just one component, with operational paralysis and data recovery expenses often proving more damaging. The reputational harm following an attack can undermine customer confidence and erode market position for years. Preparedness for such scenarios has become a business imperative.
RaaS platforms' constant evolution presents increasingly complex defensive challenges. Regular updates to attack methods and evasion techniques necessitate equally dynamic security postures. Comprehensive vulnerability management programs form the foundation of effective protection.
Developing Effective Countermeasures
Combating RaaS threats requires coordinated defensive strategies. Robust endpoint protection, network segmentation, and continuous security awareness training represent essential components. Organizations must also develop specialized incident response plans addressing ransomware-specific scenarios. Foundational security practices including rigorous access controls, timely patch management, and multi-factor authentication significantly reduce attack surfaces.
Collaboration across sectors enhances collective defense capabilities. Information sharing regarding emerging threats, attack patterns, and defensive innovations helps organizations stay ahead of evolving RaaS tactics. This cooperative approach remains vital in addressing the persistent ransomware challenge.