Understanding Spear Phishing Tactics
Spear phishing is a sophisticated form of phishing attack that goes beyond the generic, mass-mailed approach. Instead of sending out indiscriminate emails to a large pool of recipients, spear phishing targets specific individuals or organizations. This targeted approach makes it more effective because the attackers tailor their messages to exploit the recipient's specific knowledge, position within the organization, or personal relationships. This personalized touch increases the likelihood of the victim falling for the scam, as it creates a sense of urgency or legitimacy that a generic phishing email lacks. Criminals often research their victims extensively to create realistic and convincing messages, which can make it difficult for victims to recognize the attack.
The attackers' meticulous research often involves gathering information about the victim's professional roles, responsibilities, and relationships within the organization. This information allows them to craft highly personalized emails that mimic legitimate communications, such as invoices, requests for information, or even urgent messages from a superior. This level of personalization can make it challenging for recipients to distinguish between a genuine communication and a malicious attempt to steal sensitive data or gain unauthorized access.
Identifying Spear Phishing Attempts
Recognizing spear phishing attempts requires a keen eye for detail and a heightened awareness of potential threats. Look for emails that appear unusually urgent or demanding, contain suspicious links or attachments, or request sensitive information like login credentials or financial details. Pay close attention to the sender's email address, which may be slightly altered to mimic a legitimate source. Also, be wary of emails containing unusual grammar or spelling errors, as these can be indicators of a fraudulent attempt. These subtle clues, combined with a general sense of caution, can help individuals and organizations avoid falling victim to spear phishing attacks.
A critical aspect of identifying spear phishing attempts is the ability to recognize the context of the message. Consider whether the request aligns with normal procedures or if it seems unusual or out of place. If a message asks for something unexpected or sensitive, it's crucial to verify its legitimacy through independent channels, such as contacting the purported sender directly via a known and trusted method (not through the email in question). This crucial step can prevent significant data breaches or financial losses.
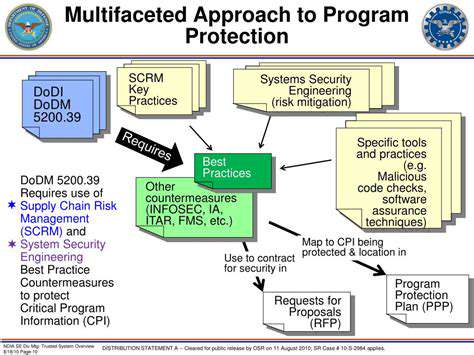
Protecting Against Spear Phishing Attacks
Implementing robust security measures is paramount in protecting against spear phishing attacks. This includes educating employees about the risks of phishing and spear phishing, emphasizing the importance of verifying the legitimacy of all emails, especially those containing sensitive information or unusual requests. Implementing multi-factor authentication (MFA) on all accounts can add an extra layer of security, making it significantly harder for attackers to gain access even if they obtain login credentials. Regular security awareness training can help to reinforce the importance of these measures and equip employees with the knowledge and skills necessary to identify and report suspicious emails.
Organizations should also implement strong email filtering systems to block potentially malicious emails before they reach employees' inboxes. Encouraging employees to report suspicious emails to IT security teams is vital, enabling the quick identification and mitigation of threats. By combining robust security protocols, comprehensive employee training, and a culture of vigilance, organizations can significantly reduce their vulnerability to spear phishing attacks and safeguard their valuable data and resources.