Effective communication is paramount in any work environment, but remote work presents unique challenges. Misunderstandings can easily arise from the lack of nonverbal cues, leading to frustration and misinterpretations. Clearer communication protocols and tools are crucial for remote teams to thrive. This often necessitates more explicit instructions and frequent check-ins to ensure everyone is on the same page.
Different time zones can also complicate communication, making it difficult to schedule meetings and respond to urgent requests in a timely manner. Implementing flexible scheduling or utilizing tools that accommodate different time zones can mitigate this issue.
Maintaining Work-Life Balance
The blurred lines between work and personal life can be a significant hurdle for remote workers. Successfully separating these two spheres is essential for maintaining well-being and preventing burnout. Remote work requires conscious effort to establish boundaries and prioritize personal time. Setting clear work hours and designating a dedicated workspace can help create a more structured environment.
Establishing healthy routines and engaging in activities outside of work can also contribute to maintaining a balanced lifestyle.
Isolation and Collaboration
Working remotely can sometimes lead to feelings of isolation, especially for individuals who thrive on in-person interaction. Creating a sense of community and fostering collaboration is crucial for remote teams to function effectively. Regular virtual team-building activities and social interactions can help combat feelings of isolation. Utilizing collaborative tools and platforms can further enhance interaction and information sharing.
Remote work can also create challenges for team bonding and building strong professional relationships. Teams need to proactively organize virtual events and activities to nurture these connections.
Technical Glitches and Infrastructure Issues
Reliable internet connectivity and access to necessary technology are fundamental for remote work success. Technical difficulties can disrupt workflow and create significant frustration for remote workers. Investing in robust internet infrastructure and ensuring access to reliable technology solutions can help alleviate these issues. Having backup plans and troubleshooting procedures in place is also essential.
Ensuring adequate equipment and software for all team members is also critical. Technical support must be readily available to address any issues that may arise.
Productivity and Time Management
Remote work necessitates strong self-discipline and time management skills. Maintaining focus and productivity in a home environment can be challenging. Establishing a dedicated workspace, setting clear goals, and prioritizing tasks can help improve productivity. Time management techniques, such as the Pomodoro method, can assist in staying organized and focused.
Regular breaks and mindful downtime are vital for preventing burnout and maintaining concentration. A good work environment at home can also encourage productivity, and there should be tools and resources to help support this.
Security and Data Privacy Concerns
Protecting sensitive company data and maintaining secure communication channels are critical in a remote work environment. Cybersecurity risks are heightened when employees work from various locations and use personal devices. Implementing strong security protocols and providing adequate training on data protection best practices is essential. Using encrypted communication channels and secure cloud storage solutions can further mitigate these risks.
Strong passwords and multi-factor authentication should be enforced. Regular security audits and risk assessments are also important.
Overcoming the Cultural Differences
Remote work often brings together individuals from diverse cultural backgrounds. Understanding and appreciating these differences is essential for building strong and effective teams. Training programs that promote cultural awareness and sensitivity can help to mitigate misunderstandings and foster mutual respect. Acknowledging and respecting different communication styles and work ethics is crucial for success.
Language barriers and cultural nuances can sometimes affect communication and collaboration. Utilizing translation tools and providing cultural sensitivity training can help to bridge these gaps.
Ensuring Data Integrity Through Redundancy and Validation

Data Validation Techniques
Data validation is a crucial step in ensuring data integrity. It involves verifying that the data entered into a system conforms to predefined rules and constraints. This process helps to identify and correct errors early in the data entry process, preventing inconsistencies and inaccuracies from propagating throughout the system. Thorough data validation minimizes the risk of flawed analyses and misleading conclusions. By adhering to strict validation rules, organizations can maintain the accuracy and reliability of their data.
Different validation techniques are employed depending on the type of data. These include checking for valid formats, ensuring data ranges are within acceptable limits, and verifying that data conforms to specified business rules. Implementing robust validation routines is essential to prevent data entry mistakes that can compromise the integrity of the entire database.
Data Backup and Recovery Strategies
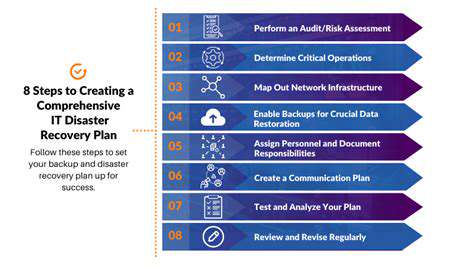
Regular data backups are essential for maintaining data integrity. A comprehensive backup strategy safeguards against data loss due to various factors, including hardware failures, software errors, or malicious attacks. Implementing a robust backup and recovery plan is critical to ensuring business continuity and minimizing downtime. A well-defined disaster recovery plan should include multiple backup locations and automated recovery procedures.
The frequency of backups should be determined based on the sensitivity and criticality of the data being backed up. For instance, critical operational data may require daily backups, while less critical data might be backed up weekly or monthly. Effective data backup and recovery procedures are paramount to protecting against catastrophic data loss.
Data Security Measures
Protecting data from unauthorized access and modification is paramount to maintaining its integrity. Robust security measures, such as access controls, encryption, and firewalls, are essential to prevent data breaches and ensure that only authorized personnel can access sensitive information. Implementing these measures safeguards the confidentiality, integrity, and availability of the data.
Regular security audits and vulnerability assessments are necessary to identify and address potential security risks. These processes help to ensure that the security measures are effective and up-to-date. Regular updates and patches to security software and systems are crucial in mitigating potential threats. Security awareness training for employees is also a vital component of a comprehensive data security strategy.
Data Auditing Procedures
Regular data audits are essential for ensuring ongoing integrity. Audits help to identify inconsistencies, errors, and anomalies in the data. This process helps to pinpoint potential issues and take corrective action before they escalate to significant problems. Maintaining a detailed audit trail is critical to tracing data changes and understanding the origin of any discrepancies. This process helps to ensure accountability and compliance with relevant regulations.
Audits should be conducted at regular intervals to ensure that data integrity is maintained throughout the system. The scope and frequency of audits should be tailored to the specific data being audited and the potential risks associated with that data. By implementing regular auditing procedures, organizations can maintain the accuracy and reliability of their data over time.
Data Quality Management Systems
Implementing a formal data quality management system is essential for establishing and maintaining data integrity. This system should define clear data quality standards, establish procedures for data validation and correction, and provide mechanisms for monitoring data quality. These standards ensure consistency and accuracy in data collection and usage. A robust data quality management system promotes data consistency and reliability, leading to more effective data-driven decision-making.
Data quality management systems should also include provisions for regular data quality assessments and reporting. These assessments help to identify trends and patterns in data quality issues and suggest improvements to the data collection and management processes. Data quality initiatives are vital for long-term data integrity and business success.