Ensuring Secure Communication Channels for IoT Devices
Securing the Communication Protocols
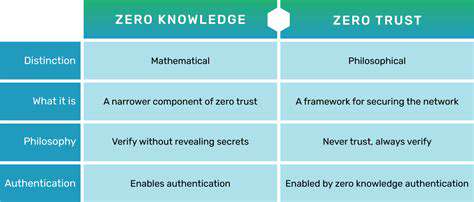
Robust communication protocols form the foundation of secure IoT device interactions. Encryption, particularly Transport Layer Security (TLS), must be implemented across all communication channels without exception. This critical measure guarantees that sensitive data moving between devices and central servers remains confidential and shielded from unauthorized interception. When choosing between protocols like MQTT, CoAP, or AMQP, organizations must carefully evaluate each option's security implications based on their specific device requirements and data characteristics. The selection process should involve thorough analysis of each protocol's advantages and limitations to maintain both security and operational efficiency.
Authentication and Authorization Mechanisms
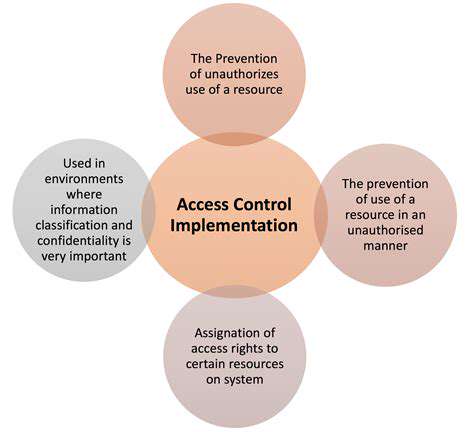
Strong authentication and authorization systems serve as essential barriers against unauthorized access to IoT networks. Multi-factor authentication, digital certificates, and unique device keys represent some of the most effective methods for verifying identities. Well-designed access control lists (ACLs) play a crucial role in defining and limiting user and device permissions. Security teams must establish regular review cycles for these mechanisms to ensure they remain effective against emerging threats and evolving attack vectors.
Data Integrity and Validation
Protecting the accuracy and consistency of data in transit represents a fundamental requirement for IoT systems. Advanced techniques like SHA-256 message digests provide reliable verification of data authenticity and prevent unauthorized modifications. Implementing comprehensive validation rules at multiple system levels helps filter out potentially harmful or corrupted data inputs. This multi-layered validation approach significantly reduces the risk of security breaches caused by malformed or malicious data packets.
Device Hardening and Patch Management
Individual IoT devices require rigorous security measures comparable to network protections. System hardening involves removing unnecessary services, implementing secure boot processes, and enforcing strict password policies. Timely firmware updates and vulnerability patches represent non-negotiable components of ongoing device security maintenance. These practices collectively reduce potential attack surfaces and help maintain consistent protection against constantly evolving cyber threats.
Network Segmentation and Isolation
Strategic network division provides an effective containment strategy for potential security breaches. By creating isolated network zones, organizations can limit the spread of any potential compromise while maintaining critical operations. This segmentation approach allows for customized security controls tailored to each network segment's specific requirements and risk profile. Properly implemented network segmentation significantly enhances overall system resilience and security posture.
Security Monitoring and Logging
Comprehensive activity monitoring and detailed logging form essential components of modern IoT security strategies. Intrusion detection systems (IDS) and prevention systems (IPS) provide critical real-time threat detection capabilities. Systematic log analysis enables security teams to identify patterns, detect anomalies, and respond quickly to potential incidents. Regular security audits and trend analysis help organizations stay ahead of emerging threats and adapt their defenses accordingly.
Managing and Updating IoT Devices Securely

Device Inventory Management
Maintaining a comprehensive inventory of IoT devices serves as the cornerstone of effective device management. Detailed records should include hardware specifications, software versions, physical locations, and data flow characteristics. Accurate device classification and tracking enables more efficient maintenance scheduling and update prioritization. This systematic approach ensures correct software deployments while minimizing system disruptions.
Software Updates and Patches
Consistent software maintenance remains critical for both functionality and security. Developing reliable update mechanisms requires extensive testing to ensure seamless deployment across diverse device fleets. Delayed updates create exploitable vulnerabilities that threaten entire IoT ecosystems. Prioritizing timely patch management protects sensitive data and maintains system integrity against increasingly sophisticated cyber threats.
Remote Device Access and Control
Efficient remote management capabilities prove invaluable for large-scale IoT deployments. These systems enable rapid troubleshooting, configuration adjustments, and software maintenance without physical access. Secure remote access protocols must balance convenience with robust authentication mechanisms. Implementing strict access controls prevents unauthorized modifications while maintaining operational flexibility.
Device Security Configuration
Customized security configurations must address each device's unique risk profile. This includes enforcing complex credentials, regular credential rotation, and strong encryption standards. Periodic security audits and vulnerability scans provide critical insights into potential weaknesses. Proactive identification and mitigation of security gaps helps maintain continuous protection against evolving threats.
Data Backup and Recovery
Comprehensive data protection strategies must account for potential device failures or data corruption. Reliable backup systems form the foundation of business continuity planning for IoT deployments. Regular testing of recovery procedures ensures operational resilience and minimizes potential downtime during critical situations.
Maintenance and Troubleshooting
Systematic maintenance protocols extend device lifespans and optimize performance. Well-documented troubleshooting procedures enable rapid incident response and minimize service interruptions. Standardized documentation ensures consistent practices across maintenance teams and facilitates effective knowledge transfer.