Relying solely on perimeter security often leaves significant vulnerabilities unaddressed. This situation is particularly alarming for government organizations where safeguarding sensitive information and systems is of utmost importance. A more proactive and holistic security approach is necessary to effectively counter these sophisticated threats and protect critical assets.
The Importance of Zero Trust Architecture
Zero Trust architecture represents a paradigm shift in security philosophy, operating on the fundamental principle that no user, device, or application should receive automatic trust. This model requires continuous authentication and authorization for every access request, irrespective of origin or credentials. By rigorously verifying each access attempt, Zero Trust dramatically reduces potential attack vectors and minimizes the impact of potential security breaches.
Implementing Zero Trust in Government
Deploying Zero Trust in government environments necessitates a comprehensive strategy tailored to the unique requirements and challenges of public sector organizations. This includes establishing robust identity and access management (IAM) systems, implementing network micro-segmentation to restrict lateral movement, and deploying advanced threat detection and response capabilities. Continuous monitoring and adaptation to emerging threats form the cornerstone of successful implementation.
Furthermore, fostering collaboration between various government agencies and cybersecurity professionals is vital for sharing threat intelligence and operational best practices. This cooperative approach ensures Zero Trust principles become deeply embedded across all government operations, creating a more secure and resilient digital infrastructure.
Addressing the Challenges of Zero Trust Adoption
While Zero Trust offers compelling security advantages, its implementation presents several challenges. These include substantial investments in new technologies and infrastructure, the complexity of managing granular security controls, and potential disruptions to existing operational workflows. Comprehensive training programs for personnel on new security protocols represent another critical consideration.
Overcoming these obstacles requires a phased implementation approach, robust change management strategies, and commitment to continuous improvement. With careful planning and execution, the long-term security benefits of Zero Trust can significantly outweigh initial implementation challenges, ultimately creating more secure government operating environments.
Zero Trust Principles: A Foundation for Enhanced Security
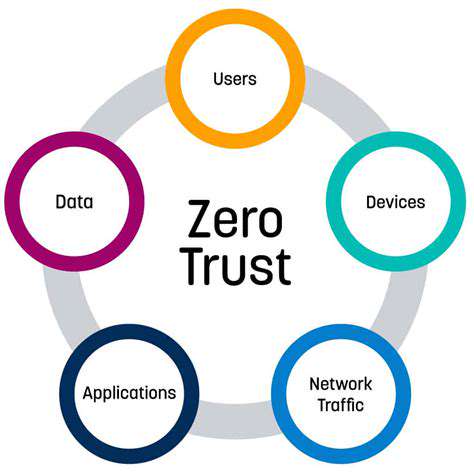
Zero Trust Architecture: Core Principles
Zero Trust architecture fundamentally redefines security paradigms by eliminating implicit trust assumptions, regardless of an entity's network location. This approach mandates continuous verification and validation of all access attempts by users, devices, and applications. This systematic verification process inherently reduces potential attack surfaces by enforcing stringent authentication and authorization protocols for every access request. It represents a decisive departure from traditional network security models that rely primarily on perimeter defenses.
The principle of least privilege forms the foundation of Zero Trust implementation. This security philosophy ensures users and devices receive only the minimum access privileges required to perform their designated functions. This containment strategy significantly limits potential damage from security breaches by restricting attacker access to sensitive systems and data.
Identifying and Verifying Users and Devices
User and device verification represents a critical component of Zero Trust implementation. This process incorporates multi-factor authentication (MFA) and other advanced verification techniques to ensure only authorized entities gain access to protected resources. Comprehensive verification protocols are essential for maintaining data integrity and confidentiality within Zero Trust environments. This includes deploying sophisticated identity management systems capable of accurately authenticating all users and devices.
Micro-segmentation and Access Control
Network micro-segmentation serves as a fundamental element of Zero Trust security. This approach divides networks into isolated segments, effectively containing the impact of potential security breaches. Access to resources within these segments is strictly controlled through detailed security policies. This granular access control mechanism substantially reduces the potential damage from compromised systems or credentials within network environments. The segmentation strategy effectively contains threats and isolates potential damage within specific network zones.
Continuous Monitoring and Response
Zero Trust implementation requires ongoing commitment rather than one-time deployment. Continuous monitoring of network activities and user behaviors is essential. Security teams employ advanced SIEM (Security Information and Event Management) tools to detect anomalies and potential security threats. This perpetual monitoring ensures security postures remain robust and adaptable to evolving cyber threats. The proactive monitoring approach enables rapid response to emerging security issues and prevents potential threats from escalating.
Data Loss Prevention (DLP) and Data Security
Data loss prevention systems constitute an integral component of Zero Trust security frameworks. DLP mechanisms help prevent unauthorized access, misuse, disclosure, alteration, or destruction of sensitive information. Implementing comprehensive DLP solutions is critical for ensuring data confidentiality and integrity within Zero Trust architectures. This includes encrypting sensitive data during transmission and storage while implementing strict data access controls to prevent unauthorized exposure.
Overcoming Challenges and Maximizing Benefits

Identifying and Defining Challenges
Successful problem resolution begins with precise identification and clear definition of existing obstacles. This initial phase requires meticulous analysis to properly understand the specific issues at hand. Inaccurate problem identification frequently leads to ineffective solutions and resource misallocation. Thorough examination ensures challenges are not only recognized but also understood within their complete operational context, including their potential impacts and interrelationships.
Developing a Comprehensive Strategy
Following challenge identification, developing a well-structured strategy becomes essential for effective resolution. This process involves evaluating various approaches, exploring potential solutions, and assessing their practical feasibility. A holistic strategy addresses immediate concerns while anticipating future complications and promoting sustainable development. This forward-looking approach minimizes the likelihood of encountering similar challenges in subsequent operations.
Resource Allocation and Prioritization
Effective resource distribution is critical for successful implementation. This involves evaluating available resources—both human and material—and prioritizing tasks based on their potential impact and urgency. Strategic prioritization ensures focused efforts on the most critical areas, optimizing return on investment. Well-planned resource allocation enables efficient utilization of time and other valuable assets.
Implementing Actionable Solutions
Strategic planning achieves little without concrete implementation. Converting identified challenges into specific, measurable, achievable, relevant, and time-bound (SMART) objectives is essential. This ensures all actions align with overarching goals. Solution implementation requires detailed planning and precise execution, with careful consideration of all operational aspects.
Monitoring Progress and Evaluating Results
Continuous assessment forms the foundation of successful initiatives. Regular progress evaluations enable necessary strategy adjustments and verify solution effectiveness. Tracking key performance indicators and analyzing outcomes identifies potential improvement areas and refines operational approaches. This iterative process ensures optimal resource utilization and maintains strategy alignment with evolving conditions.
Adapting to Shifting Circumstances
The operational environment remains constantly dynamic and evolving. Successful initiatives require inherent adaptability. The capacity to modify strategies and solutions in response to changing conditions or emerging opportunities proves vital. Operational flexibility and adaptability represent essential components of long-term success across all domains. This responsive capability ensures strategies remain effective and relevant despite environmental changes.
Future Trends in Government Zero Trust Security

Government Zero Trust: Enhanced Security Measures
The continuously evolving threat landscape demands robust cybersecurity approaches, with zero trust architecture emerging as a leading solution. Government entities are progressively adopting zero trust principles to safeguard sensitive information and critical infrastructure. This transition to zero trust substantially reduces potential attack vectors by verifying every access attempt before authorization. This proactive security philosophy prioritizes comprehensive protection over traditional perimeter-based defenses, establishing zero trust as a fundamental component of modern government security strategies.
Implementing zero trust principles requires fundamental changes in security philosophy, replacing implicit trust assumptions with continuous verification protocols. Government agencies must thoroughly evaluate every access request, regardless of origin or user credentials. This rigorous scrutiny significantly reduces risks of unauthorized access and potential data breaches.
Improved Data Visibility and Control
Future government zero trust initiatives will emphasize enhanced data visibility and control mechanisms. This includes deploying advanced analytical tools to identify suspicious activities and potential threats in real-time, providing complete visibility into data movements and access patterns. Comprehensive tracking and monitoring of data flows across networks will prove essential for effective breach prevention and response.
Enhanced data visibility enables governments to proactively identify and address system vulnerabilities, thereby strengthening overall security postures. This proactive approach facilitates rapid responses to emerging threats, minimizing potential damages and ensuring operational continuity.
Enhanced User Authentication and Authorization
Zero trust mandates rigorous user authentication and authorization protocols. Advanced authentication mechanisms, including multi-factor authentication (MFA), become essential for verifying user identities and preventing unauthorized access. Implementing these measures ensures only properly authorized individuals can access sensitive government resources.
Beyond basic authentication, zero trust requires detailed authorization policies. This involves specifying precise access rights for each user and device, limiting access to strictly necessary resources. This approach minimizes opportunities for malicious actors to exploit compromised credentials or devices.
Centralized Security Management Platforms
Integrated security management platforms will play pivotal roles in supporting government zero trust initiatives. These platforms consolidate security tools and data from multiple sources, providing unified security oversight. This centralized approach simplifies threat detection and response processes, enabling security teams to react more efficiently to emerging threats.
Integration with Cloud Technologies
Growing cloud adoption within government sectors makes zero trust principles essential for securing these environments. Zero trust implementations must seamlessly integrate with cloud services, ensuring all access requests undergo proper verification and authorization. This involves establishing secure connections and enforcing strict access controls within cloud infrastructures. This integration proves critical for ensuring data security and regulatory compliance in cloud-based government systems.
Advanced Threat Detection and Response
Modern zero trust strategies will increasingly rely on sophisticated threat detection and response capabilities. Implementing cutting-edge security tools and techniques, including machine learning and AI-powered threat detection systems, becomes imperative. These technologies can identify and neutralize sophisticated attacks in real time, protecting sensitive government data and infrastructure. Proactive threat detection and rapid response capabilities will prove essential for mitigating cyberattack impacts.
Improved Collaboration and Information Sharing
Successful zero trust implementation across government requires enhanced interagency collaboration and information sharing. Exchanging threat intelligence and operational best practices helps identify and address emerging vulnerabilities more effectively. Strengthened collaboration and information sharing significantly improve overall security postures across government ecosystems. This cooperative approach facilitates knowledge exchange and strengthens collective government security.











