Introduction to AI-Powered Cloud Security

Key Benefits of AI-Powered Cloud Solutions
The landscape of cloud computing has been transformed by artificial intelligence, creating new possibilities across multiple sectors. Modern enterprises are adopting these intelligent systems to streamline operations, process massive datasets efficiently, and extract meaningful patterns that drive strategic choices. This technological synergy results in measurable financial benefits and enhanced operational performance for organizations across the spectrum. The flexible nature of cloud-based AI systems enables seamless adjustment to fluctuating business requirements.
When AI capabilities merge with cloud infrastructure, the combination unlocks unprecedented potential. Cloud environments supply the computational power needed for sophisticated AI operations, while machine learning algorithms extract valuable knowledge from stored information. Forward-thinking companies are gaining market advantages by utilizing these integrated solutions to spot industry shifts, predict consumer behavior, and customize offerings.
Data protection remains a cornerstone of these advanced systems. Major cloud service providers implement comprehensive security protocols, safeguarding sensitive information used in AI model development. This allows businesses to concentrate on innovation rather than potential vulnerabilities in their digital ecosystem.
Implementing AI-Powered Cloud Solutions
Deploying intelligent cloud systems demands methodical preparation and evaluation of multiple considerations. Organizations must audit existing technical resources, define precise AI objectives, and choose suitable cloud services and analytical tools. This thoughtful approach guarantees system harmony and optimizes the value of the technological investment.
Assembling the right team proves essential for successful deployment. Companies should either hire or develop professionals skilled in both distributed computing and artificial intelligence methodologies. Having competent personnel is fundamental to sustaining the solution's effectiveness and extracting maximum benefit from the AI implementation.
Proper information handling forms the foundation for productive AI utilization. The integrity and availability of data significantly influence analytical model precision. Organizations must rigorously verify that their training datasets are thoroughly processed, systematically arranged, and readily available to machine learning processes. This groundwork ensures trustworthy outcomes from AI-powered analyses.
Real-time Security Monitoring and Alerting
Real-time Threat Detection
Contemporary security monitoring platforms have become indispensable for early threat identification and rapid response. These solutions continuously examine digital communications, access records, and user interactions for irregularities. Persistent surveillance enables cybersecurity teams to intercept and neutralize risks before they develop into serious breaches. Immediate threat recognition dramatically lessens the consequences and possible harm from digital intrusions.
Network Intrusion Detection
Specialized network monitoring tools serve as critical components in modern security architectures. These systems scrutinize data transmissions for malicious behavior including unauthorized entries, service disruptions, and virus distribution. Optimal performance demands precise setup and continuous refinement to counter new vulnerabilities. Alert mechanisms notify security staff about potential compromises, facilitating quick assessment and containment.
Advanced network protection mechanisms can recognize complex attack strategies through behavioral analysis that surpasses basic signature recognition.
Endpoint Security Monitoring
Device-level security surveillance provides critical protection for all connected equipment within corporate networks. Continuous observation of workstations, portable computers, and mobile devices detects harmful programs, illegitimate access efforts, and questionable data operations. Current-generation endpoint protection solutions with frequent updates are vital for risk reduction and prompt threat resolution.
Vulnerability Management
Modern security frameworks incorporate automated weakness identification mechanisms. These solutions detect security gaps in applications, equipment, and system settings throughout the digital infrastructure. Early detection of system vulnerabilities is essential for blocking potential exploits by cybercriminals. Timely updates and security patches prevent attackers from capitalizing on these weaknesses.
Automated scanning technologies and systematic patching protocols form the backbone of comprehensive vulnerability control systems.
Security Information and Event Management (SIEM)
Integrated security platforms aggregate and analyze security alerts from multiple organizational sources. These systems offer unified interfaces for examining security incidents, detecting correlations, and connecting related threats. Consolidated security intelligence proves invaluable for rapid incident handling and proactive threat investigation. The ability to link disparate security events helps uncover coordinated attack campaigns.
User and Entity Behavior Analytics (UEBA)
Behavioral analysis tools monitor activity patterns to identify deviations from normal operations. This capability helps expose internal threats, compromised accounts, and other anomalous behaviors. Tracking irregular activities enables security teams to detect potential breaches and gather critical security intelligence. Sophisticated analytical techniques reveal hidden patterns that may indicate harmful intentions.
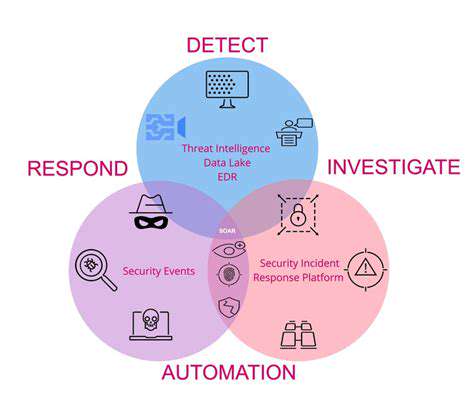
Security Orchestration, Automation, and Response (SOAR)
Integrated security automation platforms standardize incident response procedures, enhancing overall cyber resilience. These solutions connect with multiple security applications to automate alert responses, decreasing reaction times and boosting operational efficiency. Automating routine security operations allows specialists to dedicate attention to complex challenges and strategic priorities. Accelerated incident resolution capabilities minimize potential operational impacts from security events.











