The Zero Trust Paradigm Shift for Application Development
Defining Zero Trust in Application Development
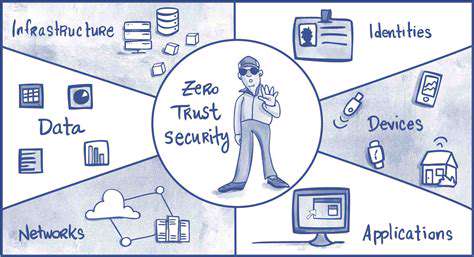
The zero trust model fundamentally alters conventional security approaches. Rather than operating on assumptions of internal network safety, it mandates verification for all access attempts regardless of origin. Every user interaction, device connection, and application request requires explicit validation before permissions are granted. This meticulous methodology transforms development practices, replacing blanket trust with continuous identity confirmation through robust IAM frameworks. Application architects must now design systems where trust is never implied but always earned through verification.
This security revolution impacts the entire development timeline. Protection mechanisms can't be tacked on as an afterthought - they must be integral to the application's DNA. Engineering teams must adopt security-by-design thinking, implementing principle-based safeguards like granular privilege assignments, network micro-partitioning, and layered authentication protocols. The transition demands more than technical changes; it requires abandoning the outdated trust but verify mentality in favor of never trust, always verify discipline.
Building Zero Trust-Ready Applications
Crafting applications for zero trust environments demands meticulous architectural planning. Development teams must master fine-grained permission systems and implement them uniformly across all application components. This involves employing secure development methodologies, conducting periodic security posture reviews, and establishing comprehensive activity tracking systems. Central to this process are sophisticated IAM platforms that govern user entitlements with surgical precision.
Strategic deployment of API management layers and encrypted communication standards proves equally critical. These components enforce validation rules for all API transactions, whether internal or external. Containerization solutions like Docker paired with orchestration tools such as Kubernetes enable creation of security-isolated runtime environments. Such compartmentalization contains potential breach impacts effectively. Perhaps most importantly, teams must institutionalize ongoing threat monitoring and preemptive vulnerability remediation processes.
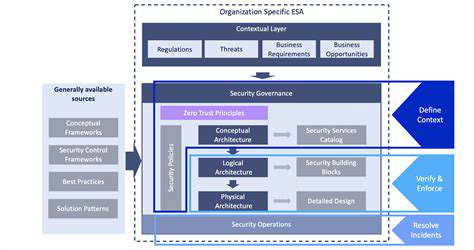
The complete integration of security considerations throughout the SDLC represents the ultimate objective. Protective measures must permeate every development stage - from initial blueprints and code implementation through quality assurance and production deployment. When security becomes an organic component rather than supplemental feature, applications naturally evolve to satisfy zero trust requirements.
Building Zero Trust into the Application Development Lifecycle (DevSecOps)
Building a Secure Foundation
Establishing comprehensive security in modern applications begins with Zero Trust adoption. This philosophy rejects outdated perimeter-based security models that assume internal safety. Instead, it operates on continuous verification principles for all access attempts to application resources. The transition demands holistic security integration across all architectural layers, not just network boundaries.
Zero Trust implementation requires microscopic attention to permission structures, with customized policies for every user role and device type. This encompasses multi-layered verification systems ensuring only properly credentialed entities gain resource access. Such precise permission management forms the bedrock of application security in zero trust environments.
Enhancing User and Device Authentication
At the heart of Zero Trust lies uncompromising authentication standards. Multi-factor authentication (MFA) becomes non-negotiable, demanding multiple proof points beyond simple passwords. Verification methods might include mobile device confirmations, hardware tokens, or biological markers. This defense-in-depth strategy dramatically reduces compromise risks even when primary credentials are exposed.
Biometric authentication systems raise security standards significantly by tying access to immutable physical characteristics. Facial recognition, fingerprint scanning, and behavioral biometrics create formidable barriers against impersonation attempts, overcoming weaknesses inherent in traditional credential-based systems.
Securing Data and Communication Channels
Data protection takes center stage in Zero Trust architectures. Comprehensive encryption - for stored information, active transmissions, and endpoint data - is mandatory for safeguarding sensitive assets. Industry-standard protocols like TLS 1.3 must secure all communication pathways between users and application services.
Secure channel establishment goes beyond encryption to include rigorous participant verification and pathway integrity checks. This involves protocol hardening, firewall optimization, and continuous connection validation to prevent unauthorized data access. Regular penetration testing and security posture assessments ensure the Zero Trust framework maintains effectiveness against evolving threats.