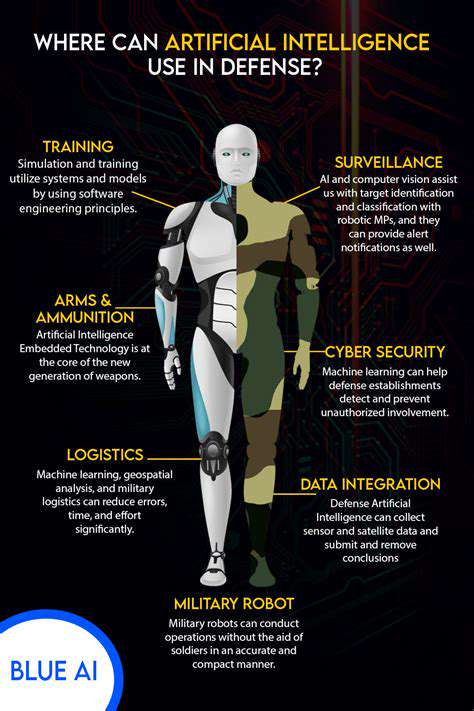
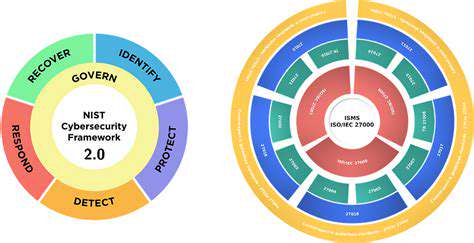
Leveraging AI for Enhanced Threat Detection
Artificial intelligence (AI) is rapidly transforming the landscape of cybersecurity, and its application in threat hunting is poised to revolutionize how organizations identify and respond to emerging threats. AI algorithms can analyze massive datasets of security logs, network traffic, and user activity with unprecedented speed and accuracy, identifying patterns and anomalies that might be missed by traditional security tools. This capability empowers security teams to proactively hunt for threats, rather than just reacting to incidents after they occur.
By automating the initial stages of threat hunting, AI frees up human analysts to focus on more complex investigations and strategic decision-making. This shift allows for a more proactive and targeted approach to security, reducing the overall response time to threats and minimizing potential damage.
AI-Powered Threat Pattern Recognition
AI algorithms excel at identifying intricate and subtle patterns within vast datasets, distinguishing malicious behavior from legitimate activities. This advanced pattern recognition capability is crucial in threat hunting, enabling security teams to detect even the most sophisticated and evasive threats that traditional methods might overlook. AI can learn and adapt to evolving threat landscapes, recognizing new attack vectors and techniques as they emerge.
Furthermore, AI can analyze contextual information to identify potential indicators of compromise (IOCs) with higher confidence. This contextual awareness allows AI to discern between legitimate activities and suspicious patterns within the context of the entire system, leading to a more accurate and efficient threat hunting process.
Automated Threat Hunting Processes
AI can automate several crucial steps in the threat hunting process, freeing up valuable human resources for more complex tasks. This automation extends to tasks such as data collection, analysis, and reporting, significantly accelerating the identification and prioritization of potential threats. AI can analyze data from various sources, including logs, network traffic, and user activity, to identify potential anomalies and prioritize them based on their risk level.
Collaboration Between Humans and AI
The future of threat hunting lies in a collaborative approach where AI augments human expertise rather than replacing it. AI can provide valuable insights, identify potential threats, and prioritize them for human review. Human analysts can leverage AI-generated insights to conduct more in-depth investigations, validate findings, and make informed decisions. This symbiotic relationship between human intelligence and AI capabilities is vital to achieving optimal security outcomes.
Improving Incident Response Time
AI's ability to rapidly identify and prioritize threats translates directly into faster incident response times. By automating the initial stages of threat hunting, AI ensures that potential threats are detected and analyzed much more quickly. This proactive approach minimizes the window of opportunity for attackers, significantly reducing the potential for damage and disruption to business operations.
Building a Robust Threat Intelligence Ecosystem
AI can play a vital role in building a comprehensive threat intelligence ecosystem by analyzing large volumes of data from various sources to identify emerging threats and vulnerabilities. By continuously learning and adapting to new attack patterns, AI can provide valuable insights into evolving threat landscapes, enabling security teams to stay ahead of attackers and strengthen their defenses. This data analysis capability also allows for the development of predictive models that can anticipate potential threats before they manifest.
Addressing the Challenges of AI in Threat Hunting
While AI offers significant advantages in threat hunting, it's crucial to acknowledge the associated challenges. Ensuring data quality and accuracy is paramount, as inaccurate or incomplete data can lead to flawed analysis and potentially misidentified threats. Furthermore, the interpretability of AI models needs to be carefully considered to understand why a particular threat is flagged and to ensure that human analysts can effectively validate the findings. Addressing these challenges is essential to building a robust and trustworthy AI-powered threat hunting system.