Real-Time Threat Response and Adaptive Security
Real-Time Threat Detection
AI-powered endpoint protection systems, such as Nex, operate with remarkable efficiency in identifying threats as they emerge. Unlike conventional tools that rely on outdated signatures, these solutions scrutinize endpoint activities—whether on computers or mobile devices—to pinpoint unusual behaviors that could signal an attack. This forward-thinking methodology proves indispensable in our current cybersecurity climate, where threats evolve at breakneck speed.
By processing immense volumes of data, from network flows to file modifications, these systems detect irregularities that might escape traditional defenses. This persistent vigilance enables the swift discovery of malware, phishing schemes, and other cyber dangers in real time, dramatically lowering the chances of data leaks or system infiltrations.
Adaptive Security Measures
Nex doesn’t just detect threats—it evolves with them. The platform refines its understanding of cyber risks continuously, enhancing its capacity to neutralize novel attack methods. This adaptability is critical as hackers constantly refine their tactics to bypass security protocols.
Leveraging both past incidents and live threat data, Nex dynamically adjusts its defensive strategies. Consequently, security effectiveness improves alongside emerging threats, ensuring robust protection against even the most recent cyber onslaughts.
Automated Response Capabilities
Among its standout features, Nex’s automated reactions to threats set it apart. The system can independently isolate infected files, halt harmful traffic, and commence recovery procedures to reinstate affected systems. Such automation drastically cuts down the manual effort typically demanded in security operations.
The immediacy of these automated defenses often spells the difference between contained incidents and catastrophic breaches. By swiftly neutralizing threats and initiating repairs, Nex mitigates damage, shielding organizations from prolonged vulnerabilities and data loss.
Proactive Threat Intelligence Integration
Nex taps into an extensive threat intelligence network, receiving constant updates about new vulnerabilities and attack methodologies. This integration ensures the system remains a step ahead, armed with the latest insights on hacker strategies and compromised systems. A proactive stance on threat intelligence is non-negotiable for sustaining formidable defenses.
Improved Security Posture and Reduced Risk
Deploying Nex translates to a fortified security framework and diminished exposure to cyber risks. The synergy of real-time threat detection, adaptive countermeasures, and automated responses creates a safer ecosystem for sensitive information and critical operations.
Nex’s ability to learn and adjust fosters a resilient security environment, adept at neutralizing risks and curtailing the fallout from potential breaches. This dynamic protection is invaluable in an era where cyber threats grow increasingly sophisticated.
Enhanced User Experience and Reduced Operational Overhead
Nex prioritizes user convenience alongside security. Its automation reduces the need for constant human oversight, allowing security teams to focus on strategic initiatives rather than routine monitoring. This efficiency boost streamlines workflows and lightens the load on personnel.
The system’s user-friendly design and autonomous functions ensure minimal disruption to daily operations, facilitating smooth integration into existing processes. Such emphasis on usability is pivotal for sustained adoption across organizations.
Advanced Threat Hunting and Prevention Capabilities
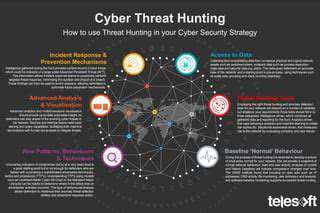
Advanced Threat Hunting Techniques
Advanced threat hunting transcends passive monitoring by actively scouring networks for concealed malicious activities. This aggressive stance is vital for uncovering advanced persistent threats (APTs) that evade conventional defenses. Hunters employ diverse intelligence sources—threat feeds, vulnerability databases—to direct their probes.
Critical methods include dissecting system logs, user actions, network patterns, and file changes. Linking seemingly unrelated events reveals hidden attack indicators. Such investigations demand specialized tools and seasoned analysts capable of sifting through colossal datasets to spot faint traces of compromise.
Preventive Measures to Combat Threats
Prevention remains the cornerstone of defense against sophisticated attacks. Strong access controls, multi-factor authentication, and routine security assessments form the bedrock of protection. Penetration tests and vulnerability scans expose weaknesses before exploitation occurs.
Ongoing surveillance of network traffic and system logs—augmented by proactive hunting—is paramount for preempting attacks. These practices empower teams to identify and neutralize threats before they escalate.
Utilizing Security Information and Event Management (SIEM)
SIEM systems aggregate and analyze security events across an organization’s digital infrastructure. This centralized approach spots anomalies and malicious patterns that might otherwise go unnoticed. SIEM solutions are indispensable for both threat hunting and coordinated incident response.
Threat Intelligence Integration
Incorporating threat intelligence into security operations fuels more effective hunting and prevention. Real-time feeds about emerging threats, hacker tactics, and compromised systems enable teams to preemptively bolster defenses and focus investigations where they matter most.
Incident Response and Containment
A polished incident response blueprint is essential for managing breaches efficiently. The plan should detail procedures for detection, isolation, eradication, recovery, and post-incident analysis. Without such preparedness, organizations risk prolonged disruptions and irreversible damage.
Advanced Security Tools and Technologies
Cutting-edge tools—intrusion detection systems, next-gen firewalls, EDR platforms—are non-negotiable for countering modern threats. These technologies form the vanguard against evolving attack vectors, preserving organizational resilience. Selection should align with specific operational needs and risk profiles.