Double extortion, a more sophisticated approach than traditional ransomware attacks, involves not only encrypting a victim's data but also threatening to publicly leak it if the ransom isn't paid. This dual threat significantly increases the pressure on victims, as the potential reputational damage and financial losses from data breaches can be devastating, often exceeding the initial cost of the ransom itself. This approach leverages the growing awareness and heightened sensitivity surrounding data privacy regulations and breaches, making victims more vulnerable to these escalating demands.
This tactic targets organizations across various sectors, from healthcare and finance to education and government, highlighting the widespread vulnerability of critical infrastructure and sensitive information to these attacks. The growing sophistication of these attacks underscores the need for proactive security measures and a heightened awareness of the risks.
The Impact on Victims
The impact of double extortion goes beyond the financial burden of the ransom. Victims face significant reputational damage, potential regulatory fines, and the loss of customer trust. The leak of sensitive data can expose confidential information, leading to legal ramifications and further financial losses. This multifaceted impact makes double extortion a particularly challenging and costly threat for organizations to contend with.
The psychological stress on victims, coupled with the mounting pressure to pay, can lead to hasty decisions that compromise security further. The fear of data exposure often outweighs the rational cost-benefit analysis, making it imperative for organizations to have robust incident response plans in place.
Data Leak Threats: A Growing Concern
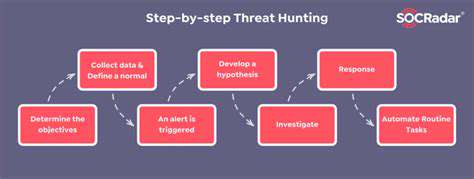
Data leak threats are an increasingly prominent part of the ransomware landscape. The availability of dark web marketplaces and online forums dedicated to leaked data allows attackers to monetize their exploits and further incentivize these attacks. This creates a potent combination that can severely impact organizations' reputation and operations.
The growing ease of access to and the use of data leak tools has enabled ransomware groups to target a wider range of organizations, with no organization feeling truly immune. This makes proactive security measures and data protection strategies more critical than ever.
The Evolution of Ransomware Groups
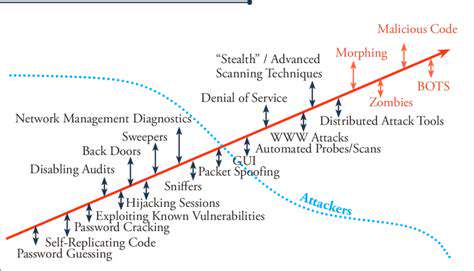
Ransomware groups are continuously evolving, adapting their tactics and techniques to exploit vulnerabilities in security measures. The rise of double extortion demonstrates their willingness to push the boundaries of what is considered acceptable in these attacks. This evolution demands a proactive and dynamic approach to security and incident response.
Responding to the Threat
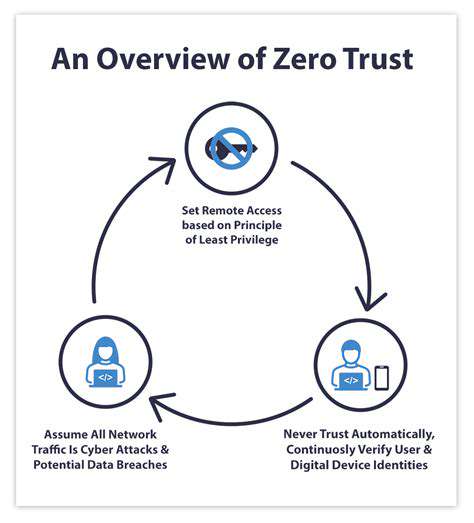
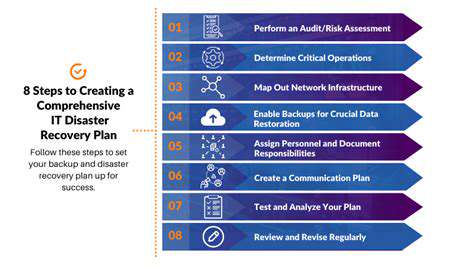
Organizations need comprehensive security strategies that go beyond traditional antivirus and firewall protection. This includes robust data backup and recovery plans, secure data handling protocols, and employee training programs to mitigate the risk of human error. Regular security audits and penetration testing are crucial to identify and address vulnerabilities before they are exploited.
Furthermore, fostering a culture of security awareness and educating employees about phishing attempts, suspicious emails, and other social engineering tactics is essential to prevent successful attacks. Collaboration between security teams, legal departments, and leadership is vital in creating a coordinated response to these evolving threats.
Prevention and Mitigation Strategies
Proactive prevention measures are critical to minimizing the impact of ransomware attacks. This includes implementing strong access controls, regularly updating software and systems, and employing robust encryption protocols. Staying informed about the latest threats and vulnerabilities is essential for mitigating risk.
Investing in security information and event management (SIEM) systems can help detect and respond to suspicious activities in real-time. Furthermore, regularly reviewing and updating incident response plans is crucial to ensure a swift and effective response when an attack occurs. By proactively addressing these concerns, organizations can significantly reduce their vulnerability to double extortion and data leak threats.