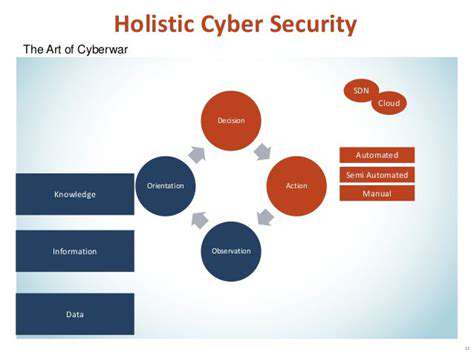
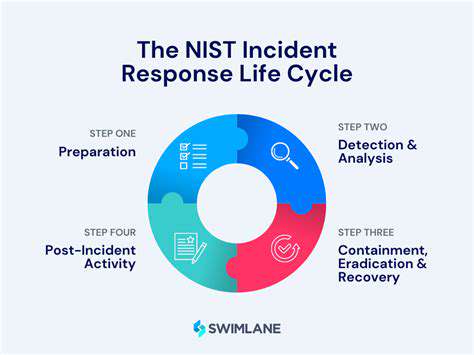
Implementing and Maintaining the Scoring System

Implementing a Robust System
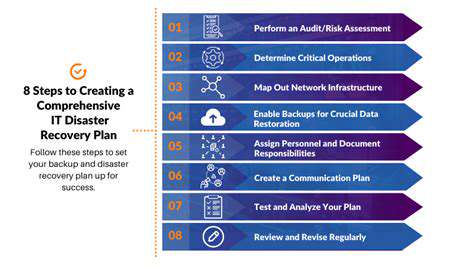
Implementing a robust system requires careful planning and execution. This involves defining clear objectives, identifying key stakeholders, and developing a detailed project plan. Thorough documentation is crucial for future maintenance and scalability. A well-defined scope ensures that the system meets the needs of the users and aligns with overall business goals.
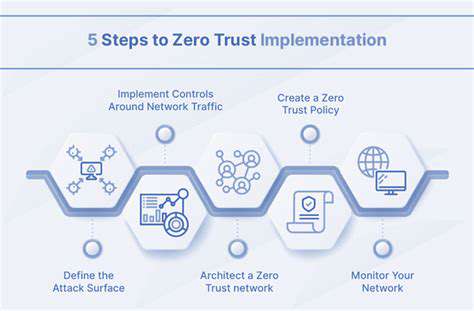
Careful consideration of security measures is essential. Implementing robust security protocols from the outset will prevent potential vulnerabilities and protect sensitive data. This encompasses a variety of measures, from access controls to encryption, to ensure the system's integrity and confidentiality.
Maintaining System Performance
System maintenance is not a one-time event; it's an ongoing process that requires proactive monitoring and responsive adjustments. Regular performance testing ensures the system continues to function optimally as user demands and data volumes increase.
Regular updates, patches, and upgrades are crucial to address security vulnerabilities and enhance functionality. Keeping the system current minimizes the risk of downtime and ensures continued compliance with industry standards.
Data Integrity and Backup Strategies
Maintaining data integrity is paramount for the reliability and trustworthiness of the system. Implementing robust data validation procedures and error handling mechanisms prevents data corruption and ensures accuracy.
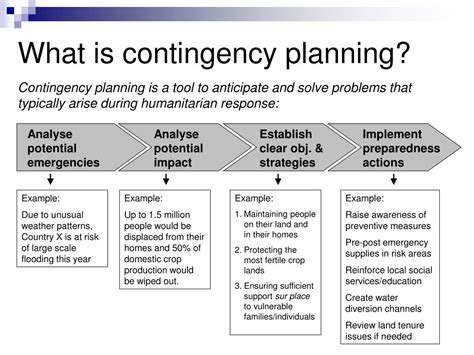
Comprehensive backup and recovery strategies are essential to protect against data loss due to hardware failures, software errors, or malicious attacks. This includes regular backups to offsite locations and testing the recovery process to ensure data restoration is swift and complete.
User Training and Support
Providing comprehensive user training is essential to ensure the system is effectively utilized. Training materials should be clear, concise, and accessible to all user levels.
Establishing a dedicated support team or readily available online resources will address user questions and resolve technical issues promptly. Effective support ensures that users can confidently utilize the system and maximize its benefits.
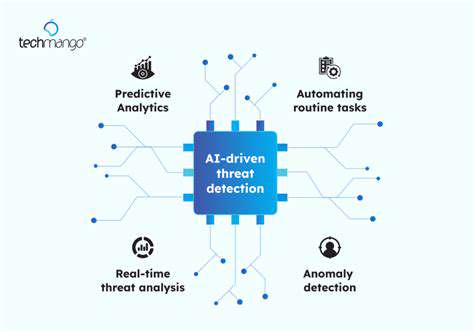
Security Considerations
Security is a crucial aspect of any system, especially in today's digital landscape. Implementing robust access controls and user authentication mechanisms is critical for safeguarding sensitive data and preventing unauthorized access.
Regular security audits and penetration testing help identify potential vulnerabilities and weaknesses in the system's security posture. Proactive identification and remediation of security flaws help maintain the system's integrity.
Scalability and Future Growth
Considering the future growth of the system is vital for long-term success. Designing the system with scalability in mind allows it to adapt to increasing user demands and data volumes without significant performance degradation.
Modular design and flexible architecture enable future enhancements and modifications to the system. Investing in a scalable solution now avoids costly and time-consuming rework later.
System Monitoring and Alerting
Continuous monitoring of the system's performance and health is critical for proactive identification and resolution of potential issues. Monitoring tools should provide real-time visibility into key metrics.
Implementing an alerting system that notifies administrators of critical events and potential problems is vital for minimizing downtime and ensuring the smooth operation of the system. This proactive approach to monitoring greatly enhances the efficiency of system maintenance and reduces the impact of unforeseen issues.