Developing a Comprehensive Security Incident Response Plan
Developing a Robust Security Strategy
A comprehensive security strategy is crucial for protecting sensitive data and systems from various threats. It's not just about installing firewalls; it's a multifaceted approach encompassing policies, procedures, and technologies. A well-defined strategy ensures consistent security measures across the organization, reducing vulnerabilities and improving overall resilience. This proactive approach is essential for mitigating risks and safeguarding against potential breaches.
A robust security strategy should be regularly reviewed and updated to address emerging threats and evolving technologies. This continuous improvement ensures that the strategy remains relevant and effective in safeguarding the organization's valuable assets.
Identifying Potential Threats
Identifying potential threats is a critical first step in developing a comprehensive security strategy. This involves recognizing both internal and external vulnerabilities, including malicious actors, accidental errors, and natural disasters. Thorough risk assessment is key to prioritizing efforts and allocating resources effectively.
Analyzing historical data on security incidents, conducting vulnerability assessments, and staying updated on emerging threats are all important components of this crucial process.
Implementing Security Policies and Procedures
Implementing clear security policies and procedures is paramount for maintaining a secure environment. These policies should outline acceptable use of technology, data handling procedures, and incident response protocols. Establishing clear guidelines ensures consistent behavior across the organization, fostering a security-conscious culture.
Regular training and awareness programs for employees are essential to ensure that everyone understands and adheres to the security policies and procedures. This includes training on identifying phishing attempts, protecting sensitive information, and reporting security incidents promptly.
Utilizing Security Technologies
Implementing appropriate security technologies is a critical component of a comprehensive security strategy. This includes firewalls, intrusion detection systems, encryption tools, and multi-factor authentication. These technologies provide a layered defense against various threats, enhancing the overall security posture.
Choosing the right technologies requires careful consideration of the organization's specific needs and budget constraints. A thorough cost-benefit analysis can help determine the most effective and efficient solutions.
Monitoring and Auditing Security Measures
Continuous monitoring and auditing of security measures are essential to ensure their effectiveness. Real-time monitoring of network activity, security logs, and user behavior can help identify potential threats and vulnerabilities early. Regular audits provide an objective assessment of the security controls in place, highlighting any gaps or weaknesses.
Regularly reviewing security logs and reports, conducting penetration testing, and implementing security information and event management (SIEM) systems are vital in achieving this crucial aspect of a strong security strategy.
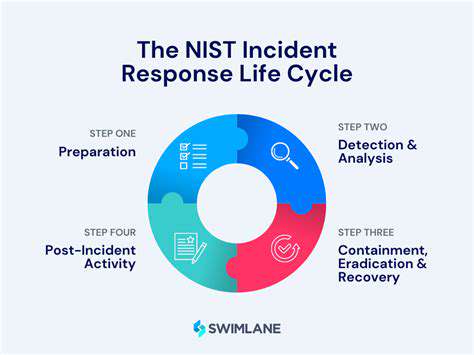
Incident Response Planning
A well-defined incident response plan is crucial for managing and mitigating security breaches. This plan should outline the steps to take in the event of a security incident, including containment, eradication, recovery, and post-incident analysis. Planning for potential incidents, including ransomware attacks and data breaches, is critical to minimizing the impact and ensuring business continuity.
Employee Security Awareness Training
Employee security awareness training is a cornerstone of a strong security posture. Regular training programs should focus on recognizing and avoiding common security threats, such as phishing attempts and social engineering tactics. Empowering employees with the knowledge and skills to identify and report potential security risks is vital in preventing breaches. This proactive approach strengthens the overall security defense of the organization.
Promoting Collaboration and Information Sharing
Fostering a Culture of Collaboration
A crucial element in building a robust supply chain cyber resilience strategy is fostering a culture of collaboration and information sharing among all stakeholders. This involves more than just exchanging data; it necessitates a shift in mindset, emphasizing transparency and mutual trust. Organizations need to actively encourage communication channels between internal teams, suppliers, and even competitors, enabling the rapid dissemination of crucial threat intelligence. This collaborative approach not only accelerates the identification of potential vulnerabilities but also allows for the development of proactive mitigation strategies, strengthening the overall security posture of the entire supply chain.
Effective communication protocols should be established, outlining clear procedures for reporting suspicious activities and sharing threat intelligence. Regular meetings and workshops can facilitate knowledge exchange and promote a sense of shared responsibility. By creating a supportive environment where information is freely shared, organizations can collectively address potential threats and minimize the impact of cyberattacks.
Implementing Secure Communication Protocols
Implementing secure communication protocols is paramount for protecting sensitive information flowing throughout the supply chain. This involves the use of encryption technologies to safeguard data transmitted between different parties. Robust authentication measures, including multi-factor authentication, are essential to verify the identity of individuals and systems involved in the exchange of information. Employing secure messaging platforms and dedicated channels for sensitive data exchange can significantly reduce the risk of unauthorized access and data breaches.
Regular security assessments of communication channels are vital to identify and address any vulnerabilities. This proactive approach not only ensures the integrity of data but also enhances the overall security posture of the supply chain. By implementing these measures, organizations can minimize the risk of cyberattacks and ensure the confidentiality, integrity, and availability of critical data.
Establishing Shared Threat Intelligence Platforms
Establishing a centralized platform for collecting, analyzing, and disseminating threat intelligence is critical for enhancing supply chain cyber resilience. This platform should facilitate the rapid sharing of information about emerging threats, vulnerabilities, and attack vectors among all stakeholders. The platform should allow for real-time updates and provide actionable insights that enable organizations to adapt their security measures accordingly.
This shared intelligence platform should be accessible to all authorized parties in the supply chain, including suppliers, manufacturers, distributors, and retailers. The platform should also include tools for threat analysis and risk assessment, enabling organizations to proactively identify and mitigate potential vulnerabilities within their specific segments of the supply chain. This collaborative approach to threat intelligence significantly strengthens the overall security posture of the entire network.