Leveraging AI for Enhanced Threat Detection Capabilities
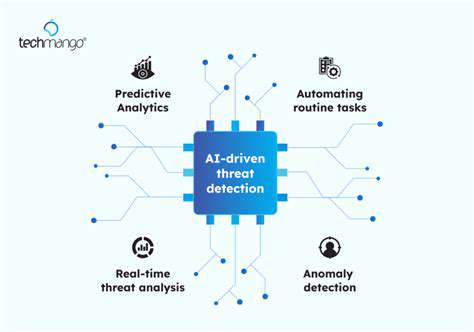
AI-Powered Threat Detection
Modern cybersecurity strategies increasingly rely on artificial intelligence to stay ahead of emerging threats. Unlike traditional methods, AI-driven systems process enormous volumes of network traffic, system logs, and user behavior data to uncover subtle signs of compromise. These advanced algorithms detect anomalies that human analysts might overlook, providing a critical advantage in today's complex digital environment. The ability to intercept threats before they escalate represents a fundamental shift in how we approach digital defense.
What sets these systems apart is their capacity for continuous learning. As attackers develop new techniques, AI models adapt in real-time, refining their detection capabilities to match evolving attack patterns. This dynamic responsiveness proves essential when dealing with sophisticated cybercriminal tactics that change by the hour.
Predictive Threat Modeling
Beyond reacting to active threats, AI enables organizations to anticipate potential security incidents. By examining historical attack data and identifying emerging patterns, these systems forecast likely vulnerabilities before exploitation occurs. Security teams can then implement targeted countermeasures, creating a preventative security framework rather than a reactive one.
This forward-looking approach transforms resource allocation, enabling organizations to concentrate their defenses where they're needed most. Instead of spreading security investments thinly, companies achieve better protection through strategic, intelligence-driven decisions.
Automated Response Mechanisms
When threats emerge, speed determines the difference between containment and catastrophe. AI-powered response systems act within milliseconds—isolating compromised endpoints, terminating malicious processes, and initiating forensic protocols. This automation eliminates human latency during critical security events, ensuring consistent and immediate reactions to potential breaches.
Strengthening Organizational Defenses
The integration of AI into security operations creates a more resilient digital infrastructure. By handling routine monitoring and initial threat response, these systems allow cybersecurity professionals to focus on strategic initiatives and complex investigations. This division of labor not only improves security outcomes but also creates a more sustainable operational model for overburdened security teams.
As AI handles the increasing volume of security alerts, organizations experience fewer false positives and more accurate threat identification. This precision reduces alert fatigue among analysts while ensuring genuine threats receive appropriate attention.
Optimizing Incident Management
Post-breach investigations benefit tremendously from AI's analytical capabilities. These systems rapidly correlate disparate data points, reconstruct attack timelines, and identify root causes with remarkable accuracy. The resulting insights accelerate recovery efforts while providing actionable intelligence to prevent similar incidents.
Intelligence-Driven Security Planning
Modern security strategies require more than generic best practices—they demand customized solutions based on specific organizational risks. AI enables this personalization by analyzing unique threat landscapes and operational patterns. The resulting security posture reflects actual rather than hypothetical vulnerabilities, creating far more effective protection.
This data-centric approach also optimizes security budgets, directing investments toward the controls that provide the greatest risk reduction for each organization's particular circumstances.
The Evolving Role of AI in Digital Defense
As cyber threats grow in sophistication, AI capabilities continue advancing to meet the challenge. Future developments will likely introduce even more nuanced detection methods and autonomous response mechanisms. This ongoing innovation represents our best hope for maintaining security in an increasingly complex digital ecosystem.
The trajectory suggests a future where AI handles routine security operations entirely, freeing human experts to focus on strategic defense planning and novel threat research. This division promises both enhanced protection and more efficient use of cybersecurity talent.
The Future of Cybersecurity: A Proactive and Intelligent Approach
Next-Generation Threat Identification
Tomorrow's cybersecurity landscape will be defined by anticipatory defense systems. Advanced AI monitors network ecosystems for microscopic irregularities that precede attacks, often detecting threats during their reconnaissance phase. This ultra-early detection shrinks the attack surface dramatically, as malicious actors find their options constrained before launching assaults.
The true power lies in AI's contextual analysis—understanding not just that an anomaly occurred, but why it matters. By connecting seemingly unrelated events across multiple systems, these systems uncover complex attack chains that would escape conventional monitoring tools.
Intelligent Security Orchestration
The future promises security systems that don't just detect threats but autonomously neutralize them. Imagine infrastructure that self-heals—automatically patching vulnerabilities, adjusting firewall rules, and reconfiguring network segments in response to emerging risks. This level of automation doesn't replace human oversight but elevates it, allowing experts to focus on architectural improvements rather than routine maintenance.
As these systems mature, they'll handle increasingly complex decision-making during security incidents. The combination of machine speed and human judgment will create response protocols far more effective than either could achieve independently.
Behavior-Centric Security Culture
Future security platforms will integrate seamlessly with user workflows while maintaining robust protection. By establishing individual behavioral baselines, AI can spot deviations suggesting compromised credentials or insider threats. These insights enable hyper-targeted security training that addresses each user's specific risk factors rather than generic best practices.
The result is a workforce that understands security as a personal responsibility rather than an IT imposition. When employees receive relevant, actionable guidance tailored to their actual work patterns, security compliance improves organically.
Self-Learning Defense Systems
The only constant in cybersecurity is change—a reality that demands equally adaptable defenses. Future AI systems will feature continuous learning loops, incorporating every new attack vector into their protective models in real-time. This creates an evolutionary arms race where defensive measures improve with each attempted breach.
Such adaptability proves particularly valuable against novel attack methodologies. Where traditional signature-based defenses fail against zero-day exploits, self-learning systems identify malicious patterns regardless of their novelty, providing crucial protection during vulnerability windows.