A Holistic Approach: Cybersecurity and Insurance in Harmony
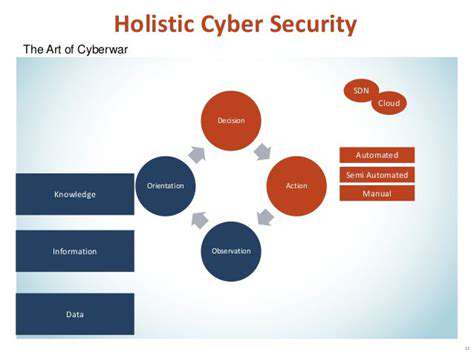
Understanding the Scope of Cybersecurity
In today's digital age, cybersecurity has transcended its traditional boundaries within IT departments, becoming a pervasive challenge that touches every corner of modern existence. Our reliance on digital systems for everything from national infrastructure to personal banking means vulnerabilities in one area can ripple across multiple sectors. Safeguarding this intricate web demands more than technical solutions—it requires a fundamental shift in how we perceive digital risks.
The most effective security strategies recognize that digital systems don't exist in isolation—they're part of an ever-changing ecosystem where human behavior, technological capabilities, and organizational policies intersect. Rather than waiting for breaches to occur, forward-thinking organizations now prioritize understanding these complex relationships to build more resilient systems.
The Importance of Proactive Measures
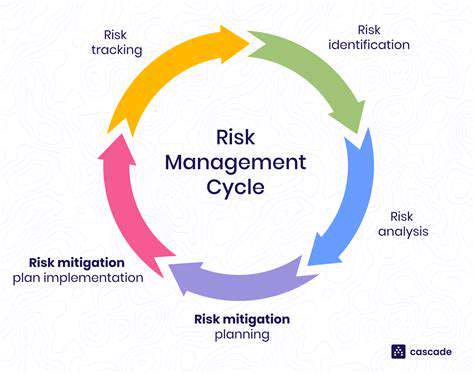
Traditional security approaches that focus solely on responding to incidents are akin to locking the barn door after the horses have bolted. Modern cybersecurity demands anticipation rather than reaction, requiring organizations to stay several steps ahead of potential threats. This shift involves implementing rigorous security protocols, conducting continuous vulnerability assessments, and fostering security-conscious cultures.
Organizations that invest in preventive measures typically experience fewer security incidents and recover more quickly when breaches do occur. By embedding security considerations into every business process from the outset, companies can dramatically reduce their exposure to digital risks.
Human Element in Cybersecurity
No firewall or encryption algorithm can completely compensate for human vulnerabilities. Cybercriminals increasingly target employees through sophisticated social engineering schemes, knowing that even the most robust technical defenses can be bypassed through human error. Regular, engaging training programs that go beyond basic compliance requirements can transform employees from security liabilities into active defenders.
When staff members understand not just security policies but the reasoning behind them, they're far more likely to spot and report potential threats. Practical simulations of phishing attempts and other common attack vectors can dramatically improve an organization's human firewall.
Technological Advancements in Cybersecurity
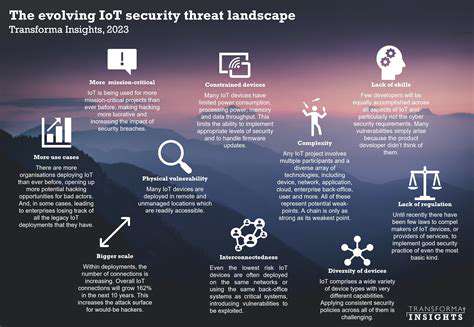
The cybersecurity arms race continues to accelerate, with defenders and attackers locked in an ongoing battle of innovation. Emerging technologies like behavioral analytics and quantum-resistant cryptography promise to reshape the security landscape. However, technology alone isn't a panacea—organizations must thoughtfully integrate new tools with existing infrastructure while considering potential unintended consequences.
Predictive security systems that leverage artificial intelligence can identify subtle patterns that might indicate emerging threats, allowing security teams to intervene before damage occurs. These systems become increasingly effective as they process more data, creating a virtuous cycle of improved protection.
Building a Strong Security Infrastructure
Effective cybersecurity architecture resembles a medieval castle's defenses—multiple concentric rings of protection, each providing backup if another fails. This defense-in-depth approach might combine network segmentation with strict access controls, continuous monitoring, and regular penetration testing. Critical to this strategy is designing systems with the assumption that some breaches will occur, ensuring the impact remains contained.
The most resilient organizations treat security infrastructure as a living system that evolves in response to new threats rather than a static set of controls. Regular audits and red team exercises help identify weaknesses before malicious actors can exploit them.
The Role of Collaboration in Cybersecurity
Cyber threats don't respect organizational boundaries, making information sharing between companies, industries, and governments essential. Collaborative threat intelligence platforms allow participants to benefit from collective experience, spotting emerging attack patterns more quickly. This cooperative approach extends to public-private partnerships that strengthen national cybersecurity postures.
When organizations share anonymized data about attacks they've experienced, the entire community gains valuable insights into evolving threat actor tactics. This collaborative mindset represents a significant shift from the traditional view of cybersecurity as a competitive advantage to be guarded jealously.
The Continuous Evolution of Cybersecurity
The only constant in cybersecurity is change—attack methods evolve, new technologies emerge, and regulatory landscapes shift. Security professionals must cultivate a mindset of continuous learning, staying current with both technological developments and the changing motivations of threat actors. This requires dedicating resources to ongoing education and maintaining mechanisms for rapid adaptation.
Organizations that institutionalize processes for regularly reviewing and updating their security postures are better positioned to respond to emerging threats. Building flexibility into security strategies ensures they remain effective as the digital landscape transforms.