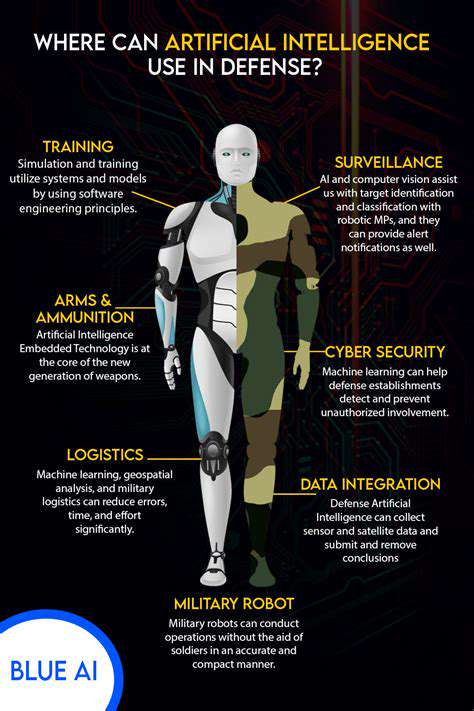
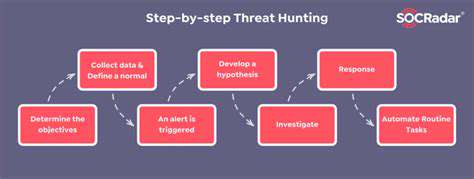
Automating Routine Tasks
Modern threat hunting often involves sifting through vast amounts of security data, a process that can be incredibly time-consuming and resource-intensive. Analysts are frequently bogged down by repetitive tasks like log file parsing, event correlation, and pattern identification. These repetitive activities, while necessary, can often detract from the strategic, higher-level thinking required for effective threat detection and response. Automating these routine tasks allows analysts to focus on more complex and strategic aspects of the threat hunting process, such as developing threat models, identifying vulnerabilities, and responding to advanced persistent threats (APTs).
By leveraging artificial intelligence (AI) and machine learning (ML) capabilities, security teams can automate the initial stages of the threat hunting process. AI can be trained on historical data to identify anomalies, suspicious patterns, and potential threats. This allows analysts to quickly zero in on the most critical issues, freeing them to investigate the findings in greater depth and detail, ultimately accelerating the response time for potential threats.
Enhancing Threat Detection Accuracy
AI algorithms can analyze massive datasets with unparalleled speed and accuracy, identifying subtle patterns and anomalies that might easily be missed by human analysts. This heightened accuracy in threat detection is crucial in today's complex cybersecurity landscape where sophisticated threats are constantly evolving. By automating the initial stages of threat hunting, AI tools can significantly improve the overall security posture of an organization. This proactive approach allows for faster detection and response times, reducing the potential impact of successful attacks.
Beyond simply identifying threats, AI can also help prioritize them based on factors such as the likelihood of a successful attack, the potential impact, and the resources required for mitigation. This prioritization allows security teams to focus on the most critical threats first, ensuring that resources are allocated effectively and efficiently. The result is a more comprehensive and effective security strategy.
Empowering Strategic Decision-Making
By offloading the mundane, repetitive aspects of threat hunting, AI frees up analysts to engage in strategic tasks that require human judgment and critical thinking. This includes developing comprehensive threat models, identifying vulnerabilities in systems and applications, and proactively strengthening security defenses. This shift in focus allows analysts to move beyond reactive threat response and embrace a more proactive and strategic approach to cybersecurity. This strategic shift also allows for better allocation of limited resources and more effective collaboration between teams.
The insights gained from AI-driven threat hunting can also be used to improve incident response procedures. By analyzing patterns and trends, AI can help security teams develop more effective strategies for dealing with future threats. This continuous learning and adaptation is crucial in today's rapidly evolving threat landscape. Ultimately, automated threat hunting empowers organizations to make more informed and strategic decisions regarding their security posture.
The Future of Threat Hunting: AI as a Strategic Partner
The Rise of AI-Powered Threat Detection
Artificial intelligence (AI) is rapidly transforming the landscape of cybersecurity, particularly in the realm of threat hunting. AI algorithms can analyze vast quantities of security data, identifying patterns and anomalies that human analysts might miss, significantly enhancing threat detection capabilities. This automated approach allows for proactive threat identification, enabling organizations to respond to emerging threats before they cause significant damage. These advanced systems can learn from past incidents and adapt to new attack vectors, making them increasingly effective in a dynamic threat environment.
AI-powered threat hunting tools can process massive datasets, including logs, network traffic, and user activity, in a fraction of the time a human analyst could. This speed and scale are crucial for identifying threats in real-time, allowing for immediate mitigation. By automating the process, AI frees up human analysts to focus on more complex tasks, such as incident response and strategic planning.
Enhanced Threat Hunting Efficiency
AI's ability to analyze massive datasets and identify subtle patterns is a game-changer for threat hunting. Human analysts are often limited in their capacity to process the sheer volume of data generated by modern IT infrastructures. AI algorithms can sift through this data, flagging potentially malicious activities that might be overlooked by human eyes, leading to a more efficient and effective threat hunting process.
Furthermore, AI can continuously learn and adapt, improving its accuracy and efficiency over time. This continuous learning capability means that the threat hunting process becomes more refined and responsive to evolving threats. By learning from past incidents, AI tools can proactively identify and address emerging threats more effectively.
Improved Accuracy and Speed in Threat Hunting
AI's ability to quickly analyze massive datasets significantly enhances the speed and accuracy of threat hunting. Traditional threat hunting often relies on manual analysis, which can be time-consuming and prone to human error. AI-powered systems, on the other hand, can identify patterns and anomalies in data far more quickly and accurately, leading to quicker response times and minimizing potential damage.
Proactive Threat Detection and Prevention
A key advantage of AI in threat hunting is its ability to detect threats proactively. AI algorithms can identify anomalies and unusual behavior that may indicate an imminent threat, allowing organizations to take preventative measures before the attack occurs. This proactive approach is crucial for mitigating the impact of sophisticated cyberattacks.
The Role of Human Analysts in the AI-Driven Future
While AI is revolutionizing threat hunting, human analysts remain critical to the process. AI systems can automate many tasks, but human expertise is still essential for interpreting results, contextualizing findings, and making complex decisions about responses to threats. The future of threat hunting likely involves a collaborative approach where AI supports human analysts, enabling them to focus on strategic planning and high-level decision-making.
AI can be a powerful tool for identifying potential threats, but human judgment and expertise are vital for evaluating the potential impact of those threats. Human analysts can use AI insights to determine the severity of a threat and prioritize responses, ensuring that resources are allocated effectively.
Challenges and Considerations for Implementing AI in Threat Hunting
While the potential benefits of AI in threat hunting are substantial, organizations must address certain challenges. One significant consideration is the need for robust data security and privacy measures to protect sensitive information used to train and operate AI models. Maintaining the integrity of data is critical to ensure the accuracy and reliability of AI-powered threat hunting tools.
Another challenge is ensuring the ethical and responsible use of AI in threat hunting. Organizations need to carefully consider the potential biases in data and algorithms and implement strategies to mitigate these biases. Transparency in the AI decision-making process is also crucial to build trust and ensure accountability.