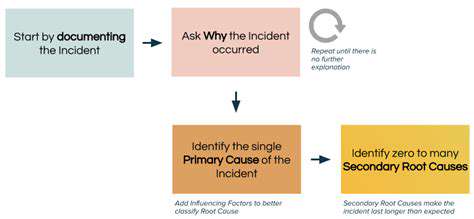
Comprehending ZTNA's Foundational Concepts
Adopting Zero Trust Network Architecture demands thorough comprehension of its core tenets, centered on perpetual verification rather than implicit trust. Conventional security frameworks depend on boundary protections, whereas ZTNA presumes dangers might originate internally or externally. Consequently, each access attempt requires authentication, permission, and ongoing scrutiny to maintain security standards.
This methodology prioritizes rigorous identity confirmation, precise permission settings, and constant tracking of user actions. Following these fundamental rules enables enterprises to dramatically shrink their vulnerability exposure and enhance their protective stance. Security personnel must effectively communicate ZTNA's basic ideas to stakeholders to promote easier adoption and enterprise-wide approval.
Evaluating Enterprise Preparedness and Systems
Prior to implementing ZTNA systems, companies need to comprehensively examine their current infrastructure and readiness for this revolutionary security approach. This includes analyzing network design, current protective measures, and access behaviors to pinpoint deficiencies and possible integration obstacles. A complete evaluation aids in developing a precise implementation strategy and verifies all essential elements conform to ZTNA standards.
Businesses should additionally assess their cloud integration progress, remote work regulations, and application structures. These elements affect ZTNA policy creation and selection of implementation methods, whether local, cloud-hosted, or combined. Proper evaluation reduces disturbances and guarantees the updated security system works harmoniously with current setups.
Choosing the Optimal ZTNA System for Your Business
Selecting a suitable ZTNA solution necessitates thoughtful examination of an organization's unique demands, growth potential, and technological environment. ZTNA providers vary in quality; certain options might provide superior integration options, user interfaces, or threat identification tools. Businesses must assess suppliers according to their security offerings, implementation simplicity, and compatibility with multi-cloud or mixed settings.
During the selection phase, organizations should also evaluate the system's capacity to deliver detailed permission settings, intuitive interfaces, and comprehensive tracking functions. Involving representatives from security, technology, and operational departments helps confirm the selected solution matches business objectives and regulatory needs, enabling more efficient implementation.
Applying Identity Verification and Permission Systems
A fundamental aspect of ZTNA adoption involves creating a strong Identity and Access Management (IAM) system that supports precise permission settings. This requires combining multiple verification methods, permission levels based on roles, and ongoing identity checks to guarantee only approved individuals access particular assets.
Enterprises might also implement federated identity solutions and unified login systems to simplify authentication across various platforms. Correctly arranged IAM reduces risks from internal threats and credential abuse, prevalent vulnerabilities in current digital security scenarios. Regular oversight and periodic IAM policy reviews further boost protective measures.
Creating a Protected Network Structure
Developing a network structure appropriate for ZTNA entails dividing the network into smaller, controllable sections that implement strict access rules. Micro-segmentation permits companies to separate vital systems and restrict internal movement during security incidents. This design supports zero-trust concepts by allowing access only when user credentials, device status, and situational factors meet requirements.
Incorporating protected access points, like Software-Defined Perimeters (SDP), improves management of resource access irrespective of user location. Furthermore, adding threat data and live analysis tools to network planning enables early identification of and reaction to questionable behaviors, strengthening protections.
Implementing Ongoing Oversight and Rule Application
Successful ZTNA implementation depends substantially on constant surveillance of user actions, device conditions, and network communications. This persistent observation assists in promptly detecting irregularities, potential dangers, or policy infractions. Security tracking systems and behavior analysis tools serve as crucial elements for immediate awareness and threat discovery.
Dynamically applying regulations according to situational data, including user whereabouts or device security status, ensures protective measures adjust to evolving conditions. Regular policy refinements and swift reaction to warnings remain essential for preserving a durable zero-trust setup.
Instruction and Adaptation Strategies for Seamless Implementation
Moving to ZTNA mandates extensive training initiatives to ensure all participants comprehend their functions and duties within the new security framework. Teaching users about safe access methods and possible hazards promotes adherence and lessens opposition to modifications. Adaptation plans should incorporate transparent messaging, gradual introductions, and continuous assistance.
Additionally, including technology and security staff in preparation and execution stages guarantees technical preparedness and successful combination with existing arrangements. Establishing a security-conscious environment proves crucial for sustained ZTNA effectiveness and general organizational durability.
Advantages of Implementing ZTNA
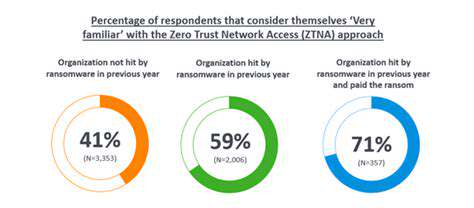
Strengthened Protection and Minimized Vulnerabilities
Zero Trust Network Access (ZTNA) considerably improves an enterprise's security by validating every access attempt no matter the user's position. This technique reduces data compromise and cyberattack risks through stringent control over resource accessibility.
Conventional protection models frequently depend on boundary defenses susceptible to breaches, creating weaknesses. ZTNA alters this approach by employing perpetual verification, substantially increasing difficulty for attackers to infiltrate networks.
Enhanced User Satisfaction and Adaptability
ZTNA delivers smooth, secure application access from any device or place, encouraging efficiency and teamwork. This adaptability proves especially valuable in contemporary remote work scenarios where staff require dependable connectivity independent of physical location.
Unlike traditional VPNs that may prove unwieldy and inefficient, ZTNA offers simplified verification, decreasing delays and user annoyance. This results in increased contentment and superior operational productivity.
Precise Permission Settings and Regulation Application
A primary benefit of ZTNA involves its capacity to implement detailed access rules according to user identification, device security status, and situational context. This ensures users obtain access solely to necessary resources, limiting excessive exposure.
Companies can tailor permissions for various roles or divisions, safeguarding confidential information while maintaining efficiency. This specific method reduces dangers from internal risks and information exposure.
Financial Efficiency and Streamlined Administration
ZTNA adoption can generate substantial savings by removing extensive hardware requirements and complicated VPN systems. It simplifies network oversight by consolidating security policies and access management within cloud platforms.
Technology teams gain from easier setup and upkeep, allowing focus on strategic projects. This efficient oversight leads to quicker reactions to security events and reduced operational interruptions.
Cloud and Mixed Environment Compatibility
As businesses increasingly embrace cloud services and combined infrastructure, ZTNA provides a matching solution ensuring uniform security standards across all platforms. It enables protected cloud application access without revealing internal networks.
This flexibility remains critical for modern businesses pursuing agility and scalability. ZTNA's structure supports effortless integration with multiple cloud services and local resources, delivering a cohesive security approach.
Regulatory Conformity Advantages
Numerous sectors encounter rigorous legal mandates concerning data security and access limitations. ZTNA assists organizations in satisfying these demands through comprehensive activity records and automatic compliance enforcement.
By guaranteeing access only under approved circumstances, ZTNA facilitates legal and regulatory obedience, decreasing fine risks. It also improves clarity, simplifying audit procedures.
Forward-Looking Protection Approach
Embracing ZTNA equips enterprises for upcoming cybersecurity obstacles by providing an expandable and adjustable protection system. As threats develop, ZTNA's continuous verification and adaptable regulations can be modified to address emerging risks successfully.
Committing to ZTNA means establishing a robust security position capable of adjusting to technological progress and shifting business requirements. This preventive strategy ensures extended safeguarding for critical assets.