Understanding Phishing Attacks
Phishing remains one of the most persistent cyber threats, targeting individuals and organizations alike. These deceptive schemes aim to harvest sensitive data like login credentials, financial information, and personal identification details. Fraudsters craft convincing emails, websites, and messages that mimic trusted sources, playing on human psychology to bypass skepticism. What makes these attacks particularly dangerous is their ability to evolve constantly, adapting to new security measures and user awareness. The consequences can range from identity theft to significant financial losses.
Recognizing phishing attempts requires constant vigilance and updated knowledge of current tactics. Many people mistakenly believe they can easily spot fraudulent communications, but modern phishing campaigns often employ professional design and psychological triggers. Security experts emphasize that education and awareness form the first line of defense against these social engineering attacks.
Identifying Phishing Emails
Suspicious emails frequently exhibit several telltale signs that careful readers can detect. The language often creates artificial urgency, with subject lines like Immediate Action Required or Security Alert. While some contain obvious grammatical errors, others appear polished but include subtle inconsistencies. Never trust emails that demand sensitive information or contain threatening consequences for non-compliance. Always verify sender addresses by hovering over links to reveal their true destinations.
Additional red flags include mismatched sender names and email domains, unusual requests for personal data, and poor formatting. Phishing attempts frequently spoof legitimate organizations but use slight variations in email addresses or website URLs. When in doubt, contact the organization directly through official channels rather than responding to the email.
Recognizing Phishing Websites
Fraudulent websites often mirror legitimate ones with impressive accuracy, copying logos, layouts, and even security certificates. However, careful examination usually reveals inconsistencies in design elements or content quality. Always inspect the URL carefully before entering any credentials, as phishing sites often use subtle misspellings or extra characters in domain names. The absence of HTTPS encryption or invalid security certificates should immediately raise suspicion.
Modern browsers often warn users about potentially dangerous sites, but these warnings shouldn't be the only line of defense. Bookmark frequently visited financial and shopping sites rather than clicking links from emails. If something feels off about a website's appearance or behavior, trust your instincts and exit immediately.
Protecting Yourself from Phishing
Building robust digital habits significantly reduces vulnerability to phishing attempts. Use unique, complex passwords for different accounts and enable multi-factor authentication wherever possible. Keep all software updated, as patches often address security vulnerabilities that phishers exploit. Avoid clicking links in unsolicited messages - instead, navigate directly to websites through bookmarks or typed URLs.
Reporting Phishing Attempts
Reporting suspicious communications helps protect the broader community from similar attacks. Forward phishing emails to your organization's security team or to anti-phishing organizations like the Anti-Phishing Working Group. Include complete details like headers, sender information, and any attachments to aid investigators. Many email providers offer built-in reporting tools that automatically analyze and block malicious content.
Staying Informed About Phishing Techniques
Cybercriminals continuously refine their tactics, making ongoing education essential. Follow cybersecurity news from reputable sources and participate in security awareness training. Understanding emerging trends helps individuals and organizations stay one step ahead of attackers. Many cybersecurity firms publish regular threat reports detailing new phishing methodologies and prevention strategies.
Exploiting Software Vulnerabilities: Zero-Day and Known Exploits
Zero-Day Exploits: The Unseen Threat
Zero-day vulnerabilities represent the most dangerous class of security flaws, as they're unknown to vendors and therefore unpatched. Attackers who discover these vulnerabilities can wreak havoc before defenses can be developed. These exploits frequently target high-value systems, with potential impacts ranging from data theft to complete system compromise. The cybersecurity community considers zero-days particularly concerning because they offer attackers a stealthy advantage.
The underground market for zero-day exploits has grown significantly, with some vulnerabilities commanding six-figure prices. This economic incentive drives continuous research into finding new vulnerabilities across all major software platforms. Organizations must implement defense-in-depth strategies to mitigate risks from these unknown threats.
Known Exploits: Leveraging Existing Weaknesses
While less sophisticated than zero-days, known vulnerabilities continue to enable countless attacks due to poor patch management. Many organizations struggle with timely updates, leaving systems exposed to well-documented threats. The gap between vulnerability disclosure and patch installation creates a window of opportunity that attackers eagerly exploit.
Regular vulnerability scanning and prompt patching remain the most effective defenses against known exploits. Automated patch management solutions can help organizations stay current, especially for large fleets of devices. Security teams should prioritize critical vulnerabilities based on potential impact and existing exploit activity.
Exploit Techniques and Tactics
Attackers employ diverse methods to exploit vulnerabilities, often combining technical flaws with social engineering. Initial access might come through a phishing email containing a malicious attachment, followed by privilege escalation through unpatched system vulnerabilities. Understanding these attack chains helps security professionals develop more effective defensive strategies.
The Role of Vulnerability Databases
Resources like the National Vulnerability Database (NVD) provide critical information about disclosed vulnerabilities, including severity ratings and patch availability. Security teams should regularly consult these databases to identify relevant threats to their environment. Many organizations integrate vulnerability feeds into their security operations centers for real-time monitoring.
The Importance of Security Awareness Training
Technical controls alone cannot prevent all exploitation attempts. Comprehensive security training helps employees recognize and avoid behaviors that could lead to system compromise. Regular simulated phishing tests and vulnerability awareness sessions keep security top-of-mind throughout an organization.
Malicious Downloads: The Hidden Threat in Filesharing
Malicious Software Camouflaged as Legitimate Files
The line between legitimate and malicious downloads has blurred significantly in recent years. Attackers invest substantial resources in making their payloads appear harmless, often mimicking popular software installers or document formats. Some even purchase expired digital certificates to sign their malware, making it appear trustworthy to security software.
Users should verify downloads through multiple channels before opening files, especially from unfamiliar sources. Checking file hashes against official sources and scanning downloads with multiple antivirus engines can help identify potentially malicious content.
Exploiting Vulnerabilities in Software
Malicious downloads frequently target both known and unknown vulnerabilities in commonly used applications. Outdated software, especially browser plugins and office suites, present particularly attractive targets. Some attacks bundle multiple exploits to increase their chances of successful infection across different system configurations.
The Role of Social Engineering in Downloads
Psychological manipulation plays a crucial role in convincing users to download and execute malicious files. Attackers craft convincing narratives around their payloads, such as fake invoice attachments or urgent software updates. The most successful campaigns leverage current events or popular trends to increase their credibility.
The Importance of Strong Security Practices
Implementing application whitelisting can prevent unauthorized executables from running, regardless of how they enter the system. Network segmentation limits the potential damage from successful infections, while robust backup strategies ensure quick recovery if malware does compromise systems.
Remote Desktop Protocol (RDP) Exploits: Unsecured Access Points
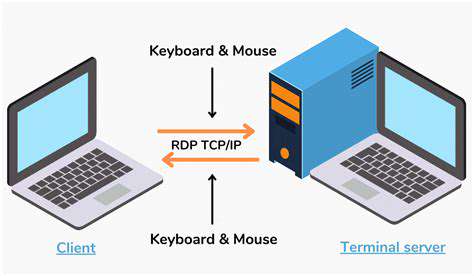
Remote Desktop Protocol (RDP) Architecture
Microsoft's Remote Desktop Protocol has become indispensable for remote work but presents significant security challenges if misconfigured. The protocol's complexity creates multiple potential attack surfaces, from authentication mechanisms to data transmission channels. Proper implementation requires careful consideration of encryption standards and access controls.
RDP Security Considerations
The dramatic increase in RDP exposure during remote work transitions has made it a prime target for attackers. Brute force attacks against RDP endpoints have surged, with automated tools testing thousands of credential combinations. Network-level protections like VPNs and jump servers can significantly reduce this attack surface.
RDP Deployment and Configuration
Secure RDP deployment requires more than enabling the service and opening firewall ports. Organizations should implement account lockout policies, restrict access by IP address when possible, and consider using Remote Desktop Gateway for additional security layers. Regular audits of RDP access logs help identify suspicious activity patterns.
RDP Troubleshooting
Connection issues often stem from network configuration problems or authentication failures. Detailed logging and network packet analysis can help diagnose stubborn RDP connectivity problems. For persistent issues, rebuilding the RDP configuration or testing with different client versions may resolve compatibility problems.