Implementing Secure Development Practices
The Critical Need for Secure Development
Secure development methodologies are essential in our interconnected digital landscape, particularly for software supply chains. A single vulnerability in a software component can have far-reaching consequences, potentially exposing confidential information, disrupting services, and creating substantial financial liabilities. Addressing security concerns late in the development cycle leads to expensive remediation efforts that impact project timelines. Making security a priority from project inception ensures software reliability and builds user trust.
Adopting Secure Coding Standards
Following established secure coding guidelines helps minimize software vulnerabilities. These best practices include proper input validation, prevention of injection attacks, and security-focused design patterns. Incorporating these standards throughout development helps identify and mitigate security risks early, resulting in more resilient software products.
Peer code reviews and security-focused code analysis further enhance software quality. These review processes help catch potential security issues that individual developers might overlook during initial implementation.
Integrating Security Testing
Security testing should occur throughout the entire development lifecycle rather than just before release. Various testing methodologies, including static code analysis, dynamic testing, and penetration testing, provide complementary security verification at different development stages. Early security testing enables prompt vulnerability identification and remediation, preventing more serious issues later in the project.
Developer Security Education
Developers serve as the first line of defense in secure software creation. Comprehensive security training equips development teams with knowledge about common vulnerabilities and secure coding techniques. This education should cover emerging threats and reinforce security policies. Continuous learning helps developers maintain current security knowledge as threats evolve.
Establishing Secure Development Processes
Formalized secure development procedures create a structured approach to building secure software. Clear security responsibilities, documented coding standards, automated security tools, and defined vulnerability management processes all contribute to stronger security. Well-established processes foster a security-conscious culture that improves software quality throughout the organization.
Proactive Monitoring and Incident Response
The Importance of Proactive Monitoring
Proactive security monitoring involves continuous observation and analysis of software development activities and related ecosystems. This includes tracking open-source components, dependencies, and potential security weaknesses. Effective proactive monitoring identifies risks before they develop into serious security incidents, representing a crucial preventative measure against vulnerabilities introduced through external sources.
This approach extends beyond simple alert monitoring. Continuous scanning and analysis enable organizations to detect and mitigate threats early, preventing costly security breaches before they occur.
Establishing Security Metrics
Defining meaningful security metrics is fundamental for effective proactive monitoring. These measurements should encompass vulnerability discovery rates, remediation timelines, and overall supply chain security health. These metrics help organizations set realistic security goals and track improvement progress, providing visibility into current security status and identifying areas needing attention.
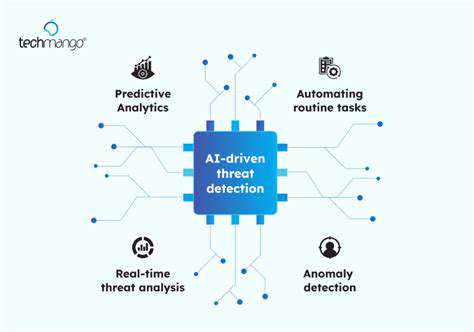
Automated Vulnerability Detection
Automated scanning tools play a vital role in proactively identifying security weaknesses in software components. These tools analyze code, dependencies, and configurations to detect potential vulnerabilities, enabling focused remediation efforts. Implementing comprehensive scanning across the entire software supply chain provides thorough security assessment and helps maintain security awareness.
Security Information Management
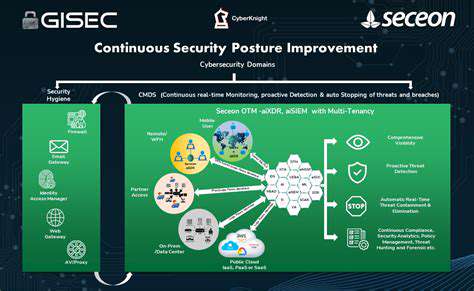
Security Information and Event Management (SIEM) systems collect and analyze security-related data from across the software supply chain. By correlating security events, these systems detect anomalies and suspicious patterns, providing valuable threat intelligence. These insights help prioritize vulnerabilities based on severity and potential impact, enabling more effective security responses.
Effective Incident Response
A well-defined incident response plan is essential for addressing supply chain security incidents. This plan should detail procedures for detection, containment, recovery, and stakeholder communication. Proactive monitoring facilitates early incident detection, minimizing damage and enabling rapid response. Prepared response plans ensure coordinated actions when security incidents occur.
Continuous Security Improvement
Ongoing monitoring and improvement form the foundation of effective supply chain security. Regular evaluation of security measures, identification of improvement opportunities, and adaptation to emerging threats maintain strong security postures. This continuous cycle of assessment and enhancement ensures supply chain resilience against evolving security challenges.
Security Collaboration
Effective collaboration and communication are essential for supply chain security success. Clear communication channels between development teams, security personnel, and supply chain partners facilitate information sharing about threats and best practices. This collaborative approach ensures all stakeholders understand potential risks and contribute to security mitigation efforts, creating a more secure software ecosystem.