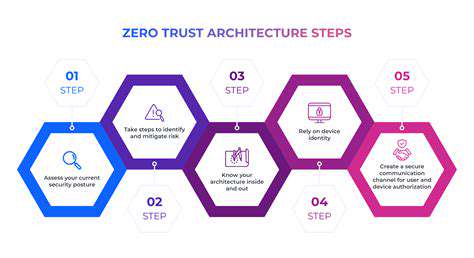
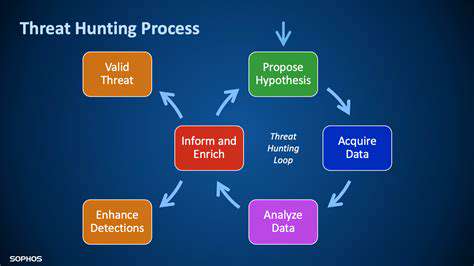
Predictive Modeling for Threat Intelligence
Predictive modeling, a cornerstone of AI-powered security analysis, extends far beyond basic threat identification. Modern security systems utilize machine learning to process enormous volumes of security data, network patterns, and user activities to forecast potential risks before they emerge. This forward-thinking strategy enables security teams to deploy preventive measures, strengthening defenses against new and complex attack methods while dramatically decreasing breach risks.
When systems detect deviations from normal operational baselines, predictive models can highlight possible malicious actions. This early alert mechanism gives security professionals crucial time to intervene, containing threats before escalation and enhancing an organization's overall security framework.
Proactive Threat Hunting and Response
Advanced predictive technologies transform security operations from reactive monitoring to active threat pursuit. These intelligent systems examine data streams to uncover signs of system compromise or ongoing malicious activities, permitting security personnel to investigate and neutralize threats preemptively. This shift in approach effectively shrinks potential attack vectors and lessens breach consequences.
Additionally, by automating routine threat detection processes, AI solutions allow security analysts to concentrate on higher-level strategic initiatives. This optimized workflow leads to more efficient threat response protocols and strengthens organizational security measures overall.
Adaptive Security Measures
The most valuable aspect of AI-powered security lies in its dynamic adaptability. Security systems continuously refine their models using fresh data, enabling them to recognize evolving attack methodologies and adjust defensive strategies accordingly. This evolutionary capability proves essential in our rapidly changing digital threat environment, ensuring protection against increasingly sophisticated cyber attacks.
Enhanced Security Posture Through Data Analysis
AI-driven security analytics offer substantial advantages by providing deeper insights into security data. By examining multiple data streams - including network activity, user behaviors, and system records - advanced algorithms can detect subtle irregularities often missed by conventional tools. This comprehensive analysis enables more informed security decisions, resulting in stronger, more flexible protective measures.
The intelligence gathered from this process helps shape targeted security protocols, creating a more anticipatory and efficient security framework. Such analytical capabilities form the foundation for building resilient, adaptive security strategies.
Automated Threat Hunting and Incident Response

Automated Threat Hunting: A Powerful Tool
Modern threat detection employs sophisticated algorithms to actively identify and address potential security issues within networks. This automated approach drastically cuts the time and resources needed for manual investigations, allowing security professionals to focus on strategic initiatives. Automating initial threat detection provides organizations with a critical advantage in today's constantly evolving cyber landscape. This proactive methodology helps detect and resolve emerging threats before they develop into major incidents.
The speed and efficiency of automated systems prove particularly valuable in our fast-paced digital world. With organizations facing relentless waves of sophisticated threats, automated tools can swiftly process massive data volumes, spotting patterns and anomalies that human analysts might overlook.
Key Benefits of Automation
Automated systems offer significant scalability advantages for threat detection and response. As organizations expand their digital presence, the volume of data requiring analysis grows exponentially. Traditional manual processes struggle to handle this scale effectively. Automated solutions adapt effortlessly to increasing demands, maintaining consistent security standards regardless of organizational size.
Another crucial advantage is the reduction of human error. While security analysts remain essential, they can experience fatigue and oversight. Automated tools eliminate these potential weaknesses, delivering consistent and precise threat detection regardless of workload pressures. This results in more dependable security outcomes across all operations.
Data Analysis and Pattern Recognition
Advanced automated tools employ sophisticated data analysis techniques to identify patterns in network traffic, system logs, and user behaviors. These algorithms can process enormous data sets rapidly, enabling quick identification of suspicious activities.
The ability to detect subtle indicators of malicious behavior represents a critical feature of automated systems. These tools can spot minor deviations from normal operations that may signal emerging threats, often before significant damage occurs. This allows security teams to take preventive action and minimize potential harm.
Integration with Security Information and Event Management (SIEM)
Effective threat detection requires seamless integration between automated tools and existing SIEM systems. This combination provides a comprehensive security event overview, enabling systems to correlate diverse data points and identify threats more accurately. Cross-system data correlation creates a complete security picture, allowing for more informed responses to potential threats.
Future Trends in Automated Threat Hunting
The future of automated security promises significant advancements through ongoing AI and machine learning development. These technologies will enable systems to learn from past incidents, adapt to new threats, and predict vulnerabilities more precisely. AI integration will substantially improve threat detection accuracy, leading to more preventive cybersecurity approaches.
As device and system interconnectivity grows, more advanced solutions will be necessary to manage the resulting data volume. These developments will create more seamless and effective security measures for organizations of all sizes.
Enhanced Security Posture Through Continuous Monitoring
Strengthening Authentication Protocols
Robust authentication forms the foundation of effective security. Implementing multi-factor authentication across all systems and accounts is essential. This layered security approach significantly reduces unauthorized access risks, even with compromised credentials. Requiring multiple verification methods creates substantial barriers for potential attackers, protecting sensitive data and critical systems.
Beyond MFA implementation, regular security audits and penetration testing of authentication systems are vital. These evaluations identify vulnerabilities in current configurations and highlight areas needing improvement. Proactive testing ensures authentication systems remain resilient against evolving threats, building stronger security foundations over time.
Improving Data Encryption and Integrity
Data encryption serves as a fundamental security component. Encrypting sensitive information during transmission and storage is critical. This ensures data remains protected even if accessed without authorization. Using strong encryption standards and proper key management provides substantial protection against data breaches.
Maintaining data integrity is equally important. Implementing verification methods like checksums and digital signatures confirms data authenticity and completeness. This rigorous approach prevents unauthorized modifications, ensuring information reliability and maintaining system trust.
Implementing Advanced Threat Detection and Response
Proactive threat detection is essential for identifying and mitigating security risks. Utilizing intrusion detection systems and SIEM solutions helps detect anomalies and suspicious activities. These systems can recognize patterns indicating potential threats, enabling quick response and containment.
Developing comprehensive incident response plans is crucial. These plans should outline procedures for handling security incidents from detection through recovery. Clear communication channels and defined responsibilities ensure efficient incident management, minimizing damage and disruption. This demonstrates commitment to maintaining secure environments.
Advanced threat hunting capabilities are increasingly important. This proactive approach actively searches for compromise indicators. This strategy can identify sophisticated threats that might bypass traditional security measures, proving critical for preventing major breaches.
The Future of Security Analytics: Proactive Threat Prediction
Predictive Modeling for Early Detection
Modern security analytics are transforming threat detection through proactive prediction capabilities. Machine learning systems analyze extensive security data sets, identifying patterns that may signal emerging threats. This predictive ability allows security teams to address vulnerabilities proactively, significantly reducing breach impacts.
By examining historical data, these systems learn to recognize subtle malicious activity indicators, such as unusual user behavior or suspicious network patterns. This enables early threat identification often missed by conventional systems, providing valuable response time.
Enhanced Threat Intelligence Gathering
AI dramatically improves threat intelligence collection by automatically processing data from multiple sources, including OSINT and threat feeds. This automation helps security teams stay current with emerging threats and adjust defenses in real-time.
Traditional intelligence methods rely heavily on manual analysis, which can be slow and incomplete. Automated tools provide more comprehensive threat landscape views, ensuring organizations remain prepared for new security challenges.
Automated Response Systems
Modern security analytics can automate threat responses, reducing breach containment and remediation times. Upon threat detection, systems can automatically execute predefined actions like isolating affected systems or blocking malicious traffic.
This automation significantly improves response speeds, minimizing potential damage. It also allows security analysts to focus on complex strategic tasks rather than routine response procedures.
Improved User and Entity Behavior Analytics (UEBA)
Advanced UEBA systems analyze user and system behaviors to identify anomalies potentially indicating malicious activity. These systems can detect unusual access patterns or suspicious data movements that may signal emerging threats.
This enhanced behavioral visibility proves critical for identifying insider threats or compromised accounts. Continuous monitoring enables proactive intervention when detecting behavioral deviations, helping prevent potential breaches.
Proactive Vulnerability Management
Security analytics can identify system vulnerabilities before exploitation. By scanning for weaknesses in real-time across software and configurations, these systems help organizations strengthen defenses proactively.
This approach significantly reduces potential attack surfaces and exploit risks. Analytics can also prioritize patching efforts, ensuring resolution of most critical vulnerabilities first for maximum security improvement.
Dynamic Security Policies
Modern security analytics enable dynamic policy adjustments based on real-time threat intelligence and evolving needs. This adaptability proves crucial in our rapidly changing threat environment where static policies often fall short.
Rather than fixed rules, these systems adapt security measures based on current threat conditions, enhancing control effectiveness. This dynamic approach allows rapid response to emerging threats while maintaining strong security postures.
Cost-Effective Security Operations
By automating tasks, improving threat detection, and enabling proactive measures, advanced security analytics can generate significant organizational cost savings. Faster response times, reduced downtime, and fewer breaches translate to substantial financial benefits.
These systems allow security teams to focus on strategic initiatives, creating more efficient security operations. The long-term advantages of proactive threat prediction and mitigation substantially outweigh initial technology investments.