Leveraging AI for Proactive Threat Hunting

Proactive Threat Detection
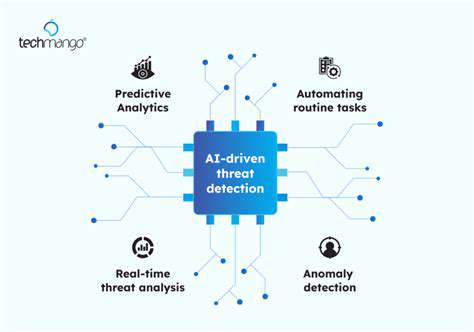
Modern AI-driven threat detection platforms process enormous datasets in milliseconds, spotting irregularities that signal potential breaches. Unlike conventional tools, these systems uncover subtle deviations in user activity, network flows, and log entries that human analysts might overlook. This automated vigilance allows security teams to intercept threats during their early stages, dramatically reducing potential organizational impact. The real advantage lies in how these tools continuously evolve, learning from each new data point to refine their detection capabilities.
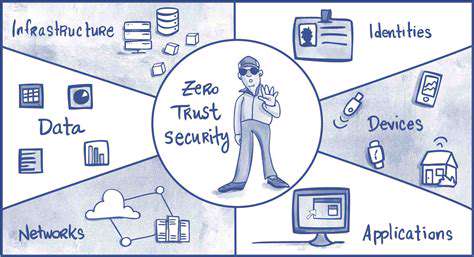
In our current digital ecosystem, perimeter defenses alone prove inadequate against sophisticated attacks. The scalable analysis provided by AI solutions addresses this gap effectively. What sets these systems apart is their dynamic nature - they don't just follow predefined rules but develop new detection methodologies as threats mutate. This evolutionary approach ensures defenses remain relevant against novel attack vectors that bypass traditional security measures.
Predictive Modeling for Security
Security teams now harness machine learning to analyze historical breach data, identifying precursor patterns that often precede attacks. This forecasting capability transforms cybersecurity from reactive to anticipatory. Organizations implementing predictive models gain the advantage of addressing vulnerabilities before exploitation occurs, optimizing their security resource allocation.
The predictive approach fundamentally changes risk management strategies. By recognizing developing threat patterns, companies can implement preemptive controls rather than scrambling post-breach. This shift not only hardens defenses but also provides measurable reductions in incident response costs and operational disruptions.
Automated Response Systems
When breaches occur, AI-driven response mechanisms spring into action within seconds. These systems execute predefined containment protocols while simultaneously assessing threat severity. This instantaneous reaction is crucial for limiting data exposure and maintaining business continuity during security events. Automated triage ensures critical incidents receive immediate attention while lower-risk alerts queue for human review.
Enhancing Human Expertise
Rather than replacing security personnel, AI serves as a force multiplier. By handling repetitive monitoring tasks, these systems allow analysts to concentrate on strategic initiatives like threat hunting and security architecture. The most effective security operations combine AI's processing power with human intuition and creativity, creating a synergy that outperforms either approach alone. This collaboration enables organizations to derive actionable insights from security data that would otherwise remain buried in noise.
Enhancing Security Operations with Automation
Automating Threat Detection
Contemporary security operations demand continuous monitoring that only automated systems can provide sustainably. These platforms scrutinize security telemetry around the clock, flagging anomalies with precision that human-operated systems can't match. The integration of these tools with existing security infrastructure creates a cohesive defense ecosystem where data flows seamlessly between components.
Real-Time Threat Intelligence Integration
Dynamic defense systems ingest live threat feeds, incorporating the latest indicators of compromise into their detection algorithms. This constant knowledge update is vital for identifying novel attack methods as they emerge across the digital landscape. The systems' ability to contextualize this intelligence with internal telemetry creates a powerful detection mechanism.
Predictive Threat Modeling
Forward-looking security teams employ AI to simulate potential attack scenarios based on current vulnerabilities and historical data. This modeling identifies weak points in defenses before adversaries can exploit them, enabling preemptive hardening of systems. The predictive approach is particularly valuable for organizations managing complex, distributed infrastructures.
Enhanced Security Monitoring
AI augmentation transforms security monitoring from a passive activity to an intelligent analytical process. These systems don't just collect data - they interpret patterns across multiple dimensions, providing security teams with prioritized, contextualized alerts. This depth of analysis would require impractical human resources to replicate manually.
Improved Incident Response
Automated response protocols execute containment measures within moments of detection, significantly shrinking the window of exposure. These systems follow predefined playbooks while adapting to the specific characteristics of each incident. This combination of speed and precision is critical for minimizing operational impact during security events.
Scalability and Adaptability
As organizations grow, their security solutions must scale accordingly. AI-driven systems expand effortlessly to handle increased data volumes and more complex infrastructures. Their learning capabilities ensure they remain effective as both the protected environment and threat landscape evolve.
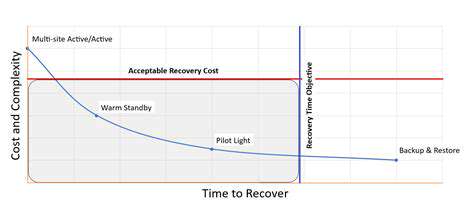
Cost-Effectiveness of Automation
While implementing advanced security automation requires initial investment, the long-term benefits outweigh the costs. Reduced reliance on manual monitoring lowers operational expenses, while preventing breaches avoids far greater financial impacts. The ROI becomes particularly evident when considering avoided regulatory fines, reputational damage, and customer churn associated with security incidents.