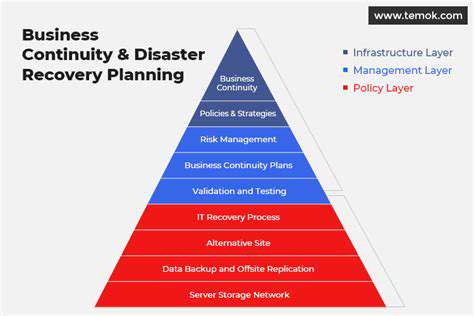
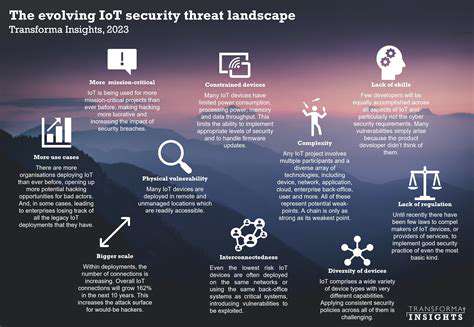
Security systems have evolved dramatically, transitioning from rudimentary physical barriers to complex networks of smart devices and processes. This transformation stems from escalating threat complexity and the demand for adaptive, forward-thinking security measures. At its heart, intelligent security thrives on real-time learning, adaptation, and response to emerging threats. Such proactive measures substantially lower breach risks while strengthening overall defenses.
Conventional security setups often depend on static rules, leaving them exposed to advanced attacks. In contrast, modern systems leverage machine learning and sophisticated algorithms to sift through massive datasets, detect patterns, and forecast potential threats. This foresight enables swifter, more precise reactions to newly identified vulnerabilities.
Key Features of Intelligent Security
One standout trait of these systems is their seamless integration of diverse security components—video surveillance, access controls, and intrusion detection—into a single cohesive platform. Unified monitoring offers a complete security overview and accelerates response efforts. Thorough data scrutiny remains vital for spotting irregularities and possible dangers.
Customizable security protocols represent another critical feature, adjusting to individual users or location-based risk evaluations. This tailored method cuts down on false alerts while optimizing protection, enhancing both security and user convenience. By adapting to specific scenarios, these systems can preemptively tackle unique environmental or behavioral risks.
The Impact on Security Operations
Automation lies at the core of intelligent security's operational benefits, handling routine tasks that once required manual intervention. This shift allows personnel to concentrate on higher-level duties like incident investigation and strategic planning. Automated processes also minimize human mistakes, yielding more dependable security results.
Additionally, these systems produce comprehensive analytics, offering invaluable perspectives on security trends. Such data-driven insights facilitate ongoing protocol refinements, resulting in stronger, more flexible security frameworks. Real-time information empowers security teams to make judicious, proactive decisions.
Future Trends in Intelligent Security
Looking ahead, intelligent security systems appear poised for significant growth, fueled by ongoing AI and machine learning breakthroughs. AI-driven threat identification and predictive analytics are set to redefine security approaches. Emerging integrations with blockchain and IoT technologies promise further security enhancements.
Growing cybersecurity awareness initiatives will likely complement these technological advances. Combining educated users with smart systems creates a multi-layered defense strategy where human insight and digital safeguards work in concert against potential threats.
Enhanced User and Entity Behavior Analytics (UEBA)

User Engagement Metrics
Evaluating platform effectiveness hinges on understanding user engagement. Metrics like visit duration, frequency, and user actions provide crucial behavioral insights. Longitudinal tracking reveals evolving interaction patterns, spotlighting both strengths and improvement areas. For instance, consistently brief sessions might indicate unengaging content, prompting targeted enhancements.
Entity Interaction Patterns
How users engage with specific system components—products, services, or resources—offers equally valuable intelligence. These interaction frequencies highlight which elements resonate most with users. Such understanding enables personalized experiences and curated content recommendations that boost engagement.
User-Entity Relationship Analysis
Moving beyond basic interaction counts, deeper analysis explores user motivations, goals, and contextual needs through demographic data, purchase histories, and other relevant metrics.
Personalized Recommendations and Content Curation
Behavioral data fuels customized suggestions and tailored content strategies. By aligning recommendations with proven user preferences, platforms dramatically enhance satisfaction and interaction quality. This precision-engineered approach delivers more meaningful user experiences.
Predictive Modeling and Future Trends
Historical behavior analysis enables predictive modeling that anticipates user needs. Forward-looking platforms can thus prepare relevant offerings before users explicitly demand them. Such proactive adaptation proves essential for maintaining competitive advantage.
Performance Metrics and Evaluation
Behavioral insights must integrate with broader performance assessments. Tracking KPIs related to engagement, satisfaction, and conversions ensures continuous optimization. Regular metric reviews verify whether platform modifications successfully enhance user value.
Roasting transforms ingredients through controlled heat exposure, typically in an oven, to create that perfect crisp exterior and deep flavor. The secret lies in matching temperatures to ingredients. Poultry demands higher heat to ensure safety and texture, while root vegetables thrive at lower temperatures to preserve their earthy sweetness. This careful dance with heat makes all the difference between mediocre and magnificent results.