The Proliferation of IoT Devices
The Internet of Things (IoT) has exploded in recent years, connecting everything from smart refrigerators to industrial machinery. This proliferation has created an enormous and ever-expanding attack surface, a vast network of interconnected devices with varying degrees of security. Many manufacturers prioritize speed and cost over robust security features, leading to a significant vulnerability gap that hackers readily exploit. This rapid growth has outpaced the development of effective security protocols, leaving countless devices susceptible to compromise.
The sheer volume of these devices poses a significant challenge. Managing security patches and updates across a constantly growing ecosystem is a daunting task. This makes it difficult to identify and address vulnerabilities before they are exploited, creating a constant race against attackers.
The Variety of Vulnerable Devices
The range of IoT devices is incredibly diverse, from consumer-grade smart home appliances to critical infrastructure components. Each device type presents unique security challenges. Smartwatches, for instance, may store personal data, making them targets for identity theft. Industrial control systems (ICS) in manufacturing and utilities can be manipulated, potentially causing widespread damage and disruption. The sheer variety necessitates a tailored security approach for each device type.
The Human Element in IoT Security
While technical vulnerabilities are a major concern, the human element plays a critical role in the security of IoT devices. Poorly configured devices, weak passwords, and a lack of user awareness contribute to breaches. Users often prioritize convenience over security, accepting default settings or failing to regularly update their devices. This human factor significantly amplifies the attack surface.
This human element is particularly critical in business settings, where employees may be less aware of the potential dangers or lack the training to properly secure their devices. This makes educating users and promoting security best practices essential to mitigating risk.
Exploiting Weaknesses in Network Design
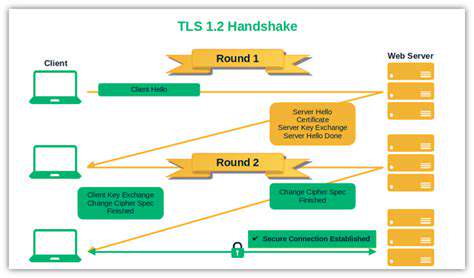
The way IoT devices are networked often contributes to security vulnerabilities. Many IoT networks lack proper security measures like firewalls and intrusion detection systems. This exposes the entire network to potential attacks. Furthermore, devices may connect to unsecured networks, making them vulnerable to eavesdropping and unauthorized access. Addressing network design weaknesses is crucial for bolstering overall security.
The Challenge of Patching and Updating
Maintaining security in this constantly evolving landscape requires robust patch and update mechanisms. However, many IoT devices struggle to receive timely updates, leaving them vulnerable to known exploits. This is often due to the complex and fragmented nature of the IoT ecosystem and the difficulty in maintaining compatibility across various device types. Manufacturers may not prioritize updates, or the devices themselves may lack the necessary processing power to handle them.
The Need for Improved Security Protocols
A fundamental shift in the way IoT devices are designed and deployed is needed to address the expanding attack surface. This includes incorporating robust security features from the design stage, prioritizing regular updates, and promoting user awareness about security best practices. The industry needs to collaborate on developing standardized security protocols and best practices to ensure that all devices meet a minimum security threshold. Ultimately, a more comprehensive and proactive approach to IoT security is crucial for mitigating the risks and ensuring the continued functionality and safety of these interconnected systems.
Default Credentials and Hardcoded Passwords: A Recipe for Disaster
Understanding the Risks
Default credentials and hardcoded passwords are a significant security vulnerability in Internet of Things (IoT) devices. These pre-configured login details, often readily available online or in device documentation, make it incredibly easy for attackers to gain unauthorized access. Without proper authentication measures, attackers can compromise the device, potentially gaining control over its functionalities and using it for malicious purposes, such as launching denial-of-service attacks or stealing sensitive data.
The Prevalence of the Problem
Many IoT devices are manufactured with default credentials, often as a convenience for initial setup. This ease of use, however, comes at a steep price. Manufacturers often fail to adequately address the security implications, resulting in a widespread vulnerability affecting countless devices across various sectors. The lack of security awareness and often rushed development cycles contribute to this pervasive problem.
The Impact on IoT Systems
Once attackers gain access to an IoT device using default credentials, they can potentially compromise the entire connected network. This can lead to significant disruptions, data breaches, and financial losses. For instance, a compromised smart home system could be used to remotely control appliances, potentially causing damage or enabling unauthorized access to sensitive information. In industrial settings, compromised devices could lead to critical process malfunctions and safety hazards.
Mitigation Strategies
Implementing robust security measures, including strong, unique passwords and multi-factor authentication, is crucial to mitigate the risks associated with default credentials and hardcoded passwords. Device manufacturers should prioritize security throughout the design and development process, implementing default credentials that are strong and not easily guessed. Regular security updates and patches are also essential to address known vulnerabilities and protect against emerging threats.
The Importance of Regular Updates
Regular software updates are vital to address security vulnerabilities that may arise. These updates often include patches for known exploits that could be leveraged by attackers using default credentials. Users should enable automatic updates whenever possible, ensuring that their IoT devices have the latest security protections. This proactive approach can significantly reduce the risk of successful attacks.
The Role of User Education
Educating users about the importance of strong passwords and the risks associated with default credentials is also critical. Users need to understand the potential consequences of using weak passwords or failing to change default credentials. Clear instructions and guidance from manufacturers on how to secure their devices can empower users to take proactive steps to enhance security.