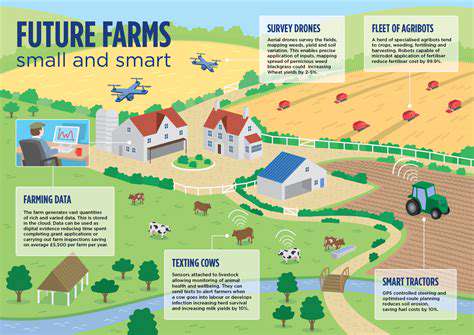
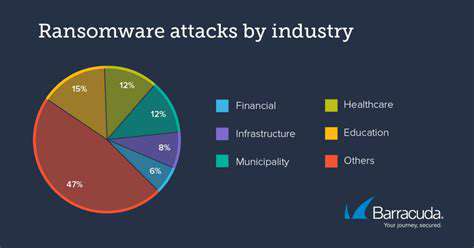
Modern agricultural practices are being transformed by smart farming technologies like IoT devices and data analytics platforms. While these innovations boost efficiency, reduce waste, and increase yields, they also create new security challenges that demand immediate attention. The interconnected nature of these systems makes them vulnerable to attacks that could disrupt global food supplies. What was once considered optional protection is now a fundamental requirement for agricultural sustainability and profitability.
Agricultural IoT systems face threats ranging from operational disruptions to sophisticated cyberattacks that manipulate critical data. Such breaches could lead to catastrophic financial damage and compromise food safety standards across entire regions.
Vulnerabilities in Current Agricultural Systems
Many existing agricultural IoT implementations suffer from inadequate security measures, often due to limited awareness or budget constraints during development. Compounding these issues are outdated equipment, irregular software maintenance, and insufficient staff training, all of which create dangerous security loopholes.
The complexity of modern farm technology presents another challenge. Managing security across diverse devices - from soil sensors to automated irrigation systems - requires sophisticated protection strategies that many operations currently lack.
Data Protection in Agricultural Technology
Precision agriculture depends on collecting and analyzing massive datasets, including weather information, soil conditions, and livestock health metrics. Safeguarding this sensitive information against unauthorized access or manipulation is absolutely critical, as breaches could destroy farmer trust in technology while causing substantial financial and reputational harm.
Effective data security requires multiple protective layers, including advanced encryption, strict access controls, and comprehensive monitoring systems to ensure information remains confidential and reliable.
Advancing Security Standards in Agriculture
The agricultural sector must adopt stronger security protocols across all technological applications. This includes developing more resilient hardware, implementing military-grade encryption, and establishing clear security policies. Regular system updates and thorough vulnerability testing should become standard practice to address emerging threats effectively.
Educating farmers and technical staff about cybersecurity risks and best practices is equally important. Industry-wide collaboration between growers, technology providers, and government agencies will be essential for developing practical, effective security solutions.
Collaborative Security for Future Farming
Sustainable smart farming depends on successfully integrating advanced technology with robust security measures. A cooperative approach involving all stakeholders - from researchers to policymakers - will be necessary to address evolving cybersecurity challenges.
Continuous system monitoring, rigorous stress testing, and rapid incident response protocols must become fundamental components of agricultural technology management. These proactive measures will help maintain system integrity and support the long-term success of precision agriculture initiatives worldwide.
Identifying Potential Threats to Agricultural IoT Systems
Recognizing External Risks
External threats to agricultural operations frequently originate from uncontrollable factors like economic fluctuations or extreme weather events. Climate change has made weather patterns increasingly unpredictable, creating new challenges for farm operations and food security worldwide.
Geopolitical conflicts and trade disputes can also disrupt global agricultural markets and supply chains unexpectedly. Farmers must develop flexible contingency plans to maintain operations during such disruptions.
Competitive Market Pressures
Agricultural businesses must continuously analyze their competitive environment, including monitoring rival operations' technological adoption and production strategies. New market entrants often introduce innovative techniques that can rapidly change industry standards and consumer expectations.
Understanding competitor weaknesses helps identify opportunities, while recognizing their strengths allows for better strategic planning in an increasingly technology-driven agricultural sector.
Regulatory Compliance Challenges
Changing government policies, particularly regarding environmental protection and food safety, can significantly impact farming operations. Non-compliance with new regulations can result in severe penalties and damage to brand reputation that takes years to repair.
Farmers must stay informed about potential policy changes in areas like water usage, pesticide application, and labor laws to avoid costly violations and operational disruptions.
Technological Disruption in Agriculture
Emerging technologies like AI-driven automation and blockchain tracking systems are revolutionizing farming practices. Operations that fail to adopt relevant innovations risk becoming obsolete as consumer preferences shift toward tech-enabled sustainable agriculture.
The rapid pace of agricultural technology development requires continuous evaluation and strategic investment to maintain competitiveness in global markets.
Changing Consumer Expectations
Modern consumers increasingly demand transparency about food origins, production methods, and environmental impact. Farms that cannot demonstrate sustainable practices may lose market share to competitors with stronger environmental credentials.
Understanding these evolving preferences allows agricultural businesses to adapt their operations and marketing strategies to meet changing consumer expectations.
Internal Operational Vulnerabilities
Many agricultural operations overlook internal risks like equipment failures, data management errors, or employee mistakes. Implementing rigorous operational protocols and staff training programs can significantly reduce these risks and improve overall efficiency.
Regular audits of internal processes help identify potential weaknesses before they cause operational disruptions or financial losses.