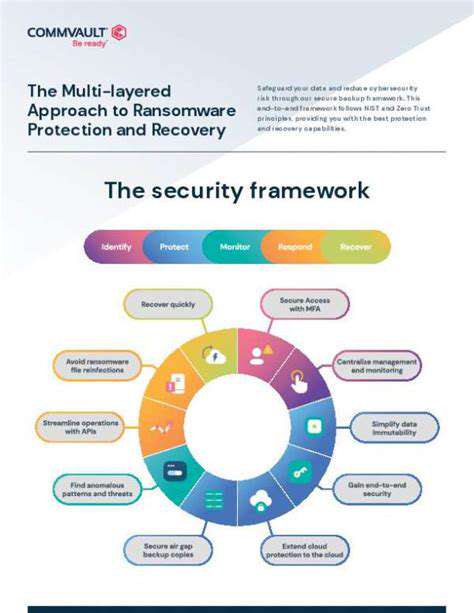
Developing and Implementing Mitigation Strategies

Developing Mitigation Strategies
Creating strong mitigation strategies is essential for tackling potential risks before they escalate. Organizations must conduct detailed threat assessments, pinpoint system vulnerabilities, and rank risks by their severity and probability. Comprehensive planning and analysis form the backbone of customized mitigation approaches that address unique organizational needs.
Identifying weak points requires examining every facet of operations, from technical infrastructure to employee protocols. A collaborative effort involving diverse stakeholders ensures no critical area is overlooked.
Implementing Mitigation Strategies
Rolling out these strategies demands meticulous coordination. Resources must be allocated wisely, staff trained thoroughly, and clear guidelines established. Execution quality directly determines whether mitigation efforts deliver their promised results.
Ongoing surveillance through regular audits maintains strategy effectiveness. These checkpoints reveal where adjustments are needed, keeping defenses responsive to evolving threats.
Prioritizing Mitigation Actions
Strategic resource allocation begins with risk prioritization. By assessing each threat's potential damage and occurrence probability, organizations can focus their efforts where they'll make the most significant impact first.
Cost-benefit analysis helps justify mitigation investments. Weighing implementation expenses against potential savings from risk avoidance ensures financially sound decisions.
Evaluating the Effectiveness of Mitigation
Continuous assessment through KPIs and incident analysis measures strategy performance. These evaluations spotlight vulnerabilities in current approaches, enabling timely refinements.
Quantitative metrics transform abstract security concepts into concrete data, supporting evidence-based policy adjustments.
Maintaining and Updating Mitigation Plans
Static defense strategies quickly become obsolete. Regular plan revisions ensure protections remain aligned with emerging threat landscapes. This requires constant monitoring of new vulnerabilities and attack vectors.
Cross-departmental collaboration during updates guarantees comprehensive protection. When all stakeholders contribute, mitigation plans reflect diverse operational realities.
Building a Culture of Risk Awareness and Continuous Improvement
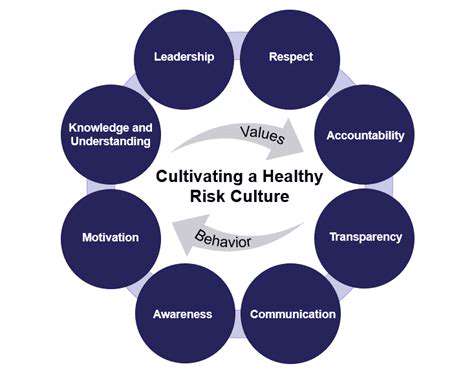
Understanding the Importance of Risk Awareness
True risk awareness transcends checklist compliance; it represents an organizational philosophy where every team member actively anticipates potential disruptions. This mindset shift creates enterprises that detect threats earlier and recover faster, turning risk management into competitive advantage.
Leadership must visibly champion risk awareness through consistent policies and resource allocation. When executives model vigilance, employees understand security isn't just an IT concern but everyone's responsibility.
Identifying and Assessing Potential Risks
Effective risk identification examines both internal operations and external pressures. Historical incident reviews combined with industry benchmarking reveal patterns that might otherwise go unnoticed.
Standardized assessment frameworks give all employees common language for evaluating threats. These tools democratize risk awareness across pay grades and departments.
Implementing Effective Risk Mitigation Strategies
Tailored countermeasures address specific organizational vulnerabilities. Documented procedures ensure consistency, while scheduled reviews maintain relevance as business conditions change.
Agility distinguishes proactive organizations. Those willing to overhaul strategies in response to new information build enduring resilience.
Communicating Risk Awareness Effectively
Transparent discussions about near-misses and successful interventions build collective security intelligence. Sharing these narratives transforms abstract risks into concrete lessons.
Multiple communication channels - from town halls to digital dashboards - keep risk consciousness alive in daily operations.
Training and Empowerment of Employees
Regular, evolving training programs arm staff with current threat knowledge. This investment creates human sensors throughout the organization, dramatically expanding defensive coverage.
A blame-free reporting culture is the hallmark of mature risk management. When employees trust their concerns will be addressed constructively, organizations gain early warning systems no technology can replicate.