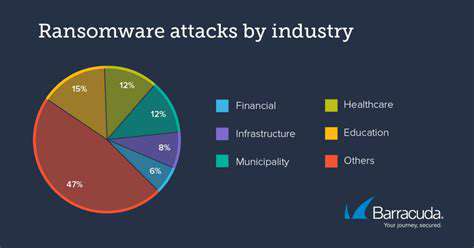
Modern cybersecurity strategies are undergoing a radical transformation with the adoption of Zero Trust architecture. Where traditional models operated on implicit trust within network perimeters, today's approach treats every access attempt as potentially hostile. This fundamental rethinking requires organizations to verify identities and permissions continuously, not just at initial login. By implementing stringent authentication protocols regardless of user location or network position, businesses can significantly shrink their vulnerable surface area.
Continuous monitoring forms the backbone of this strategy. Security teams now evaluate access requests in real-time, considering multiple contextual factors like device health, user behavior patterns, and current threat intelligence. This dynamic approach ensures that even previously authorized entities can be immediately restricted if their trust indicators deteriorate. Such vigilance proves essential against today's sophisticated cyber threats that constantly evolve to bypass conventional defenses.
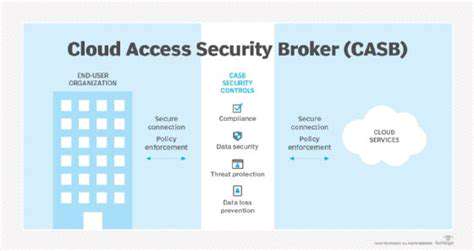
Cloud Access Security Brokers (CASBs): The Implementation Tool
Organizations embracing cloud infrastructure increasingly rely on Cloud Access Security Brokers to enforce Zero Trust principles. These solutions serve as critical gatekeepers, overseeing all cloud application interactions. By analyzing multiple security dimensions - from user credentials to application context - CASBs dynamically enforce access policies that protect sensitive organizational data.
Modern CASB platforms offer comprehensive security suites including:
- Precision access controls based on multiple verification factors
- Advanced data protection mechanisms
- Real-time threat identification and response systems
Enhancing Security Posture with Zero Trust and CASBs
The strategic combination of Zero Trust principles and CASB implementation creates a robust defensive framework. This dual approach ensures every access request undergoes rigorous validation while providing the tools to monitor and control cloud environments effectively. The result is a security posture that adapts dynamically to emerging threats while maintaining strict compliance with regulatory requirements.
Enterprises adopting this model benefit from:
- Reduced vulnerability to credential-based attacks
- Enhanced detection of suspicious activities
- Greater control over sensitive data movements
Key Benefits of Combining Zero Trust and CASBs
Zero Trust and Modern Security
The transition to Zero Trust models represents more than just a technical upgrade - it's a complete reimagining of organizational security philosophy. By eliminating default trust assumptions, companies create security environments where every access request must prove its legitimacy. This approach proves particularly valuable in today's distributed work environments where traditional perimeter defenses fall short.
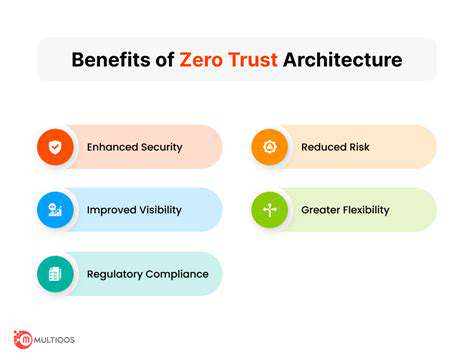
Enhanced Security Posture
Zero Trust's least-privilege approach minimizes potential damage from compromised credentials by strictly limiting access rights. Security teams gain the ability to rapidly isolate affected systems during incidents, significantly reducing breach impact and recovery time.
Improved Visibility and Control
Comprehensive monitoring capabilities provide security teams with real-time insights into network activities and user behaviors. This enhanced visibility enables faster detection of anomalies and more precise responses to potential threats.
Reduced Risk of Data Breaches
By implementing granular access controls, organizations can dramatically decrease the likelihood of successful data exfiltration attempts. This preventive strategy proves far more effective than traditional reactive security measures.
Increased Agility and Scalability
Modern Zero Trust implementations offer the flexibility to adapt security protocols as business needs evolve. This dynamic approach allows organizations to scale their operations without compromising security standards.
Beyond Basic Security: CASB's Role in Compliance and Governance
Beyond the Firewall: Expanding Security Horizons with CASB
Today's CASB solutions have evolved into sophisticated platforms that extend security monitoring and enforcement capabilities across diverse cloud environments. These tools provide essential visibility into data flows and user activities across multiple cloud services, filling critical gaps left by traditional perimeter defenses.
Compliance and Governance: CASB's Crucial Contribution
Modern regulatory frameworks demand rigorous data protection measures that CASBs are uniquely positioned to provide. Automated compliance tracking and reporting features simplify adherence to standards like GDPR and HIPAA, while continuous monitoring ensures ongoing compliance.
Data Loss Prevention (DLP) in the Cloud Era
Advanced CASB platforms integrate comprehensive DLP capabilities that:
- Classify sensitive data automatically
- Enforce contextual access policies
- Monitor data movements across cloud platforms
Future Trends and Integration with Other Security Tools
Zero Trust Architecture and Cloud Security
The cybersecurity landscape continues to evolve with Zero Trust principles becoming more sophisticated. Future implementations will likely incorporate:
- Dynamic risk scoring for access decisions
- Automated policy adjustments based on threat intelligence
- Tighter integration with cloud-native security tools
The Role of AI and Machine Learning
Emerging AI technologies are revolutionizing threat detection by:
- Identifying subtle behavioral anomalies
- Predicting potential attack vectors
- Automating complex security responses